The Cybersecurity and Infrastructure Safety Company (CISA) issued an pressing alert on October 20, 2025, highlighting a extreme vulnerability CVE-2025-33073 in Microsoft’s Home windows SMB Shopper.
Dubbed an improper entry management flaw, this vulnerability tracked beneath CVE particulars but to be absolutely specified poses a big threat of privilege escalation for attackers worldwide.
As cyber threats escalate amid rising ransomware incidents, organizations are scrambling to patch their methods earlier than the November 10 deadline.
The vulnerability exploits the Server Message Block (SMB) protocol, a cornerstone of Home windows file sharing and community communications.
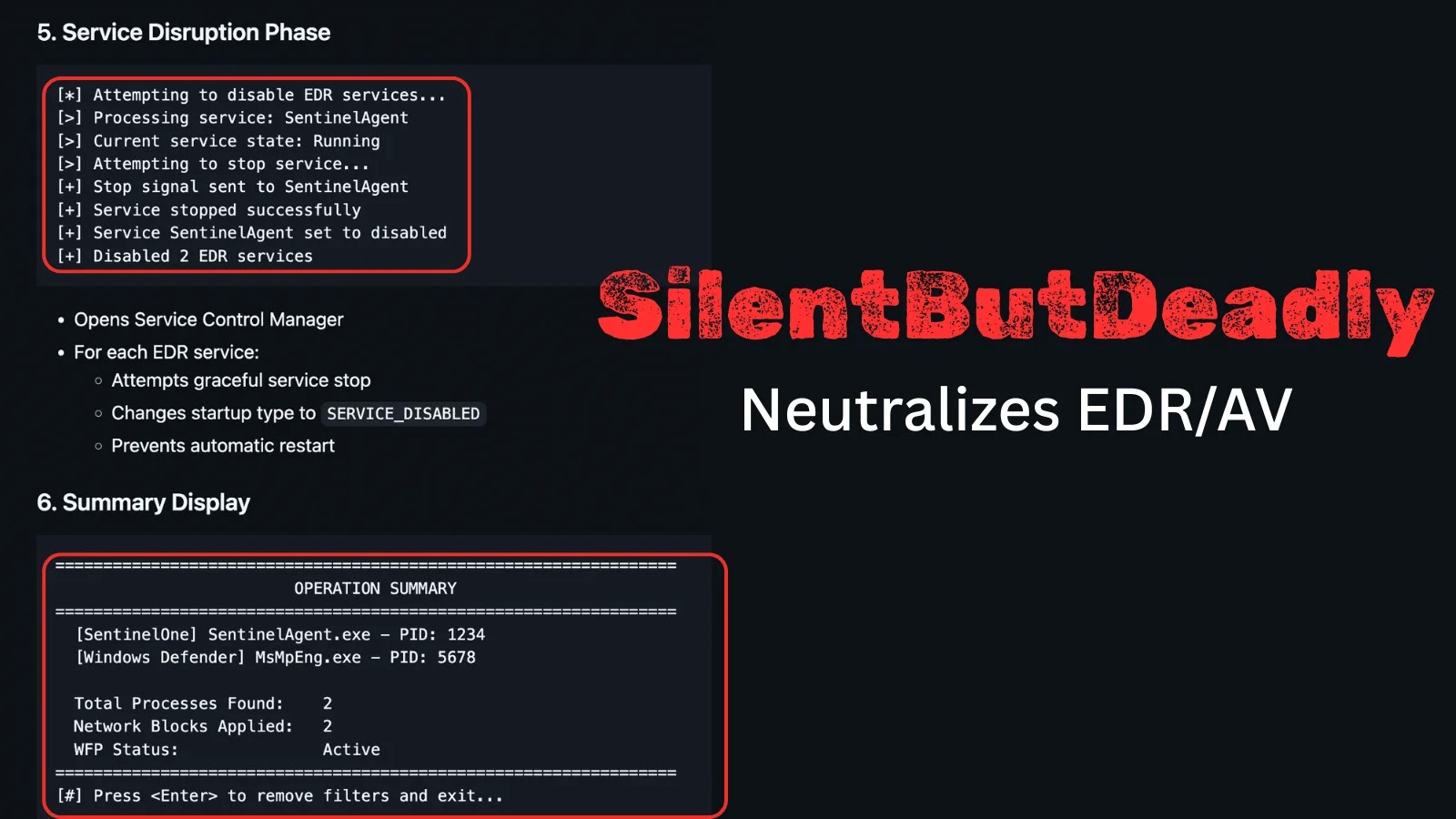
In response to CISA’s Recognized Exploited Vulnerabilities (KEV) catalog, malicious actors can craft a script that methods a sufferer’s machine into initiating an SMB connection again to the attacker’s system.
This pressured authentication grants unauthorized entry, probably permitting full management over the compromised system.
Linked to CWE-284 (Improper Entry Management), the flaw underscores long-standing considerations with SMB’s authentication mechanisms, which have been a favourite goal for cybercriminals for the reason that WannaCry outbreak in 2017.
Home windows SMB Vulnerability Actively Exploited
Attackers leverage this vulnerability by way of social engineering or drive-by downloads, the place customers accidentaly execute the malicious payload.
As soon as triggered, the SMB shopper authenticates to the attacker’s server, bypassing typical safeguards and enabling lateral motion inside networks.
Whereas CISA notes it’s unknown if this particular flaw fuels ransomware campaigns, the method mirrors ways utilized by teams like LockBit and Conti, who routinely exploit Home windows protocols for preliminary entry.
The alert arrives at a tense time for IT admins, following a wave of SMB-related exploits in 2025, together with these focusing on unpatched Azure environments.
Specialists warn that unmitigated methods may face information exfiltration or deployment of malware, particularly in sectors like finance and healthcare.
“It is a traditional elevation-of-privilege vector that preys on default configurations,” stated cybersecurity analyst Maria Gonzalez of SentinelOne. “Admins should prioritize SMB hardening to keep away from cascading breaches.”
Mitigations
CISA urges rapid motion: Apply Microsoft’s newest patches as outlined of their safety advisories, or observe Binding Operational Directive (BOD) 22-01 for federal cloud companies.
If mitigations aren’t possible, discontinue use of affected merchandise. Instruments like Home windows Defender and third-party endpoint detection will help monitor SMB site visitors anomalies.
With a 21-day remediation window, organizations ought to scan for susceptible cases utilizing instruments similar to Nessus or Qualys. Disabling pointless SMBv1 options and implementing least-privilege entry stay finest practices.
Because the due date looms, this vulnerability serves as a name to bolster defenses in opposition to evolving Home windows threats.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.