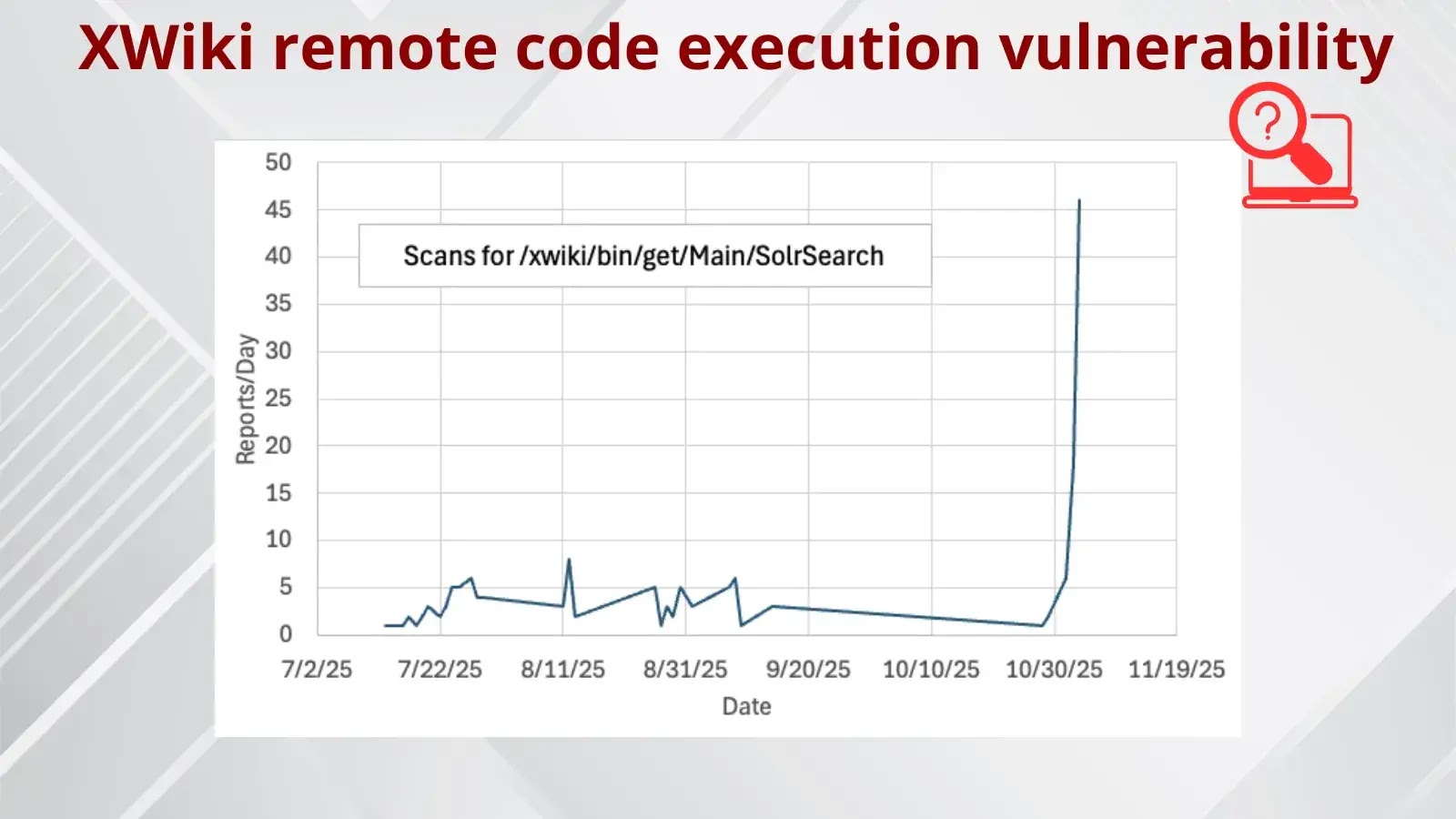
Oracle has disclosed a vital vulnerability in its E-Enterprise Suite that permits unauthenticated attackers to remotely entry delicate information, elevating alarms for enterprises counting on the platform for core operations.
Tracked as CVE-2025-61884, the flaw impacts the Oracle Configurator part and was detailed in a safety alert launched on October 11, 2025.
This comes simply days after one other exploited E-Enterprise Suite vulnerability, CVE-2025-61882, highlighting ongoing safety challenges in Oracle’s enterprise useful resource planning software program.
The difficulty permits hackers to bypass authentication over HTTP, probably exposing configuration information vital to enterprise processes like finance and provide chain administration.
Oracle E-Enterprise Suite RCE Vulnerability
CVE-2025-61884 resides within the Runtime UI of Oracle Configurator, a module used for managing product and repair configurations inside E-Enterprise Suite.
Attackers with community entry can exploit this flaw with out credentials, resulting in unauthorized information retrieval or enumeration. The vulnerability stems from an authentication bypass mechanism, although particular technical particulars like affected endpoints stay undisclosed to stop widespread abuse.
Oracle charges it with a CVSS 3.1 base rating of seven.5, classifying it as excessive severity as a result of its ease of exploitation. No credit are given to exterior researchers, suggesting inner discovery by Oracle’s safety group.
The next desk summarizes key elements of the vulnerability:
CVE IDAffected ComponentProtocolCVSS Base ScoreAttack VectorAttack ComplexityPrivileges RequiredUser InteractionScopeConfidentiality ImpactIntegrity ImpactAvailability ImpactSupported VersionsCVE-2025-61884Oracle Configurator (Runtime UI)HTTP7.5NetworkLowNoneNoneUnchangedHighNoneNone12.2.3-12.2.14
This structured breakdown underscores the distant, unauthenticated nature of the menace, making it accessible to any internet-facing deployment.
Profitable exploitation might grant hackers full entry to all Oracle Configurator information, together with delicate enterprise configurations that drive operational selections.
For organizations in sectors like manufacturing or retail, this implies publicity of proprietary fashions, pricing methods, and buyer particulars, probably resulting in aggressive disadvantages or regulatory violations.
The excessive confidentiality affect with out affecting integrity or availability positions it as a knowledge exfiltration vector relatively than a disruptive assault.
Given the latest exploitation of CVE-2025-61882 by ransomware teams like Cl0p, safety specialists warn that CVE-2025-61884 might comply with swimsuit, particularly as proof-of-concepts for comparable flaws flow into. Enterprises with unpatched E-Enterprise Suite situations face elevated dangers, significantly if uncovered to the general public web.
Mitigations
Oracle urges instant utility of the launched patches for variations 12.2.3 via 12.2.14, obtainable by way of the Safety Alert program for supported releases below Premier or Prolonged Assist.
Clients on older variations ought to improve to maintained branches, as earlier releases like 12.1.3 can also be weak regardless of missing testing.
Further defenses embody community segmentation to restrict HTTP entry to the Configurator UI and monitoring for anomalous requests.
Oracle’s advisory offers detailed patch directions via help paperwork, emphasizing the Lifetime Assist Coverage for ongoing safety.
Whereas no energetic exploitation has been confirmed for this CVE, the sample of fast E-Enterprise Suite assaults calls for swift motion to safeguard delicate assets.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.