A brand new proof-of-concept (PoC) instrument named Obex has been launched, providing a way to stop Endpoint Detection and Response (EDR) and different monitoring options’ dynamic-link libraries (DLLs) from loading into processes.
The instrument, created by a researcher often known as “dis0rder0x00,” is designed to dam specified DLLs each throughout the preliminary startup of a course of and at runtime, doubtlessly permitting malware or pink staff instruments to function with out being detected by safety software program.
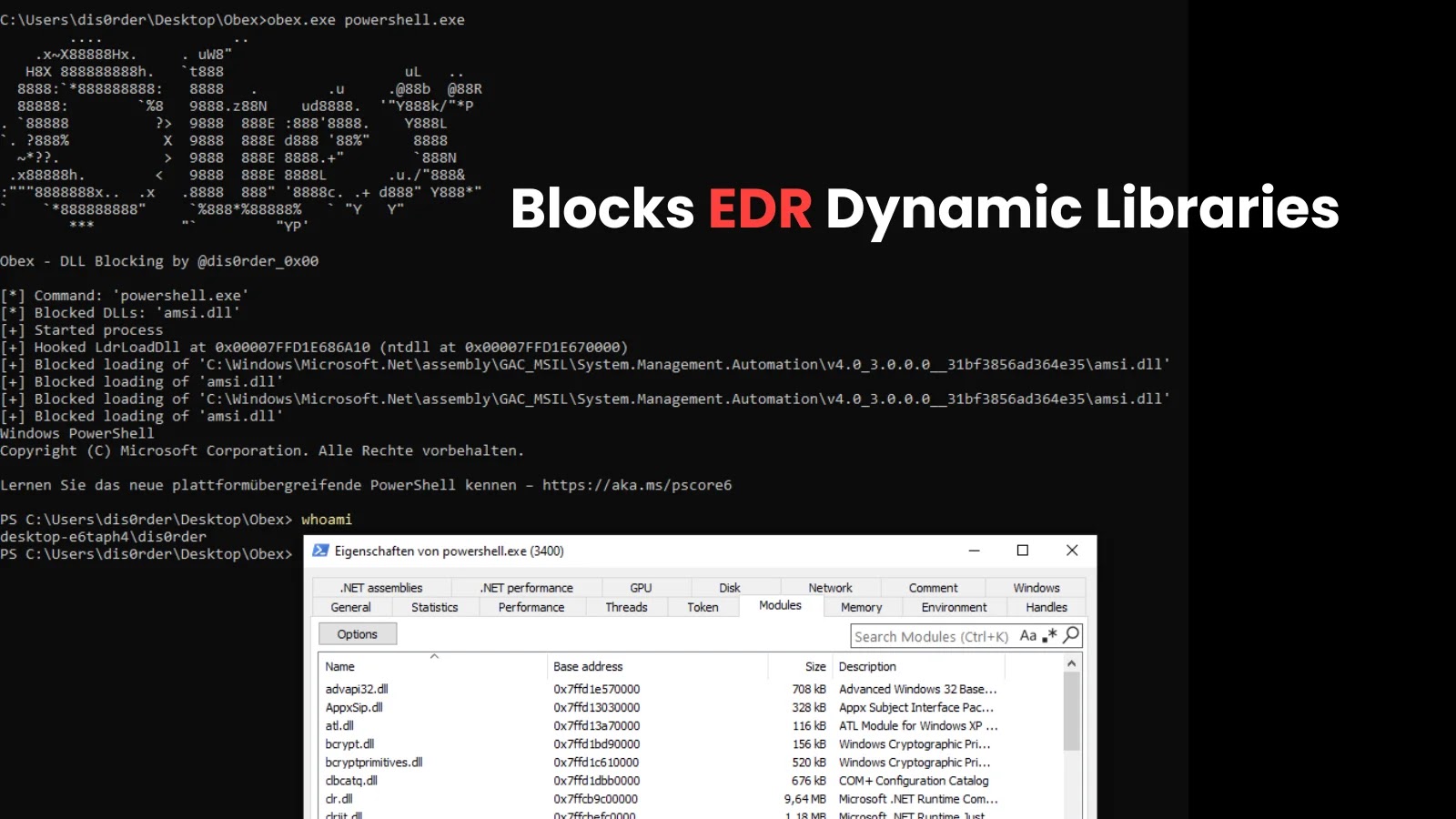
Obex features by launching a goal utility underneath its debug management. This enables it to intercept vital system operations. Particularly, it hooks the ntdll!LdrLoadDll operate, which is answerable for loading DLLs right into a course of.
When an utility makes an attempt to load a DLL, Obex intercepts the decision and checks the DLL’s title in opposition to a configurable blocklist.
If the DLL is on the record, the instrument simulates a failed load try, stopping the library from being injected into the method.
If the DLL is just not on the record, the loading course of is allowed to proceed as regular. This system successfully blinds safety instruments that depend on injecting their very own DLLs into processes to observe their habits.
The instrument is written in C and has no exterior dependencies, making it light-weight and moveable. By default, Obex is configured to dam amsi.dll, the library for the Antimalware Scan Interface, however customers can present a customized record of DLLs to dam.
The developer has made the instrument obtainable on GitHub, positioning it as a method for safety researchers to grasp and take a look at evasion strategies.
Safety options extensively use DLL injection to ascertain user-mode hooks for monitoring API calls and system habits. Instruments like Obex reveal strategies that can be utilized to bypass these defenses.
Whereas worthwhile for penetration testers and pink groups, such instruments additionally present defenders and safety distributors with necessary insights into evasion methods, serving to them to develop extra resilient detection and safety methods in opposition to refined threats.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.