All through the primary half of 2025, financially motivated menace actors have shifted their method to intrusions, abandoning conventional implant-heavy strategies in favor of a cheaper technique.
Relatively than deploying refined malware payloads, attackers are leveraging stolen credentials and legitimate account entry to determine persistence inside goal networks throughout a number of industries.
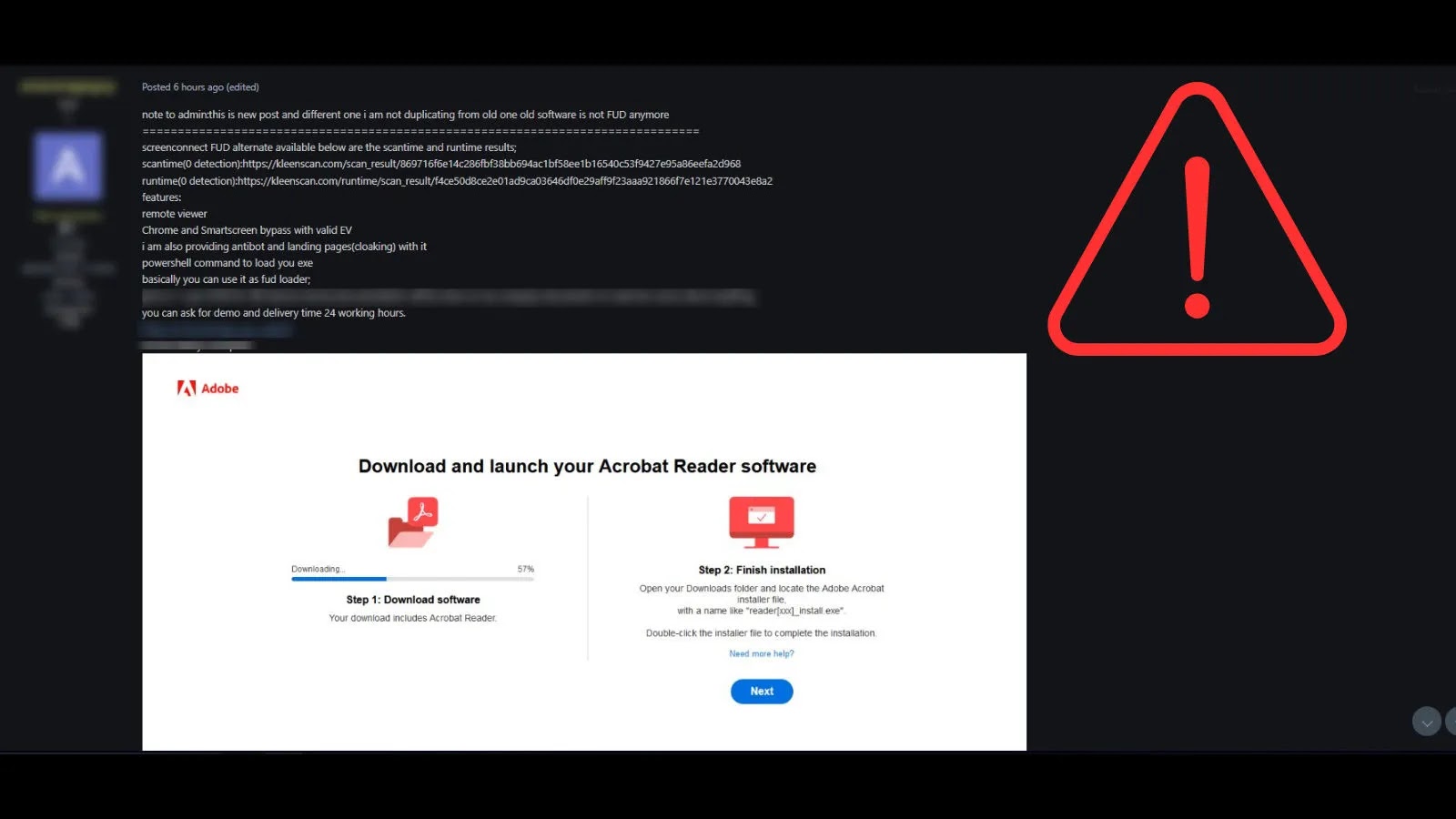
The FortiGuard Incident Response staff responded to dozens of engagements, revealing a constant sample the place adversaries achieve preliminary entry via compromised credentials, that are both harvested through phishing campaigns, bought from Preliminary Entry Brokers, or obtained via password reuse and infostealer malware distribution.
Fortinet analysts recognized that attackers exploit three main preliminary entry strategies to compromise networks.
