Might 21, 2025Ravie LakshmananMalware / Synthetic Intelligence
Counterfeit Fb pages and sponsored adverts on the social media platform are being employed to direct customers to pretend web sites masquerading as Kling AI with the aim of tricking victims into downloading malware.
Kling AI is a man-made intelligence (AI)-powered platform to synthesize photos and movies from textual content and picture prompts. Launched in June 2024, it is developed by Kuaishou Expertise, which is headquartered in Beijing, China. As of April 2025, the service has a person base of greater than 22 million, per information from the corporate.
“The assault used pretend Fb pages and adverts to distribute a malicious file which finally led to the execution of a distant entry Trojan (RAT), granting attackers distant management of the sufferer’s system and the power to steal delicate information,” Verify Level mentioned.
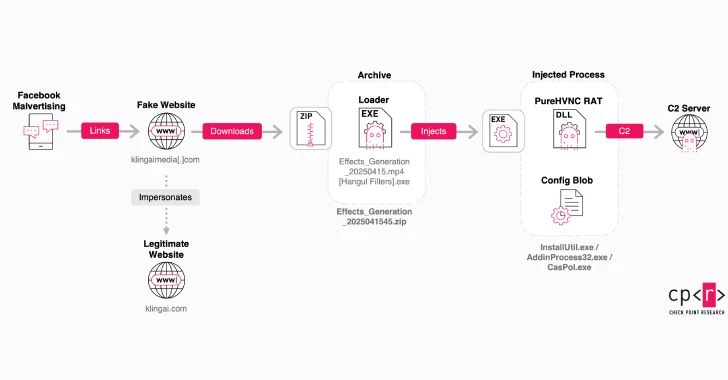
First detected in early 2025, the marketing campaign leads unsuspecting customers to a spoofed web site similar to klingaimedia[.]com or klingaistudio[.]com, the place they’re requested to create AI-generated photos or movies straight within the browser.
Nevertheless, the web site doesn’t generate the multimedia rely as marketed. Fairly, it provides the choice to a purported picture or video that, in actuality, is a malicious Home windows executable hidden utilizing double extensions and Hangul Filler (0xE3 0x85 0xA4) characters.
The payload is included in a ZIP archive and acts as a loader to launch a distant entry trojan and a stealer that then establishes contact with a command-and-control (C2) server and exfiltrates browser-stored credentials, session tokens, and different delicate information.
The loader, in addition to monitoring for evaluation instruments similar to Wireshark, OllyDbg, Procmon, ProcExp, PeStudio, and Fiddler, makes Home windows Registry adjustments to arrange persistence and launches the second-stage by injecting it right into a respectable system course of like “CasPol.exe” or “InstallUtil.exe” to evade detection.
The second-stage payload, obfuscated utilizing .NET Reactor, is the PureHVNC RAT that contacts a distant server (185.149.232[.]197) and comes with capabilities to steal information from a number of cryptocurrency pockets extensions put in on Chromium-based browsers. PureHVNC additionally adopts a plugin-based strategy to seize screenshots when window titles matching banks and wallets are opened.
Verify Level mentioned it recognized at least 70 promoted posts from pretend social media pages impersonating Kling AI. It is at present not clear who’s behind the marketing campaign, however proof gathered from the pretend web site’s internet web page and among the adverts present that they may very well be from Vietnam.
The usage of Fb malvertising methods to distribute stealer malware has been a tried-and-tested tactic of Vietnamese menace actors, who’ve been more and more capitalizing on the recognition of generative AI instruments to push malware.
Earlier this month, Morphisec revealed {that a} Vietnamese menace actor has been leveraging pretend AI-powered instruments as a lure to entice customers into downloading an data stealer malware dubbed Noodlophile.
“This marketing campaign, which impersonated Kling AI via pretend adverts and misleading web sites, demonstrates how menace actors are combining social engineering with superior malware to achieve entry to customers’ methods and private information,” Verify Level mentioned.
“With ways starting from file masquerading to distant entry and information theft, and indicators pointing to Vietnamese menace teams, this operation matches right into a broader development of more and more focused and complicated social media-based assaults.”
The event comes as The Wall Road Journal reported that Meta is battling an “epidemic of scams,” with cyber criminals flooding Fb and Instagram with varied sorts of scams starting from romance baiting to sketchy discount adverts to pretend giveaways. Lots of the rip-off pages are operated from China, Sri Lanka, Vietnam, and the Philippines, the report added.
In response to Remainder of World, phony job adverts on Telegram, Fb, and different social media are being more and more used to lure younger Indonesians and get trafficked to rip-off compounds in Southeast Asia, from the place they’re coerced into operating funding scams and defraud victims the world over.
Discovered this text fascinating? Observe us on Twitter and LinkedIn to learn extra unique content material we submit.