Cybersecurity researchers are calling consideration to a nefarious marketing campaign focusing on WordPress websites to make malicious JavaScript injections which are designed to redirect customers to sketchy websites.
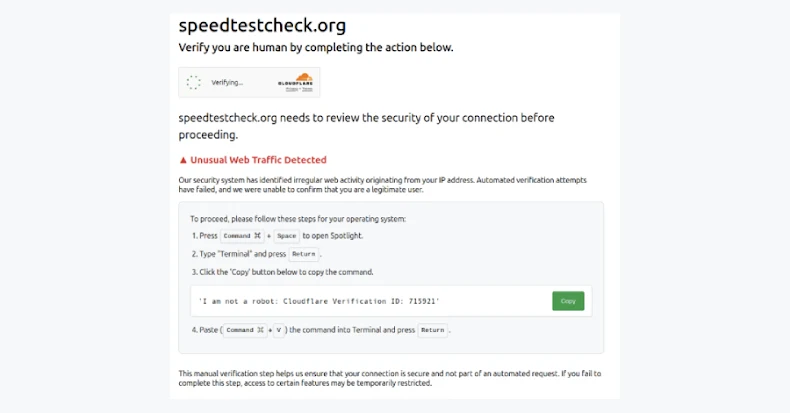
“Website guests get injected content material that was drive-by malware like pretend Cloudflare verification,” Sucuri researcher Puja Srivastava stated in an evaluation revealed final week.
The web site safety firm stated it started an investigation after one among its buyer’s WordPress websites served suspicious third-party JavaScript to website guests, finally discovering that the attackers launched malicious modifications to a theme-related file (“features.php”).
The code inserted into “features.php” incorporates references to Google Advertisements, probably in an try to evade detection. However, in actuality, it features as a distant loader by sending an HTTP POST request to the area “brazilc[.]com,” which, in flip, responds with a dynamic payload that features two parts –
A JavaScript file hosted on a distant server (“porsasystem[.]com”), which, as of writing, has been referenced on 17 web sites and comprises code to carry out website redirects
A bit of JavaScript code that creates a hidden, 1×1 pixel iframe, inside which it injects code that mimics reliable Cloudflare property like “cdn-cgi/challenge-platform/scripts/jsd/fundamental.js” – an API that is a core a part of its bot detection and problem platform
It is price noting that the area “porsasystem[.]com” has been flagged as a part of a site visitors distribution system (TDS) referred to as Kongtuke (aka 404 TDS, Chaya_002, LandUpdate808, and TAG-124).
Based on data shared by an account named “monitorsg” on Mastodon on September 19, 2025, the an infection chain begins with customers visiting a compromised website, ensuing within the execution of “porsasystem[.]com/6m9x.js,” which then results in “porsasystem[.]com/js.php” to finally take the victims to ClickFix-style pages for malware distribution.
The findings illustrate the necessity for securing WordPress websites and making certain that plugins, themes, and web site software program are stored up-to-date, implementing sturdy passwords, scanning the websites for anomalies and sudden administrator accounts created for sustaining persistent entry even after the malware is detected and eliminated.
Create ClickFix Pages Utilizing IUAM ClickFix Generator
The disclosure comes as Palo Alto Networks Unit 42 detailed a phishing package named IUAM ClickFix Generator that permits attackers to contaminate customers with malware by leveraging the ClickFix social engineering approach and provide you with customizable touchdown pages by mimicking browser verification challenges usually used to dam automated site visitors.
“This instrument permits menace actors to create extremely customizable phishing pages that mimic the challenge-response habits of a browser verification web page generally deployed by Content material Supply Networks (CDNs) and cloud safety suppliers to defend towards automated threats,” safety researcher Amer Elsad stated. “The spoofed interface is designed to look reliable to victims, rising the effectiveness of the lure.”
The bespoke phishing pages additionally include capabilities to govern the clipboard, a vital step within the ClickFix assault, in addition to detect the working system used with the intention to tailor the an infection sequence and serve suitable malware.
In at the least two completely different instances, menace actors have been detected utilizing pages generated utilizing the package to deploy data stealers equivalent to DeerStealer and Odyssey Stealer, the latter of which is designed to focus on Apple macOS techniques.
The emergence of the IUAM ClickFix Generator provides to a previous alert from Microsoft warning of an increase in industrial ClickFix builders on underground boards since late 2024. One other notable instance of a phishing package that has built-in the providing is Impression Options.
“The kits supply creation of touchdown pages with quite a lot of accessible lures, together with Cloudflare,” Microsoft famous again in August 2025. “In addition they supply development of malicious instructions that customers will paste into the Home windows Run dialog. These kits declare to ensure antivirus and internet safety bypass (some even promise that they will bypass Microsoft Defender SmartScreen), in addition to payload persistence.”
It goes with out saying that these instruments additional decrease the barrier to entry for cybercriminals, enabling them to mount subtle, multi-platform assaults at scale with out a lot effort or technical experience.
ClickFix Turns into Stealthy by way of Cache Smuggling
The findings additionally comply with the invention of a brand new marketing campaign that has innovated on the ClickFix assault components by using a sneaky approach known as cache smuggling to fly underneath the radar versus explicitly downloading any malicious recordsdata on the goal host.
“This marketing campaign differs from earlier ClickFix variants in that the malicious script doesn’t obtain any recordsdata or talk with the web,” Expel Principal Risk Researcher Marcus Hutchins stated. “That is achieved through the use of the browser’s cache to pre-emptively retailer arbitrary information onto the person’s machine.”
Within the assault documented by the cybersecurity firm, the ClickFix-themed web page masquerades as a Fortinet VPN Compliance Checker, utilizing FileFix techniques to deceive customers into launching the Home windows File Explorer and pasting a malicious command into the handle bar to set off the execution of the payload.
The invisible command is designed to run a PowerShell script by way of conhost.exe. What makes the script stand aside is that it doesn’t obtain any further malware or talk with an attacker-controlled server. As an alternative, it executes an obfuscated payload that passes off as a JPEG picture and is already cached by the browser when the person lands on the phishing web page.
“Neither the net web page nor the PowerShell script explicitly downloads any recordsdata,” Hutchins defined. “By merely letting the browser cache the pretend ‘picture,’ the malware is ready to get a complete zip file onto the native system with out the PowerShell command needing to make any internet requests.”
“The implications of this method are regarding, as cache smuggling could supply a method to evade protections that will in any other case catch malicious recordsdata as they’re downloaded and executed. An innocuous-looking ‘picture/jpeg’ file is downloaded, solely to have its contents extracted after which executed by way of a PowerShell command hidden in a ClickFix phishing lure.”