Oct 30, 2025Ravie LakshmananMalware / Cybercrime
The open-source command-and-control (C2) framework often known as AdaptixC2 is being utilized by a rising variety of menace actors, a few of whom are associated to Russian ransomware gangs.
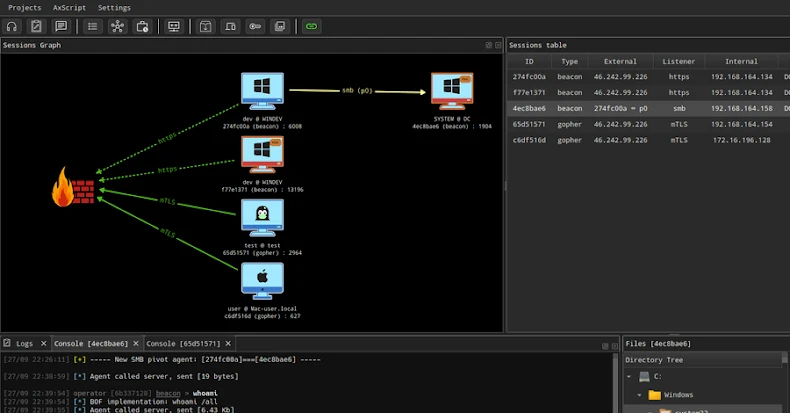
AdaptixC2 is an rising extensible post-exploitation and adversarial emulation framework designed for penetration testing. Whereas the server part is written in Golang, the GUI Shopper is written in C++ QT for cross-platform compatibility.
It comes with a variety of options, together with totally encrypted communications, command execution, credential and screenshot managers, and a distant terminal, amongst others. An early iteration was publicly launched by a GitHub person named “RalfHacker” (@HackerRalf on X) in August 2024, who describes themselves as a penetration tester, purple workforce operator, and “MalDev” (quick for malware developer).
In latest months, AdaptixC2 has been adopted by numerous hacking teams, together with menace actors tied to the Fog and Akira ransomware operations, in addition to by an preliminary entry dealer that has leveraged CountLoader in assaults which might be designed to ship numerous post-exploitation instruments.
Palo Alto Networks Unit 42, which broke down the technical points of the framework final month, characterised it as a modular and versatile framework that can be utilized to “comprehensively management impacted machines,” and that it has been put to make use of as a part of pretend assist desk assist name scams by way of Microsoft Groups and thru a man-made intelligence (AI)-generated PowerShell script.
Whereas AdaptixC2 is obtainable as an moral, open-source device for purple teaming actions, it is also clear that it has attracted the eye of cybercriminals.
Cybersecurity firm Silent Push stated RalfHacker’s GitHub bio about them being a “MalDev” triggered an investigation, permitting them to seek out a number of e-mail addresses for GitHub accounts linked to the account’s proprietor, along with a Telegram channel known as RalfHackerChannel, the place they re-shared messages posted on a devoted channel for AdaptixC2. The RalfHackerChannel channel has greater than 28,000 subscribers.
In a message on the AdaptixFramework channel in August 2024, they talked about their curiosity in beginning a undertaking a few “public C2, which could be very stylish proper now” and hoped “will probably be like Empire,” one other common post-exploitation and adversary emulation framework.
Whereas it is presently not identified if RalfHacker has any direct involvement in malicious exercise tied to AdaptixC2 or CountLoader at this stage, Silent Push stated their “ties to Russia’s legal underground, by way of using Telegram for advertising and marketing and the device’s subsequent uptick in utilization by Russian menace actors, all elevate important purple flags.”
The Hacker Information has reached out to RalfHacker for remark, and we’ll replace the story if we hear again.