Tel Aviv, Israel, October twenty ninth, 2025, CyberNewsWire
Candy Safety Brings Runtime-CNAPP Energy to Home windows
Candy Safety, a pacesetter in Runtime Cloud and AI safety options, immediately introduced an extension of its Runtime CNAPP sensor to incorporate Home windows environments.
With this launch, organizations can safe Home windows workloads and purposes within the cloud.
The brand new functionality brings the identical deep visibility, real-time detection, danger prioritization, and automatic investigation that energy Candy’s Runtime CNAPP for Linux to one of the vital advanced and extensively used working methods within the enterprise cloud.
Defending cloud workloads operating on the Home windows working system has lengthy been a problem as a result of complexity and the big selection of assault vectors that adversaries can exploit.
Many present options depend on an EDR agent that’s been repurposed for the cloud, however was in the end designed for completely totally different assault situations than those current within the cloud.
Candy’s Home windows sensor was developed particularly for the cloud utilizing Rust, which permits for minimal useful resource footprint.
Candy’s Home windows sensor covers all the standard assault vectors, similar to DLL injection, registry manipulation, PowerShell scripting, and many others., along with overlaying application-level requests and responses (Layer 7 knowledge), peering into purposes’ habits.
Like all of Candy’s runtime indicators, the Home windows sensor depends on Candy’s famend behavioral baselining expertise, which permits it to detect not simply identified assault methods or binary signatures, but in addition the abuse of official instruments for malicious functions.
The indicators are additionally cross-correlated with cloud audit logs and cloud identities (CDR and ITDR) for max context and observability.
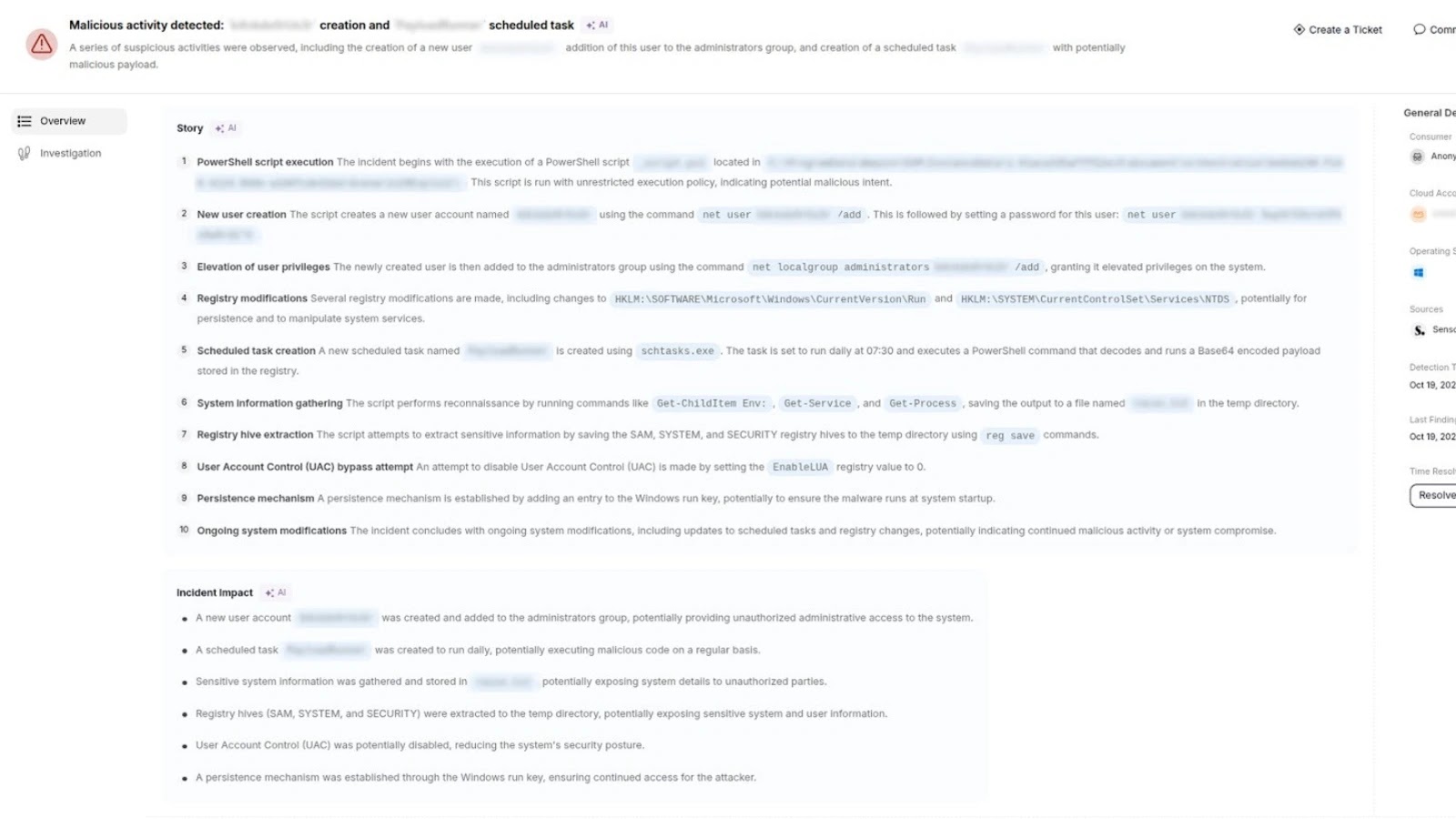
In a current buyer analysis, Candy’s Home windows sensor recognized a credential-dumping try inside seconds. The sensor correlated PowerShell execution, registry export, and file creation anomalies that conventional sensors did not detect.
From detection to full investigation, all the course of took beneath two minutes, demonstrating how Candy’s behavioral and AI-powered detection capabilities speed up response instances and scale back investigation noise.
With Candy’s Home windows runtime sensor, clients now have a transparent view of exercise throughout all workloads. They’re now capable of detect and deal with potential threats quicker and with better confidence, defending vital workloads and sustaining enterprise continuity.
