Cybersecurity is not only about protection; it’s about defending income. Organizations with out fashionable risk intelligence (TI) face escalating breach prices, wasted sources, and operational inefficiencies that hit the underside line.
Actionable intel may help companies lower prices, optimize workflows, and neutralize dangers earlier than they escalate.
Safety operations facilities (SOCs) undergo from inefficiency and burnout with out high-fidelity TI. Analysts manually sift by hundreds of alerts, a lot of that are false positives, losing time and budgets whereas overlooking actual threats.
This reactive chaos results in excessive turnover, with false positives costing enterprises as much as $1.3 million yearly in labor alone, and burnout making workers twice as prone to search new jobs.
Undetected threats flip into monetary disasters, exploiting visibility gaps and gradual responses. Generic TI feeds typically miss evasive assaults, permitting breaches to trigger downtime, fines, and misplaced belief.
The worldwide common breach price in 2025 is $4.44 million, with U.S. organizations going through $10.22 million, whereas almost one in 5 small and medium-sized companies (SMBs) may shut after a profitable assault.
Compliance gaps invite fines and authorized dangers, as regulators demand proactive risk documentation. With out real-time TI, audits reveal shortcomings, triggering penalties like GDPR’s as much as 4% of world income or €20 million, and HIPAA violations exceeding $1.5 million per incident.
5 Methods for Price Financial savings with Risk Intelligence
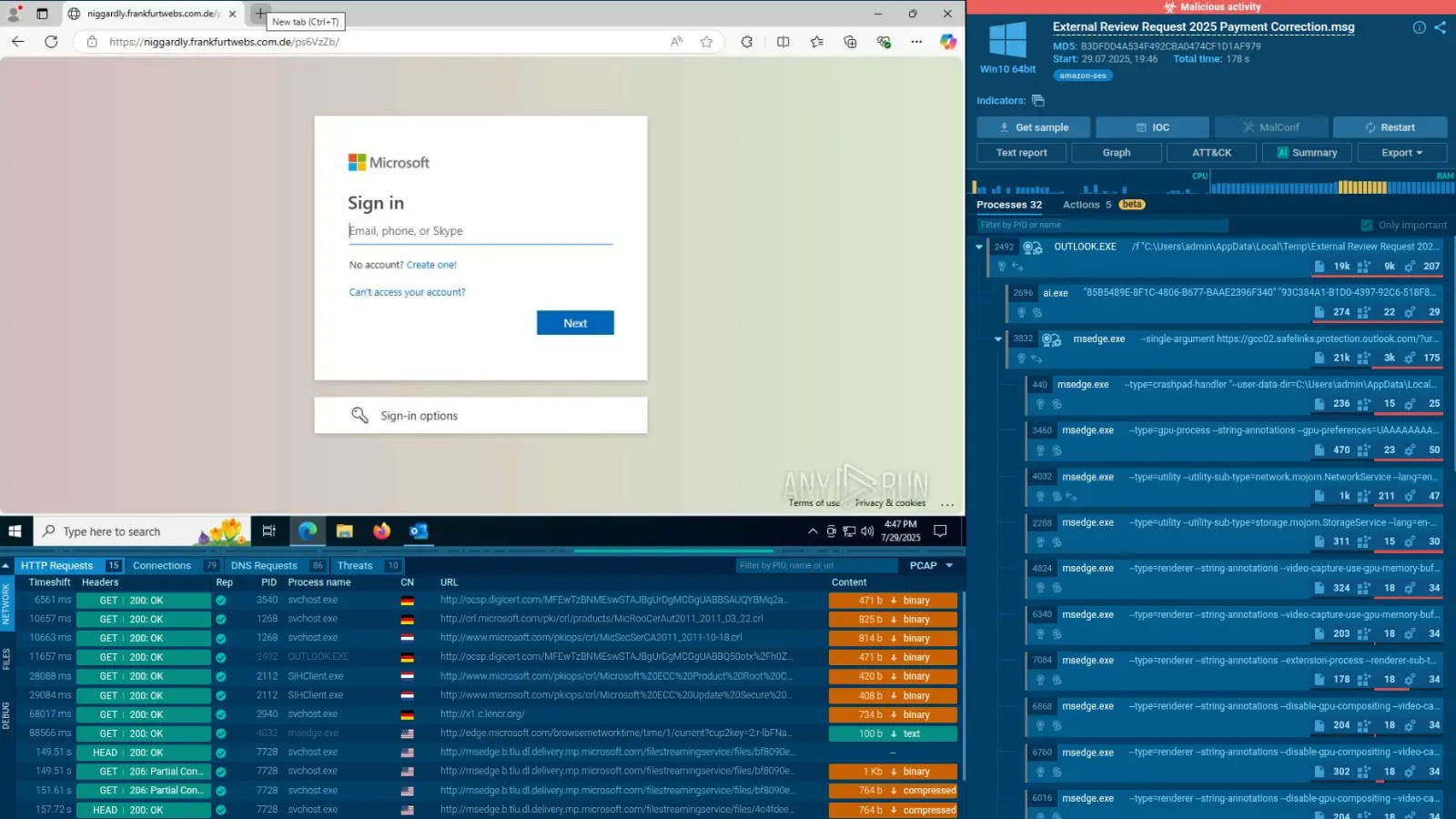
TI prevents breaches early by feeds offering real-time knowledge on indicators of compromise (IOCs). ANY.RUN’s Risk Intelligence Feeds ship actionable intel from over 15,000 SOC investigations, blocking threats on the supply and avoiding multimillion-dollar recoveries.
