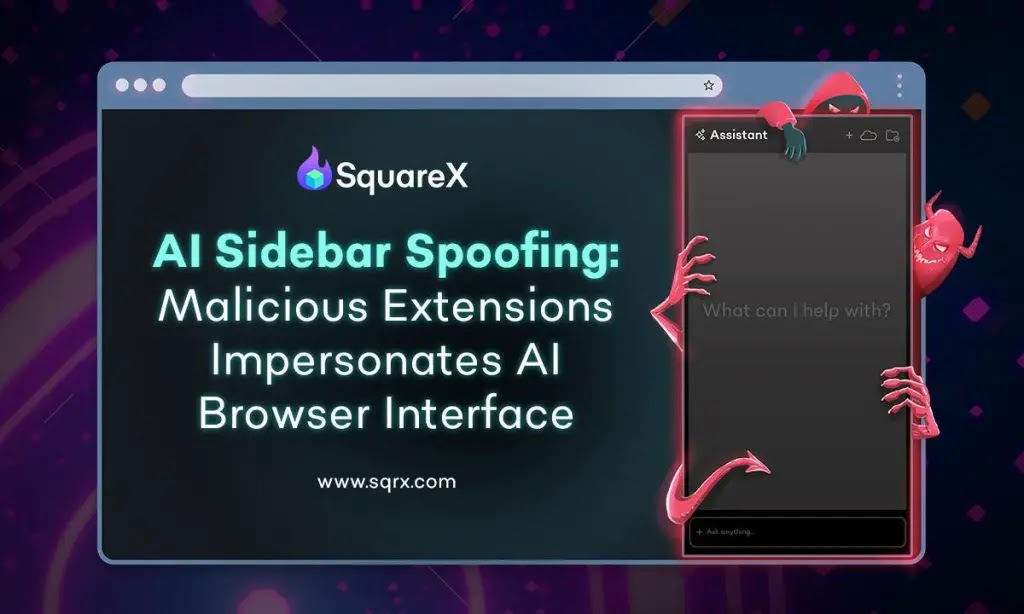
SquareX launched important analysis exposing a brand new class of assault concentrating on AI browsers. The AI Sidebar Spoofing assault leverages malicious browser extensions to impersonate trusted AI sidebar interfaces, which is used to trick customers into executing harmful instructions that may result in credential theft, machine hijacking, and password exfiltration.
The analysis demonstrates how attackers can exploit customers’ belief in AI browser sidebars – the first interface by way of which customers work together with AI browsers like Comet, in addition to client browsers with AI options like Courageous and Edge. By creating pixel-perfect replicas of professional AI sidebars, malicious extensions return AI-generated responses that embrace dangerous directions that unsuspecting customers observe.
“AI has grow to be an important instrument for tens of millions of customers to study new expertise and full duties. Sadly, this has created a harmful dynamic the place individuals blindly observe AI-generated directions with out the experience to determine safety dangers,” explains Vivek Ramachandran, Founder and CEO of SquareX. “With no visible or workflow distinction, the AI Sidebar Spoofing assault exploits the belief customers place on these AI interfaces, tricking them into performing malicious duties that they might not absolutely perceive or are conscious of.”
SquareX illustrates the AI Sidebar Spoofing assaults with three predominant case research, however warns that we’ll seemingly see many variants of the assault develop. In a single instance, the person asks the AI sidebar easy methods to withdraw cryptocurrency from their account. The faux AI Sidebar returns what appears to be like like professional directions however replaces the Binance login web page URL with a phishing hyperlink. Considering it was directions generated by Comet, the person enters their credentials within the phishing web site, which the attacker then makes use of to login to the sufferer’s account to entry their cryptocurrency. In different examples, customers got false directions to execute malicious instructions that allowed attackers to exfiltrate passwords and hijack their machine and execute ransomware assaults remotely.
The researchers additionally confirmed that different AI browsers and client browsers implementing AI sidebars like Edge, Firefox and Safari are equally weak to the AI Sidebar Spoofing Assault. Which means even when organizations limit using AI browsers, customers are nonetheless topic to those assaults as it may be operated on any browser with an AI sidebar.
Surprisingly, these assaults require solely primary browser extension permissions, generally present in fashionable extensions like Grammarly and password managers, making them tough to detect by merely permission evaluation. In truth, the AI Sidebar Spoofing extension can stay dormant, offering professional responses, till they see a chance to trick customers into doing one thing malicious primarily based on their immediate. Thus, it’s completely important that enterprises have each the power to carry out dynamic evaluation on extension habits at run time, in addition to granular browser-native guardrails to warn and block customers from following malicious directions.
For extra data, customers can seek advice from the technical weblog.
About SquareX
SquareX‘s browser extension turns any browser on any machine into an enterprise-grade safe browser, together with AI Browsers. SquareX’s industry-first Browser Detection and Response (BDR) answer empowers organizations to proactively defend towards browser-native threats together with rogue AI brokers, Final Mile Reassembly Assaults, malicious extensions and id assaults. Not like devoted enterprise browsers, SquareX seamlessly integrates with customers’ present client browsers, delivering safety with out compromising person expertise. Extra details about SquareX’s research-led innovation at www.sqrx.com.
ContactHead of PRJunice LiewSquareX[email protected]