Cybercriminals and state-sponsored actors are ramping up assaults on unpatched Cisco IOS XE gadgets throughout Australia, deploying a persistent Lua-based net shell generally known as BADCANDY to take care of unauthorized entry.
This implant, first noticed in variations since October 2023, has seen renewed exploitation all through 2024 and into 2025, exploiting the essential CVE-2023-20198 vulnerability within the software program’s net person interface.
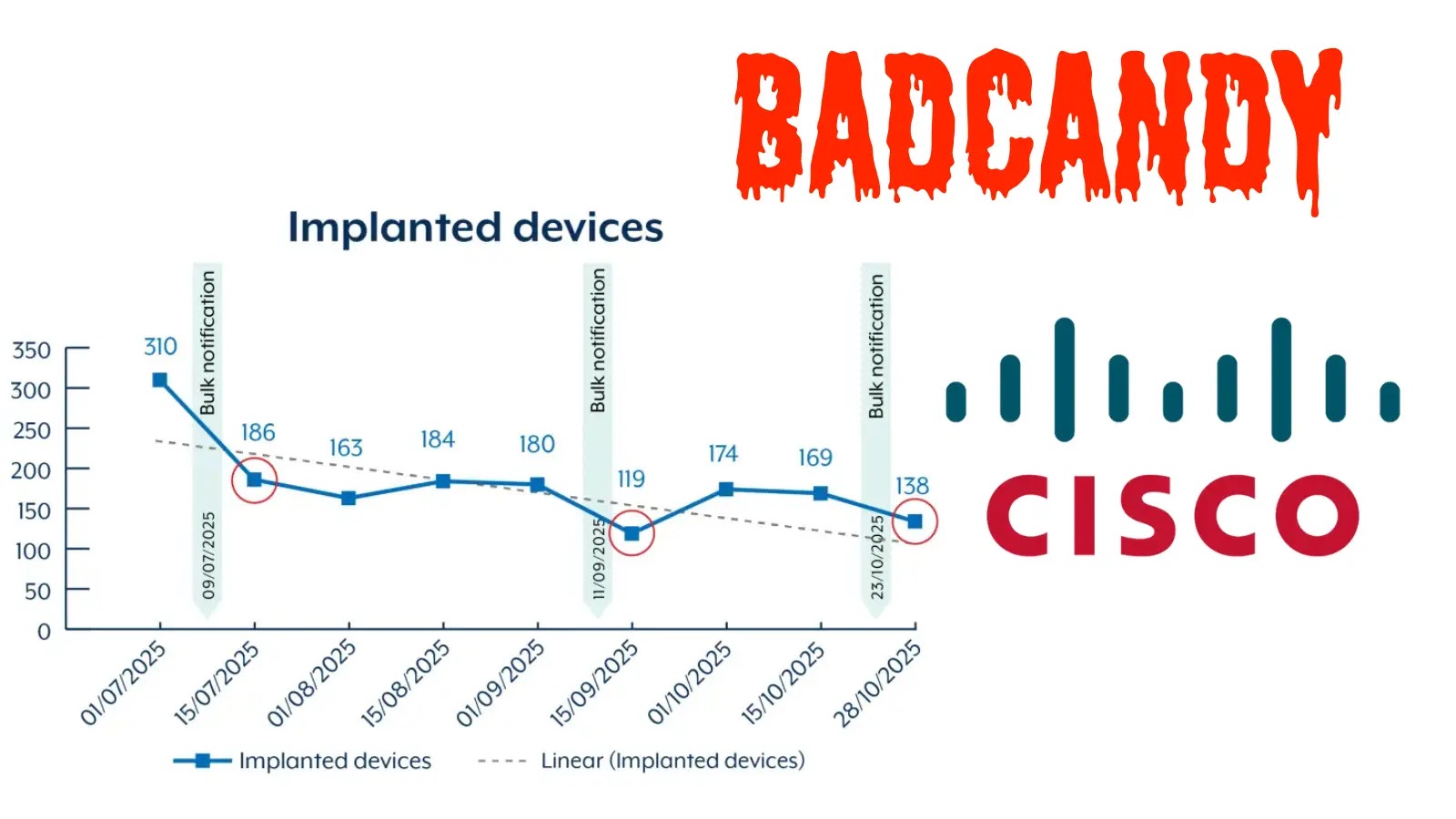
The Australian Alerts Directorate (ASD) warns that over 400 gadgets have been doubtlessly compromised since July 2025, with greater than 150 nonetheless contaminated as of late October, highlighting the continued risk to community infrastructure.
BADCANDY Net Shell Exploiting Unpatched Units
The CVE-2023-20198 flaw, rated at a most CVSS rating of 10.0, permits distant unauthenticated attackers to create extremely privileged accounts on affected Cisco IOS XE routers and switches, granting full system management with out credentials.
Cisco patched this zero-day in October 2023 amid energetic exploitation, however public exploits emerged shortly after, fueling widespread abuse by teams just like the Chinese language state-sponsored SALT TYPHOON.
ASD stories that attackers usually apply a non-persistent patch post-compromise to cover the vulnerability, whereas putting in BADCANDY—a light-weight implant that allows root-level command execution by way of a hidden URI path in an Nginx configuration file named cisco_service.conf.
Though BADCANDY vanishes upon reboot, attackers can retain entry by means of stolen credentials or different persistence strategies, making re-exploitation trivial on uncovered net interfaces.
This vulnerability ranked among the many high routinely exploited flaws in 2023, and ASD confirms ongoing assaults in 2025, notably concentrating on internet-facing gadgets.
SALT TYPHOON, linked to Chinese language intelligence, has leveraged related Cisco weaknesses in world telecom breaches, usually utilizing official credentials alongside exploits like CVE-2023-20198 and CVE-2023-20273.
Prison actors and different nation-states are additionally reusing BADCANDY, scanning for unpatched techniques and re-infecting these cleared by notifications.
The implant’s low footprint makes detection difficult with out deep configuration critiques, underscoring dangers to edge networks worldwide.
ASD’s Response
In response, ASD has issued bulk notifications to affected entities by way of service suppliers, urging fast patching, reboots, and incident response since July 2025.
These efforts decreased infections from over 400 to round 150 by late October, however fluctuations counsel actors detect and re-exploit cleared gadgets.
A graph monitoring BADCANDY implants from July to October 2025 exhibits a gradual decline punctuated by spikes round bulk notification occasions in September and early October, with the road dropping from 350 in mid-July to about 138 by late October.
ASD attributes resurgences to unpatched techniques left on-line, emphasizing that reboots alone gained’t suffice with out addressing the foundation vulnerability.
To fight this, ASD recommends reviewing operating configurations for privilege 15 accounts, particularly suspicious ones like “cisco_tac_admin” or these with random strings, and eradicating unauthorized entries.
Organizations must also scan for unknown tunnel interfaces, resembling “interface tunnel[number]” with surprising IPs, and test TACACS+ logs for adjustments if enabled.
Making use of Cisco’s patch for CVE-2023-20198 is essential, alongside disabling the HTTP server function and following the IOS XE hardening information to limit net UI entry.
Rebooting removes the implant however requires post-reboot checks for lingering adjustments, and broader edge-device safety, resembling community segmentation, can forestall lateral motion.
Cisco offers indicators of compromise in its advisory to help investigations, whereas ASD continues notifications to shrink the assault floor in Australia. By prioritizing these actions, networks can thwart re-exploitation and bolster defenses in opposition to evolving threats.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.