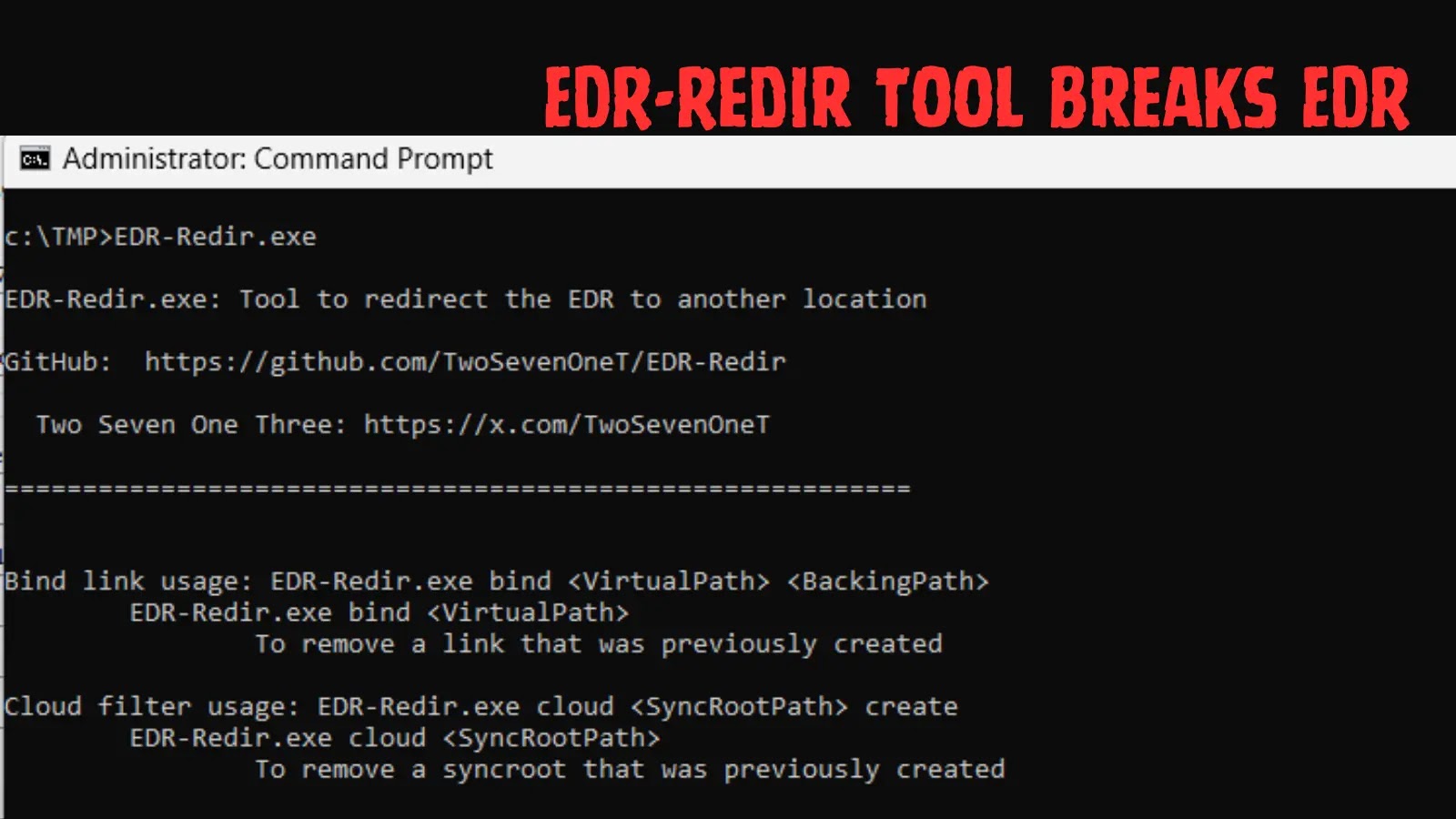
A brand new device referred to as EDR-Redir has emerged, permitting attackers to redirect or isolate the executable folders of common Endpoint Detection and Response (EDR) options.
Demonstrated by cybersecurity researcher TwoSevenOneT, the method leverages Home windows’ Bind Filter driver (bindflt.sys) and Cloud Filter driver (cldflt.sys) to undermine EDR protections with out requiring kernel-level entry.
This user-mode exploit, rooted within the Carry Your Personal Susceptible Driver (BYOVD) strategy, might allow attackers to disable defenses, inject malicious code, or hijack processes, leaving techniques susceptible to undetected intrusions.
The vulnerability stems from Home windows 11’s Bind Hyperlink function, launched in model 24H2. Bind Hyperlinks present filesystem namespace redirection through digital paths, managed by the bindflt.sys minifilter driver.
Not like conventional symbolic hyperlinks, which EDRs actively monitor and block utilizing mechanisms like Microsoft’s RedirectionGuard, Bind Hyperlinks function transparently on the driver degree.
They map digital paths to actual ones, native or distant, with out creating bodily information, inheriting permissions from the goal whereas remaining invisible to most functions.
This subtlety permits attackers with administrator privileges to carry out learn and open operations on protected EDR folders, that are usually locked in opposition to writes.
EDR-Redir, obtainable as an open-source device on GitHub, simplifies the method with easy instructions. As an example, operating “EDR-Redir.exe bind C:TMP123 C:TMP456” creates a digital path at C:TMP123 that redirects all interactions to C:TMP456.
The researcher examined this in opposition to a number of EDRs. With Elastic Defend and Sophos Intercept X, the device efficiently redirected their executable folders to attacker-controlled places.
Sophos EDR Break
Elastic EDR
As soon as redirected, adversaries might drop DLLs for course of hijacking, insert malicious executables, or empty the folder to halt EDR operations on reboot. Notably, these Bind Hyperlinks don’t persist throughout restarts, requiring a scheduled activity or service for automation.
Bypassing Home windows Defender with Cloud Filter Tips
Home windows Defender proved extra resilient to direct Bind Hyperlink redirection, doubtless resulting from its built-in protections. Nevertheless, the researcher devised a workaround utilizing the Cloud Information API (CFAPI), powered by cldflt.sys.
Sync Fail
This API, designed for sync engines like OneDrive, allows on-demand file entry by means of placeholder information. By invoking CfRegisterSyncRoot with minimal insurance policies basically an incomplete registration EDR-Redir registers the Defender folder as a “sync root.”
This corrupts entry, stopping the EDR from studying or writing to its listing. Put up-reboot, Defender’s providers fail to begin, successfully isolating it.
Not like Bind Hyperlinks, this Cloud Filter methodology persists with out further setup, making it notably stealthy. A demo video shared by the researcher illustrates the method, displaying Defender’s folder turning into inaccessible after registration.
Assessments confirmed related efficacy in opposition to two unnamed industrial EDRs, highlighting a broad danger.
This method underscores a rising problem: EDRs should evolve past user-mode symlink defenses to scrutinize minifilter interactions. Attackers achieve full management over EDR behaviors, probably evading detection in red-team workouts or actual breaches.
Organizations ought to audit administrator privileges, monitor for uncommon driver masses, and apply Home windows patches promptly. Distributors like Microsoft, Elastic, and Sophos are urged to reinforce folder protections in opposition to these API abuses.
As endpoint threats intensify, instruments like EDR-Redir remind us that even strong defenses can falter on ignored filesystem options.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.