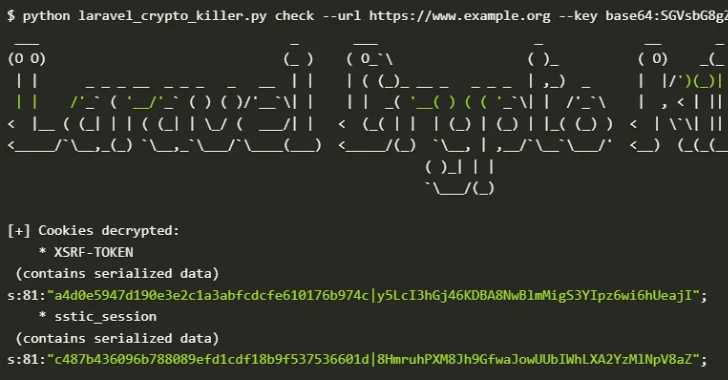
Month: July 2025

How to Monitor Application Logs for Security Events
In today’s digital landscape, monitoring application logs is more important than ever. Why? Because these logs provide a wealth of information about what’s happening in your systems. Think of application logs as the diary of your software. They record everything from user actions to system errors. By keeping an eye on them, you can spot…
Read More “How to Monitor Application Logs for Security Events” »