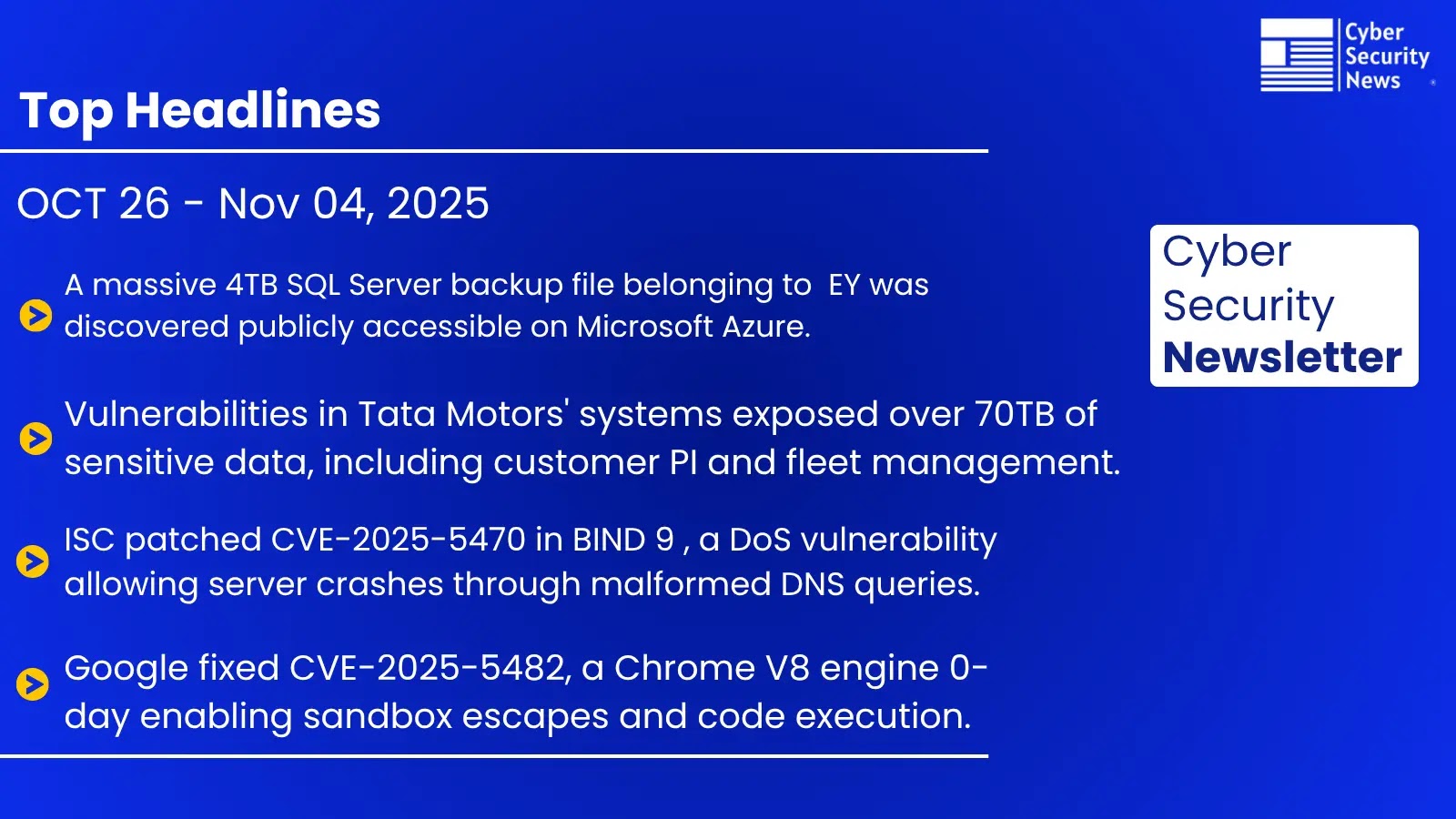
Qilin ransomware has emerged as one of the vital devastating threats within the second half of 2025, working at an alarming tempo with over 40 sufferer disclosures per thirty days on its public leak web site.
Initially tracked below the title Agenda earlier than rebranding to Qilin round July 2022, this ransomware-as-a-service platform has developed into a world menace affecting organizations throughout a number of continents and industrial sectors.
The group’s dual-extortion mannequin combines file encryption with knowledge theft and public disclosure, creating compounded stress on victims to pay extortion calls for.
Manufacturing represents the hardest-hit sector at 23% of all circumstances, trailed by skilled providers at 18%, whereas the USA faces the best focus of assaults.
The menace panorama reveals Qilin’s subtle assault infrastructure spanning from preliminary entry by way of knowledge exfiltration to closing encryption and persistence mechanisms.
Cisco Talos analysts recognized that attackers usually acquire community entry by way of compromised VPN credentials sourced from darkish net leaks, mixed with the absence of multi-factor authentication protections.
Preliminary intrusion through VPN (Supply – Cisco Talos)
As soon as inside sufferer networks, operators carry out intensive reconnaissance utilizing official Home windows utilities like nltest.exe and web.exe to map area infrastructure and establish high-value targets.
The investigation uncovered that Qilin operators make use of a methodical knowledge harvesting strategy earlier than deploying encryption payloads, permitting them to establish and exfiltrate probably the most delicate firm data earlier than triggering system-wide encryption.
Cisco Talos analysts recognized a very ingenious approach the place attackers leverage built-in Home windows purposes to find delicate recordsdata throughout the reconnaissance section.
The analysis reveals that artifact logs constantly present mspaint.exe and notepad.exe being executed to manually examine and consider high-sensitivity data throughout community storage techniques.
Quite than relying solely on automated file discovery scripts, operators use these seemingly innocuous purposes to open and overview recordsdata, maybe to confirm knowledge high quality earlier than compression and exfiltration.
This guide inspection strategy permits attackers to prioritize probably the most helpful mental property, monetary data, and confidential paperwork whereas avoiding frequent safety signatures related to automated knowledge discovery instruments.
Twin-Encryptor Deployment Technique
The twin-encryptor deployment technique additional demonstrates operational sophistication throughout the Qilin ecosystem.
The primary variant, encryptor_1.exe, spreads laterally utilizing PsExec throughout compromised hosts with administrator privileges and inner password specs hardcoded into the binary.
The second variant, encryptor_2.exe, operates from a single system to encrypt a number of community shares concurrently, maximizing protection and influence throughout distributed infrastructure.
Earlier than encryption initiates, operators set up persistence by way of scheduled duties named TVInstallRestore and registry modifications below RUN keys, guaranteeing ransomware survives system reboots.
The malware particularly targets essential infrastructure together with Cluster Shared Volumes internet hosting Hyper-V digital machines and databases whereas intentionally excluding system recordsdata required for boot performance, a calculated strategy guaranteeing victims can not simply get better by way of working system reinstallation.
For knowledge exfiltration, Qilin operators make use of Cyberduck, an open-source file switch utility that obscures malicious exercise inside official cloud service site visitors directed towards Backblaze servers.
Earlier than knowledge departure, directors deploy WinRAR with specialised parameters excluding base folders and disabling recursive subdirectory processing, creating optimized archive configurations.
The mix of guide file inspection utilizing commonplace Home windows purposes, subtle deployment techniques, and cloud-based exfiltration represents a mature menace operation demanding complete detection and response capabilities from organizations worldwide.
Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most well-liked Supply in Google.