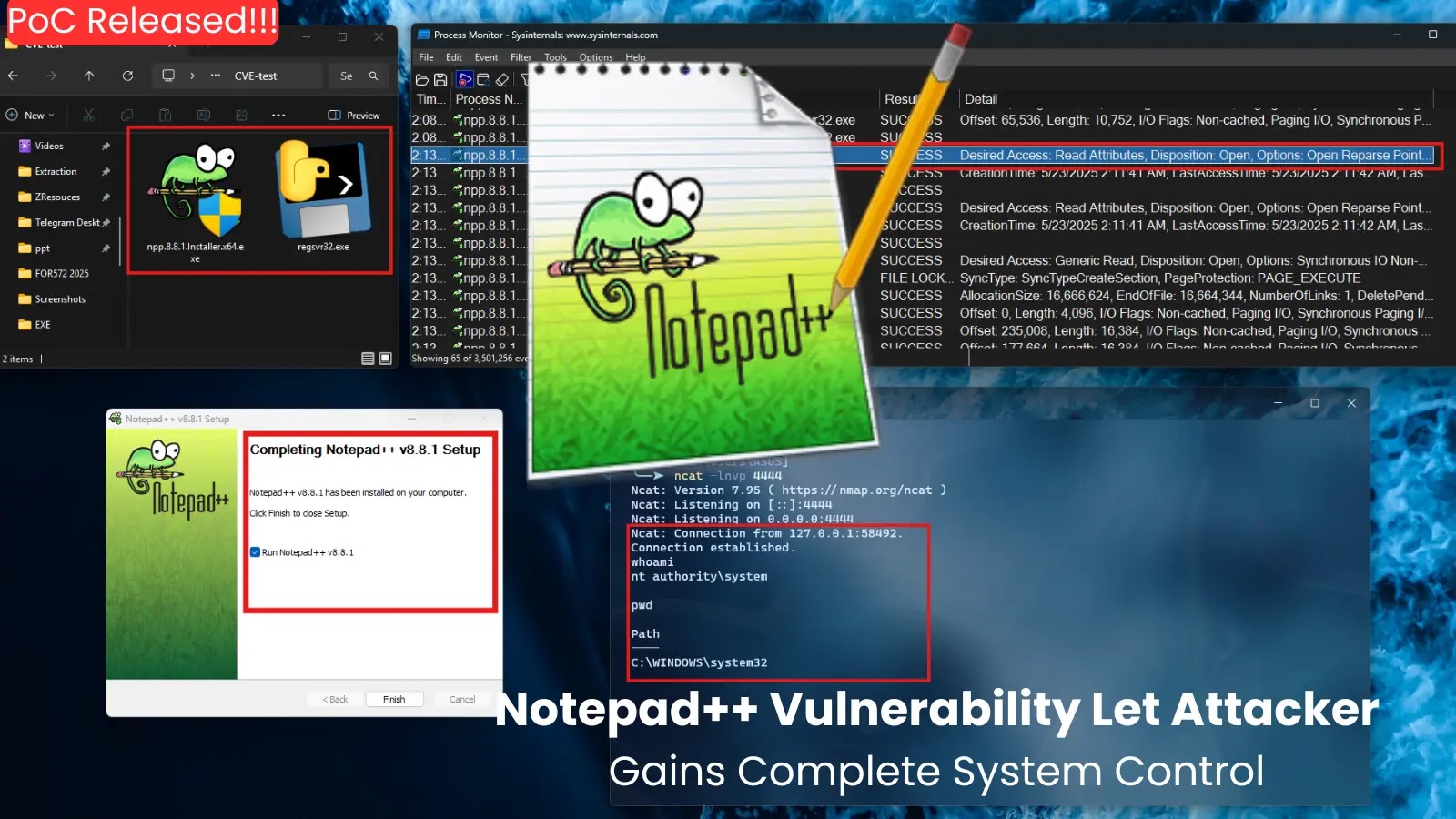
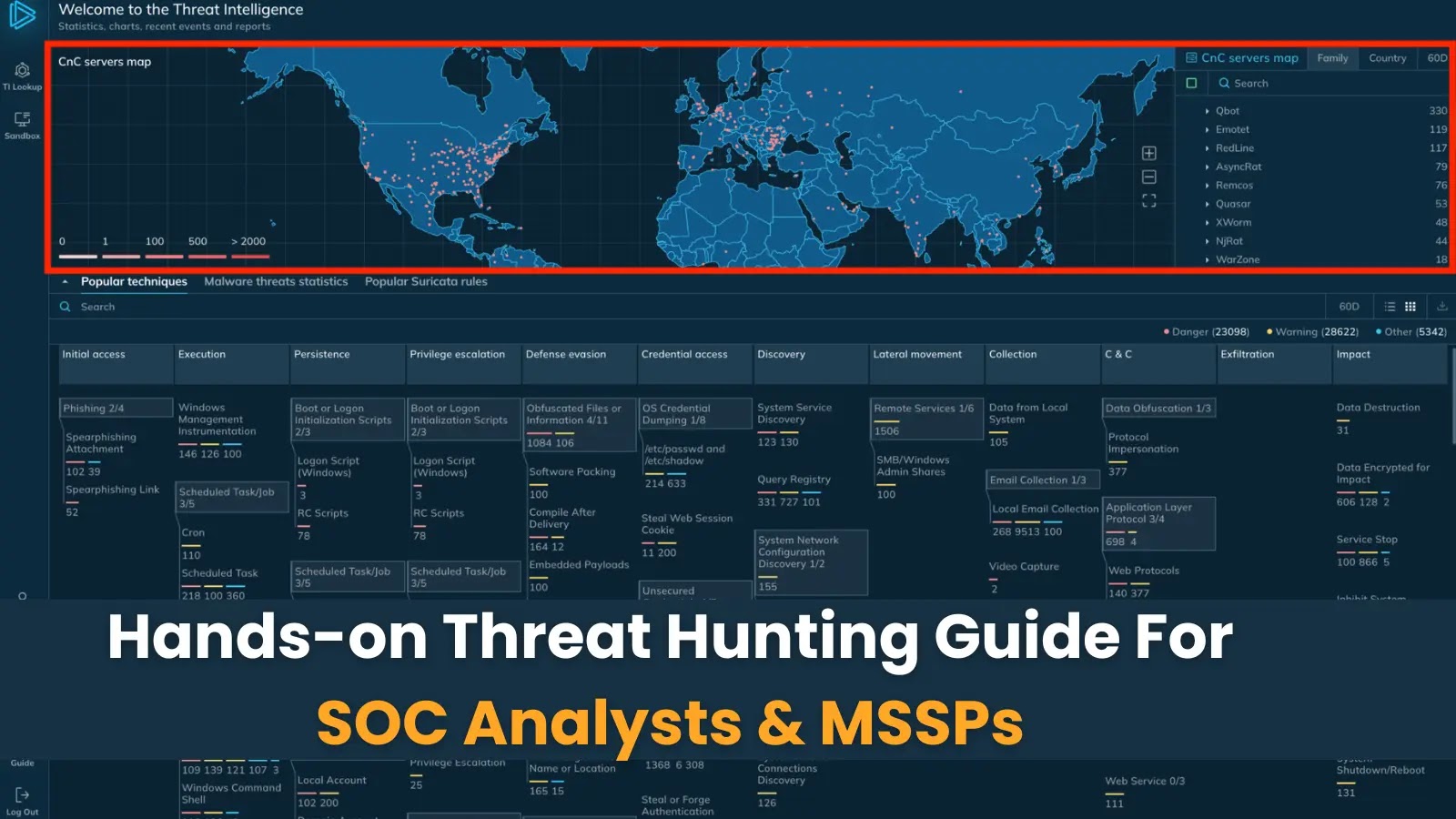
Month: June 2025

How to Disable Location Tracking on Apps
In today’s digital world, your privacy is more important than ever. With every app you download, there’s a chance it might track your location. But fear not! Disabling location tracking is easier than you think. This guide will walk you through the steps to take control of your personal information. After all, who wants their…