Nov 03, 2025Ravie LakshmananCryptocurrency / Menace Intelligence
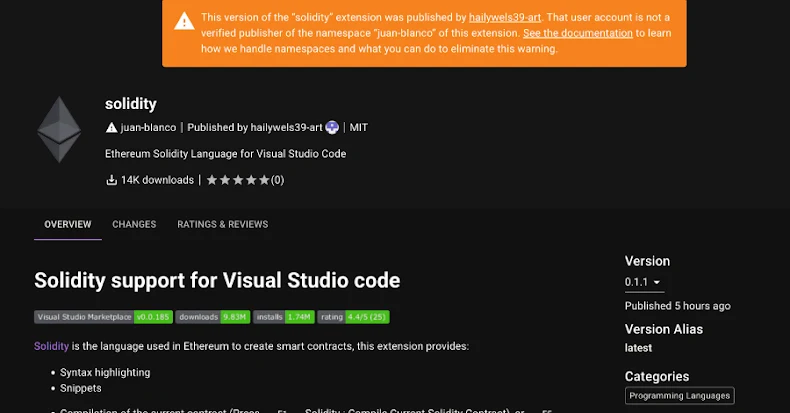
Cybersecurity researchers have flagged a brand new malicious extension within the Open VSX registry that harbors a distant entry trojan referred to as SleepyDuck.
In response to Safe Annex’s John Tuckner, the extension in query, juan-bianco.solidity-vlang (model 0.0.7), was first printed on October 31, 2025, as a very benign library that was subsequently up to date to model 0.0.8 on November 1 to incorporate new malicious capabilities after reaching 14,000 downloads.
“The malware contains sandbox evasion strategies and makes use of an Ethereum contract to replace its command and management deal with in case the unique deal with is taken down,” Tuckner added.
Campaigns distributing rogue extensions focusing on Solidity builders have been repeatedly detected throughout each the Visible Studio Extension Market and Open VSX. In July 2025, Kaspersky disclosed {that a} Russian developer misplaced $500,000 in cryptocurrency belongings after putting in one such extension by way of Cursor.
Within the newest occasion detected by the enterprise extension safety agency, the malware is triggered when a brand new code editor window is opened or a .sol file is chosen.
Particularly, it is configured to search out the quickest Ethereum Distant Process Name (RPC) supplier to connect with so as to receive entry to the blockchain, initialize contact with a distant server at “sleepyduck[.]xyz” (therefore the title) by way of the contract deal with “0xDAfb81732db454DA238e9cFC9A9Fe5fb8e34c465,” and kicks off a polling loop that checks for brand new instructions to be executed on the host each 30 seconds.
It is also able to gathering system data, equivalent to hostname, username, MAC deal with, and timezone, and exfiltrating the small print to the server. Within the occasion the area is seized or taken down, the malware has built-in fallback controls to succeed in out to a predefined record of Ethereum RPC addresses to extract the contract data that may maintain the server particulars.
What’s extra, the extension is provided to succeed in a brand new configuration from the contract deal with to set a brand new server, in addition to execute an emergency command to all endpoints within the occasion that one thing sudden happens. The contract was created on October 31, 2025, with the risk actor updating the server particulars from “localhost:8080” to “sleepyduck[.]xyz” over the course of 4 transactions.
It is not clear if the obtain counts have been artificially inflated by the risk actors to spice up the relevance of the extension in search outcomes – a tactic typically adopted to extend the recognition in order to trick unsuspecting builders into putting in a malicious library.
The event comes as the corporate additionally disclosed particulars of one other set of 5 extensions, this time printed to the VS Code Extension Market by a person named “developmentinc,” together with a Pokémon-themed library that downloads a batch script miner from an exterior server (“mock1[.]su:443”) as quickly because it’s put in or enabled, and runs the miner utilizing “cmd.exe.”
The script file, in addition to relaunching itself with administrator privileges utilizing PowerShell and configuring Microsoft Defender Antivirus exclusions by including each drive letter from C: by way of Z:, downloads a Monero mining executable from “mock1[.]su” and runs it.
The extensions uploaded by the risk actor, now not obtainable for obtain, are listed beneath –
developmentinc.cfx-lua-vs
developmentinc.pokemon
developmentinc.torizon-vs
developmentinc.minecraftsnippets
developmentinc.kombai-vs
Customers are suggested to train warning with regards to downloading extensions, and make it possible for they’re from trusted publishers. Microsoft, for its half, introduced again in June that it is instituting periodic marketplace-wide scans to guard customers in opposition to malware. Each eliminated extension from the official market could be seen from the RemovedPackages web page on GitHub.