Month: September 2025

How to Use Sandboxing to Analyze Suspicious Files
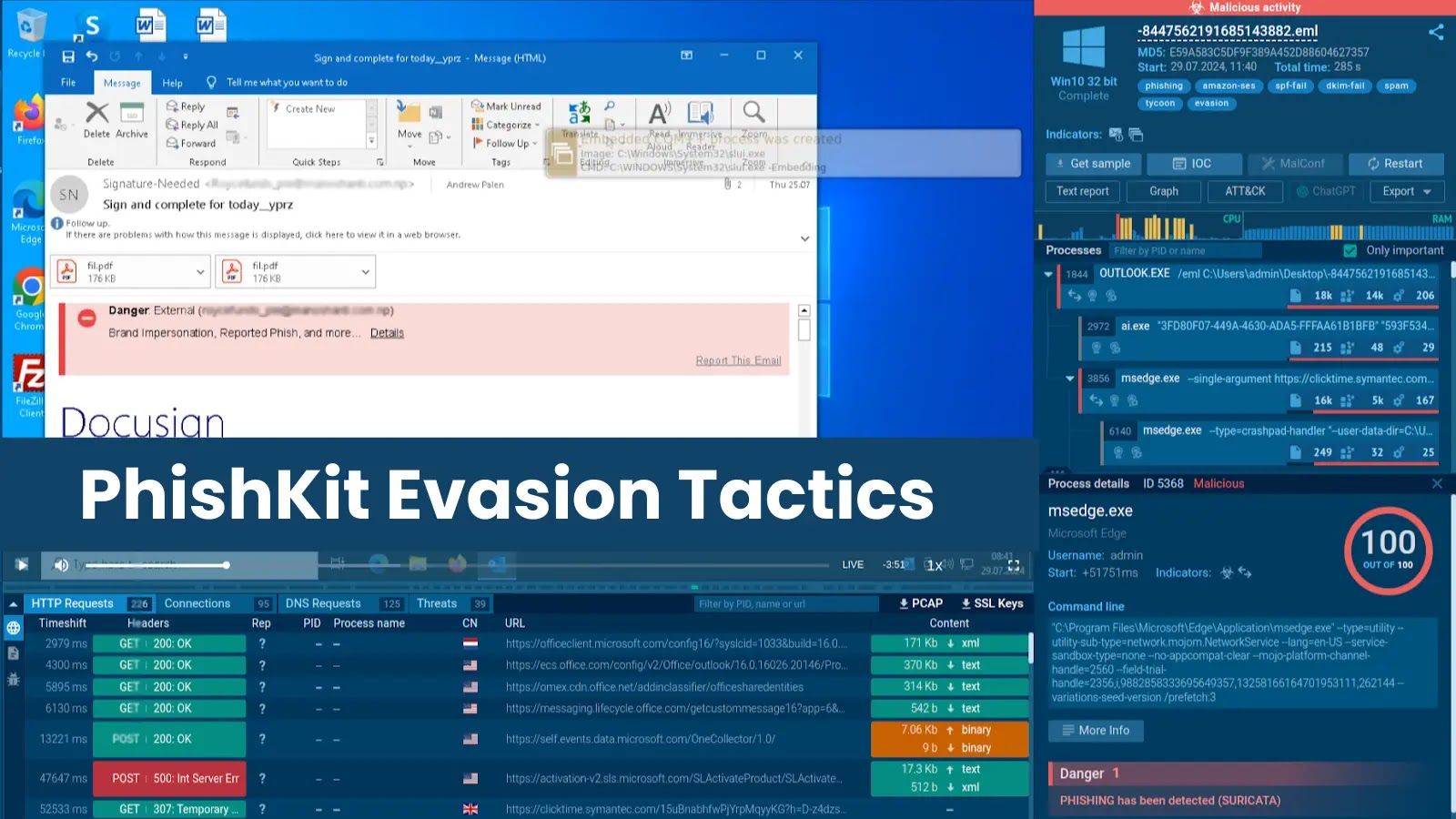
In today’s digital world, where threats lurk around every corner, understanding how to use sandboxing is essential. So, what exactly is sandboxing? Think of it as a protective bubble. It allows you to run programs or files in a controlled environment, ensuring they don’t harm your main system. Imagine letting a child play with a…
Read More “How to Use Sandboxing to Analyze Suspicious Files” »