Might 22, 2025Ravie LakshmananCybersecurity / Vulnerability
A privilege escalation flaw has been demonstrated in Home windows Server 2025 that makes it potential for attackers to compromise any person in Energetic Listing (AD).
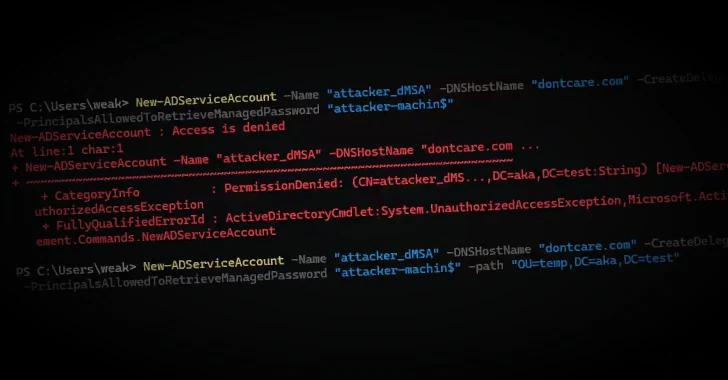
“The assault exploits the delegated Managed Service Account (dMSA) function that was launched in Home windows Server 2025, works with the default configuration, and is trivial to implement,” Akamai safety researcher Yuval Gordon stated in a report shared with The Hacker Information.
“This problem doubtless impacts most organizations that depend on AD. In 91% of the environments we examined, we discovered customers exterior the area admins group that had the required permissions to carry out this assault.”
What makes the assault pathway notable is that it leverages a brand new function referred to as Delegated Managed Service Accounts (dMSA) that enables migration from an present legacy service account. It was launched in Home windows Server 2025 as a mitigation to Kerberoasting assaults.
The assault approach has been codenamed BadSuccessor by the net infrastructure and safety firm.
“dMSA permits customers to create them as a standalone account, or to interchange an present customary service account,” Microsoft notes in its documentation. “When a dMSA supersedes an present account, authentication to that present account utilizing its password is blocked.”
“The request is redirected to the Native Safety Authority (LSA) to authenticate utilizing dMSA, which has entry to every part the earlier account might entry in AD. Throughout migration, dMSA routinely learns the units on which the service account is for use which is then used to maneuver from all present service accounts.”
The issue recognized by Akamai is that through the dMSA Kerberos authentication section, the Privilege Attribute Certificates (PAC) embedded right into a ticket-granting ticket (i.e., credentials used to confirm identification) issued by a key distribution heart (KDC) contains each the dMSAs safety identifier (SID) in addition to the SIDs of the outdated service account and of all its related teams.
This permissions switch between accounts might open the door to a possible privilege escalation state of affairs by simulating the dMSA migration course of to compromise any person, together with area directors, and achieve comparable privileges, successfully breaching your complete area even when a corporation’s Home windows Server 2025 area is not utilizing dMSAs in any respect.
“One fascinating reality about this ‘simulated migration’ approach, is that it does not require any permissions over the outdated account,” Gordon stated. “The one requirement is to jot down permissions over the attributes of a dMSA. Any dMSA.”
“As soon as we have marked a dMSA as preceded by a person, the KDC routinely assumes a respectable migration happened and fortunately grants our dMSA each single permission that the unique person had, as if we’re its rightful successor.”
Akamai stated it reported the findings to Microsoft on April 1, 2025, following which the tech large categorised the difficulty as reasonable in severity and that it doesn’t meet the bar for rapid servicing attributable to the truth that profitable exploitation requires an attacker to have particular permissions on the dMSA object, which suggests an elevation of privileges. Nevertheless, a patch is at present within the works.
On condition that there isn’t any rapid repair for the assault, organizations are suggested to restrict the flexibility to create dMSAs and harden permissions wherever potential. Akamai has additionally launched a PowerShell script that may enumerate all non-default principals who can create dMSAs and record the organizational items (OUs) through which every principal has this permission.
“This vulnerability introduces a beforehand unknown and high-impact abuse path that makes it potential for any person with CreateChild permissions on an OU to compromise any person within the area and achieve comparable energy to the Replicating Listing Modifications privilege used to carry out DCSync assaults,” Gordon stated.
Discovered this text fascinating? Observe us on Twitter and LinkedIn to learn extra unique content material we put up.