With the extension to Home windows, Candy Safety now leverages its patented LLM-powered correlation and investigation, behavioral baseline, and L7 capabilities to offer full-stack safety for the cloud with its runtime CNAPP, together with:
Cloud Utility Detection and Response (CADR)
Cloud Safety Posture Administration (CSPM)
Kubernetes Safety Posture Administration (KSPM)
Cloud Infrastructure Entitlements Administration (CIEM)
Compliance & Governance
Vulnerability Administration
CI/CD Pipeline Hardening
Identities Safety (ITDR)
API Safety
Dynamic Utility Safety Testing (DAST)
Knowledge Safety (DSPM)
“This launch marks a significant step ahead for all the cloud safety {industry},” stated Orel Ben Ishay, co-founder and VP of R&D, Candy Safety.
“Home windows has traditionally been a blind spot for runtime safety. By bringing the identical depth of behavioral perception, AI-powered detection, and real-time investigation that we ship for Linux to Home windows environments, we’re eliminating one of the vital vital visibility gaps in cloud safety. Detection and full investigation can now take lower than two minutes, offering groups with actionable insights quicker than ever. This can be a foundational step towards our imaginative and prescient of common runtime safety throughout all cloud workloads.”
With this launch, Candy Safety continues to redefine runtime-native CNAPP, serving to organizations detect and cease refined assaults earlier than they affect vital cloud workloads.
For extra data on Candy’s Home windows sensor or Runtime CNAPP, customers can ebook a demo immediately or contact their buyer help consultant.
About Candy Safety
Candy Safety is redefining enterprise cloud safety.
Because the main supplier of Runtime CNAPP options and a pioneer in AI Safety, Candy unifies runtime context with superior AI intelligence to guard the trendy enterprise throughout purposes, workloads, and infrastructure.
Its platform delivers real-time detection and response, vulnerability and posture administration, id risk safety, and API safety—powered by patent-pending, LLM-driven detection, lowering alert noise to only 0.04%.
By bridging cloud and AI safety, Candy permits organizations to speed up innovation, scale back operational danger, and obtain industry-leading MTTR instances.
Privately funded, Candy is backed by Evolution Fairness Companions, Munich Re Ventures, Glilot Capital Companions, CyberArk Ventures, and an elite group of angel traders. For extra data, customers can go to candy.safety.
Contact
Chloe Amante
Montner Tech PR
[email protected]