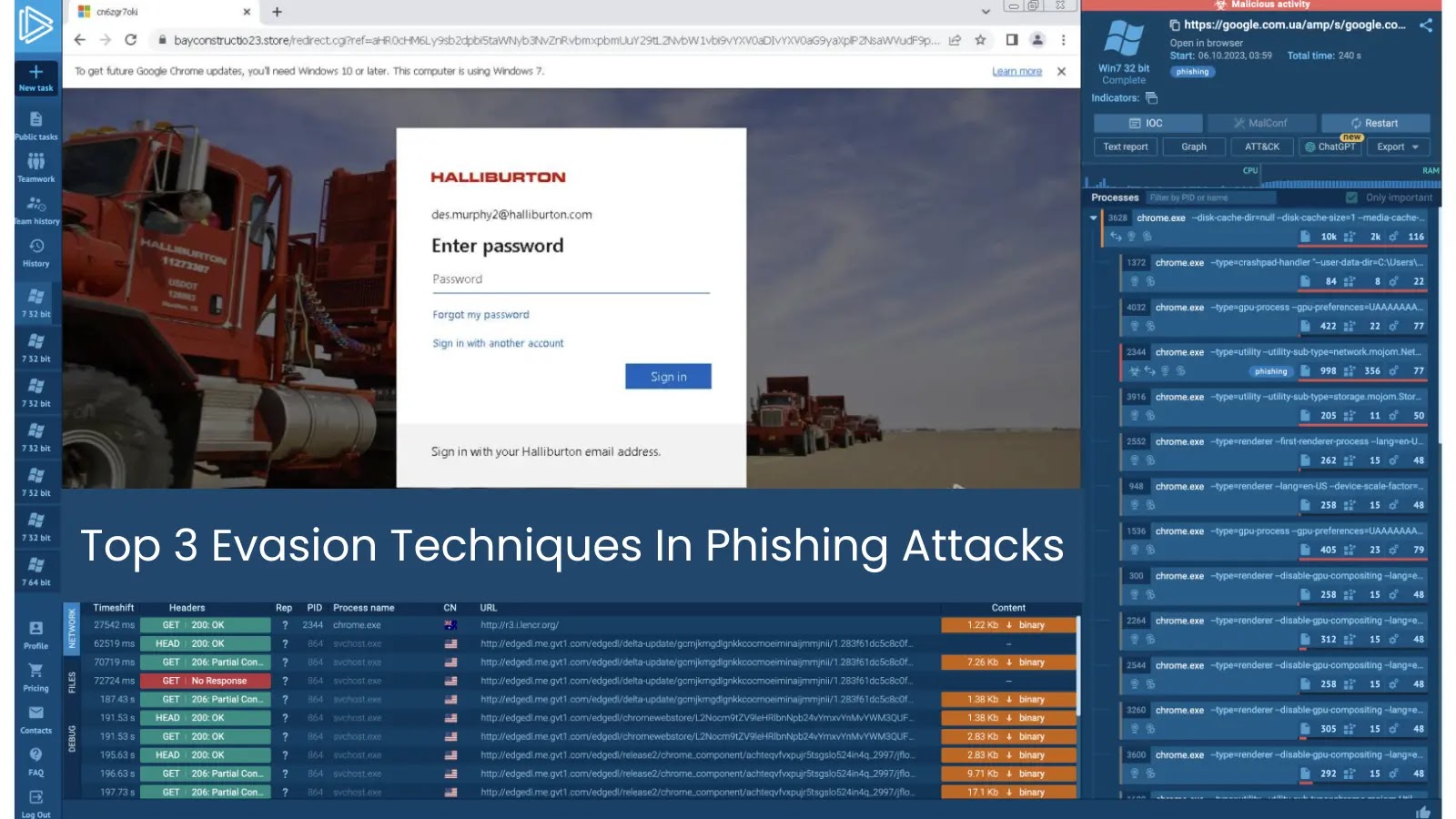
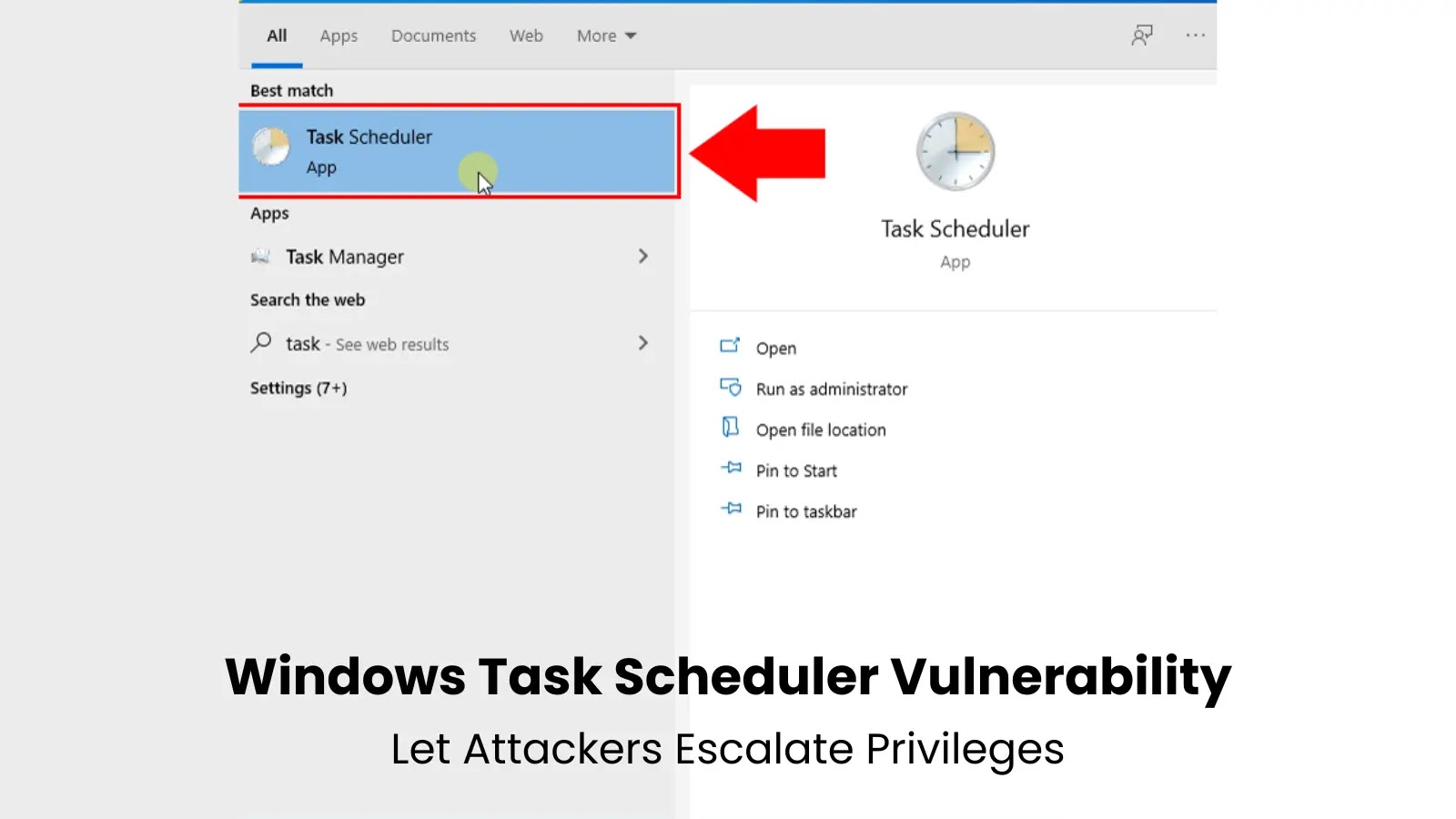
Month: June 2025

How to Configure Email SPF, DKIM, and DMARC
This article provides a comprehensive guide on configuring SPF, DKIM, and DMARC for email authentication, ensuring better deliverability and enhanced security against phishing and spoofing attacks. SPF (Sender Policy Framework) records are essential. They help prevent email spoofing by specifying which mail servers are allowed to send emails for your domain. Think of it as…