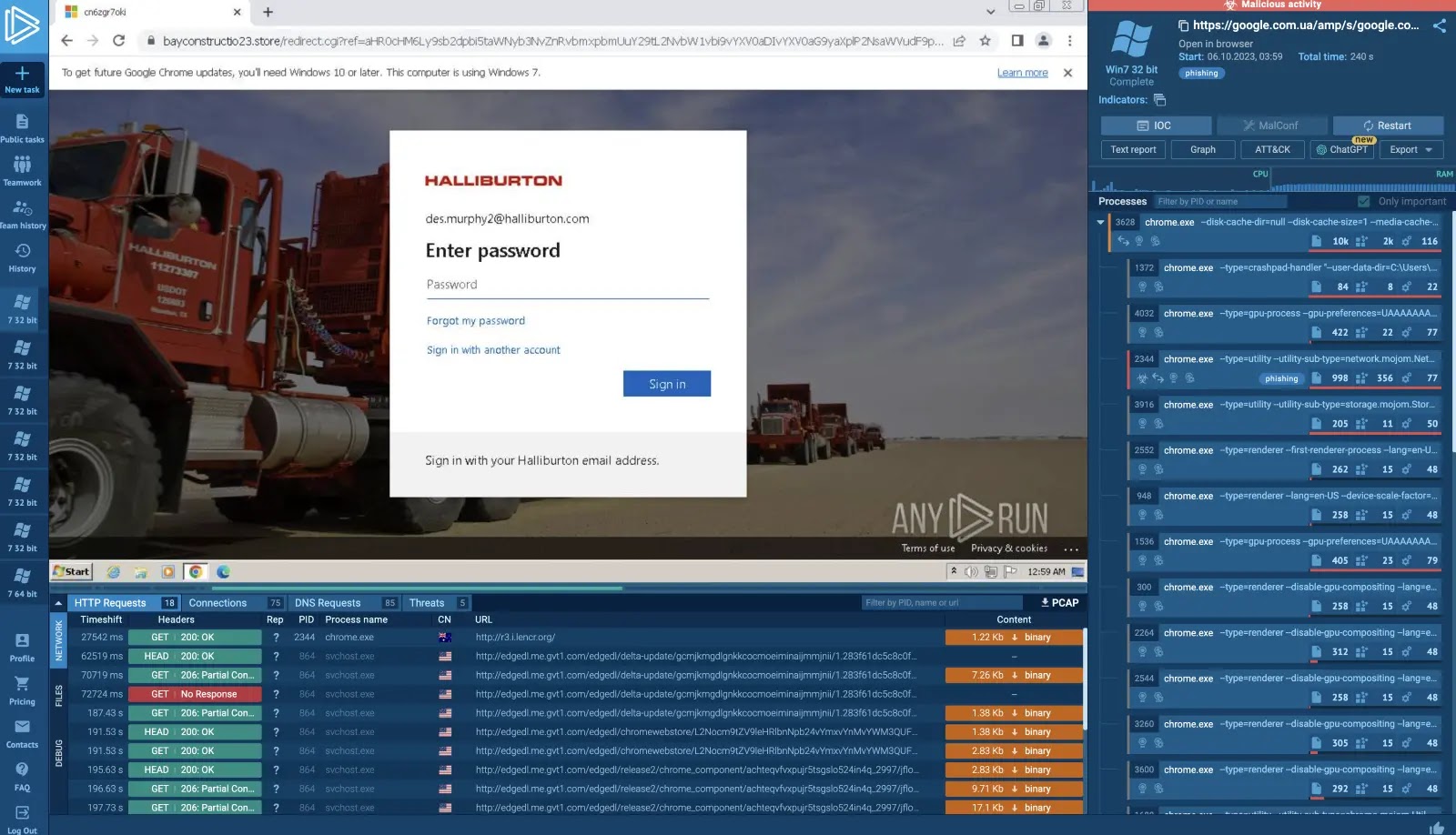
Exterior distant providers, significantly VPN infrastructure, function essentially the most prevalent entry level, permitting adversaries to authenticate utilizing stolen credentials and progress laterally via sufferer environments.
Moreover, menace actors exploit public-facing functions utilizing n-day vulnerabilities to deploy legit distant administration instruments reminiscent of AnyDesk, Atera, Splashtop, and ScreenConnect.
Compromised credentials bought from underground markets vary from $100 to $20,000 relying on organizational dimension and geographic location, making this method economically enticing for menace actors working throughout developed and rising economies.
Lateral Motion and Persistence Techniques
As soon as inside networks, Fortinet researchers famous that adversaries make use of guide, operator-driven lateral motion utilizing built-in instruments together with Distant Desktop Protocol (RDP), Server Message Block (SMB), and Home windows Distant Administration (WinRM).
This guide method allows attackers to mix with legit administrator exercise, considerably complicating detection efforts.
Sufferer Industries (Supply – Fortinet)
Adversaries preserve persistence by putting in their very own situations of distant entry instruments and leveraging privileged credentials obtained via Mimikatz execution and Zerologon exploitation for elevated account entry.
Knowledge exfiltration happens via direct file transfers through RDP and RMM interface drag-and-drop capabilities, leaving minimal forensic artifacts in comparison with standard web-based exfiltration strategies.
In noticed circumstances, attackers configured VPN infrastructure with out multi-factor authentication, granting unrestricted community entry and enabling fast encryption of hypervisor infrastructure for ransomware deployment.
This low-complexity, high-return methodology permits financially motivated adversaries to function undetected for prolonged intervals whereas avoiding the detection signatures generally related to malware-centric intrusions.
Comply with us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most popular Supply in Google.