Stopping Breaches Proactively
Risk intelligence (TI) stops breaches early by delivering real-time IOC feeds that combine with firewalls and EDR instruments for automated blocking of threats like malicious domains.
Platforms akin to ANY.RUN offers 24 occasions extra IOCs from world SOC knowledge, enabling fast threat isolation and lowering breach chance by as much as 70% by predictive attacker insights.
Eliminating False Optimistic Waste
TI filters alerts by enriching them with context on risk actors and TTPs, chopping investigation time on benign occasions and assuaging alert fatigue that wastes 30% of analyst hours.
ANY.RUN’s TI Lookup prioritizes high-risk threats through SIEM integrations, saving as much as 50% in labor by focusing groups on verified risks reasonably than noise.
Slicing Labor Prices By Automated Triage
Automated TI triage makes use of APIs to attach with SOAR and EDR, offering immediate sandbox context to cut back handbook escalations and empower junior analysts.
ANY.RUN’s SDK automates artifact enrichment, minimizing turnover and extra time whereas boosting SOC capability by 20-30% with out further hires.
Accelerating Response to Restrict Injury
TI speeds incident response with full assault visibility from single IOCs, shortening MTTR by 40-60% by sandbox reviews on malware behaviors.
ANY.RUN’s feeds hyperlink to detailed analyses, enabling exact containment that cuts downtime prices—as much as $100,000 per hour—and prevents income loss from extended incidents.
Sustaining Up-to-Date Defenses Effortlessly
Steady TI updates ship real-time, 99% distinctive IOCs with MITRE ATT&CK mappings, automating diversifications to evolving threats like ransomware with out handbook effort.
ANY.RUN’s question notifications preserve defenses proactive, lowering breach dangers by 50% and avoiding prices from outdated static feeds.
It eliminates false optimistic waste by filtering alerts for verified threats. ANY.RUN’s options lower noise, saving hours on triage and redirecting budgets to high-impact duties, lowering alert fatigue that plagues groups.
Automated triage lowers labor prices through seamless integrations. ANY.RUN’s API and SDK join with SIEM, SOAR, and EDR instruments, enriching alerts immediately and minimizing escalations, thus avoiding extra time and hiring wants.
Quicker responses reduce fallout, with TI offering full assault context from sandbox analyses. ANY.RUN’s TI Lookup affords immediate IOC enrichment, shortening imply time to reply (MTTR) and limiting downtime losses.
Steady updates future-proof defenses with out handbook effort. ANY.RUN’s feeds refresh in actual time with 99% distinctive IOCs, integrating MITRE ATT&CK mappings to adapt to evolving threats proactively.
A world transport agency battled phishing and malware by adopting ANY.RUN’s TI Lookup for automated monitoring of geo-targeted threats and CVEs.
Customized queries and real-time updates enabled fast rule creation, slashing handbook analysis and boosting detection pace. The outcome: blocked assaults preemptively, optimized sources, and enhanced proactive defenses towards shifting attacker ways.
Risk intelligence like ANY.RUN’s TI Feeds and Lookup transforms safety from a value heart right into a revenue protector.
Construct Stronger Safety With Contemporary TI Information From 500,000 Analysts => Attempt Now