A brand new risk group calling itself Crimson Collective has emerged as a big cybersecurity concern, concentrating on Amazon Internet Companies (AWS) cloud environments with refined information exfiltration and extortion campaigns.
The group has just lately claimed duty for attacking Crimson Hat, asserting they efficiently compromised and stole non-public repositories from Crimson Hat’s GitLab infrastructure.
This improvement represents a regarding escalation in cloud-focused cybercrime, highlighting the evolving panorama of threats going through organizations working in cloud environments.
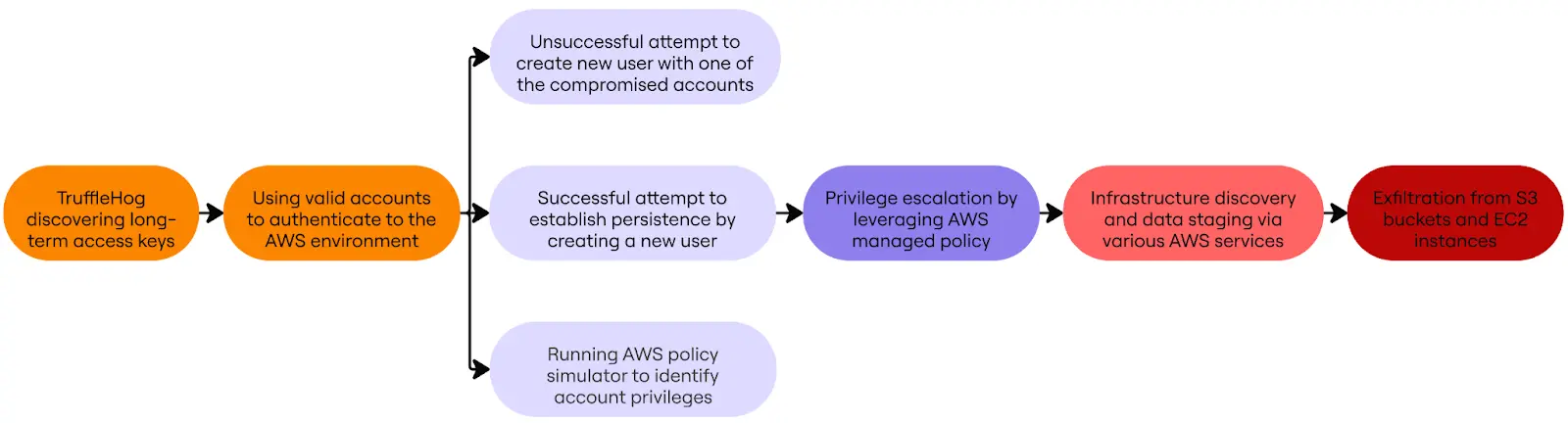
The Crimson Collective employs a methodical strategy to breach AWS infrastructure, starting with the exploitation of leaked long-term entry keys earlier than escalating privileges by way of IAM account manipulation.
Their operations reveal superior information of AWS providers and safety configurations, enabling them to navigate advanced cloud architectures whereas sustaining persistence throughout compromised environments.
The group’s actions have been focused on accumulating and exfiltrating databases, mission repositories, and different beneficial organizational information, inserting each company mental property and buyer info at important threat.
Over latest weeks, safety researchers have documented elevated exercise from this risk actor throughout a number of AWS environments, with documented circumstances occurring all through September.
The group operates from a number of IP addresses and maintains presence throughout a number of compromised accounts throughout the identical goal setting, suggesting a coordinated multi-operator construction.
Diagram of the assault (Supply – Rapid7)
Their extortion notes reference themselves utilizing plural pronouns, indicating a number of people collaborate in these operations, although the exact composition and construction of the group stays unclear.
Rapid7 analysts recognized the malware and its operational patterns by way of complete evaluation of CloudTrail logs and behavioral indicators throughout affected environments.
Their analysis revealed that Crimson Collective constantly employs the open-source instrument TruffleHog as their main technique for locating compromised AWS credentials in code repositories and storage places.
Technical Exploitation Strategies
The group’s technical methodology facilities on leveraging TruffleHog, a official safety instrument designed to establish uncovered credentials in numerous storage places.
When TruffleHog discovers legitimate AWS credentials, it authenticates utilizing the GetCallerIdentity API name to confirm credential validity.
Evaluation of CloudTrail logs constantly exhibits the TruffleHog consumer agent because the preliminary indicator throughout all compromised accounts, offering safety groups with a transparent detection alternative.
Following profitable credential validation, Crimson Collective establishes persistence by way of systematic consumer creation and privilege escalation.
They execute CreateUser API calls adopted by CreateLoginProfile to ascertain password authentication, then generate further entry keys utilizing CreateAccessKey calls.
The group makes an attempt these persistence mechanisms throughout each compromised account, although accounts missing adequate privileges are both deserted or subjected to SimulatePrincipalPolicy calls to evaluate out there permissions.
When profitable in creating new customers, the risk actors instantly escalate privileges by attaching the arn:aws:iam::aws:coverage/AdministratorAccess coverage by way of AttachUserPolicy API calls.
This AWS-managed coverage grants complete entry to all AWS providers and assets, offering attackers with unrestricted management over the compromised setting for subsequent information exfiltration operations.
Comply with us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates, Set CSN as a Most well-liked Supply in Google.