Cybersecurity researchers and firewall monitoring companies have detected a dramatic surge in reconnaissance exercise focusing on Home windows Server Replace Companies (WSUS) infrastructure.
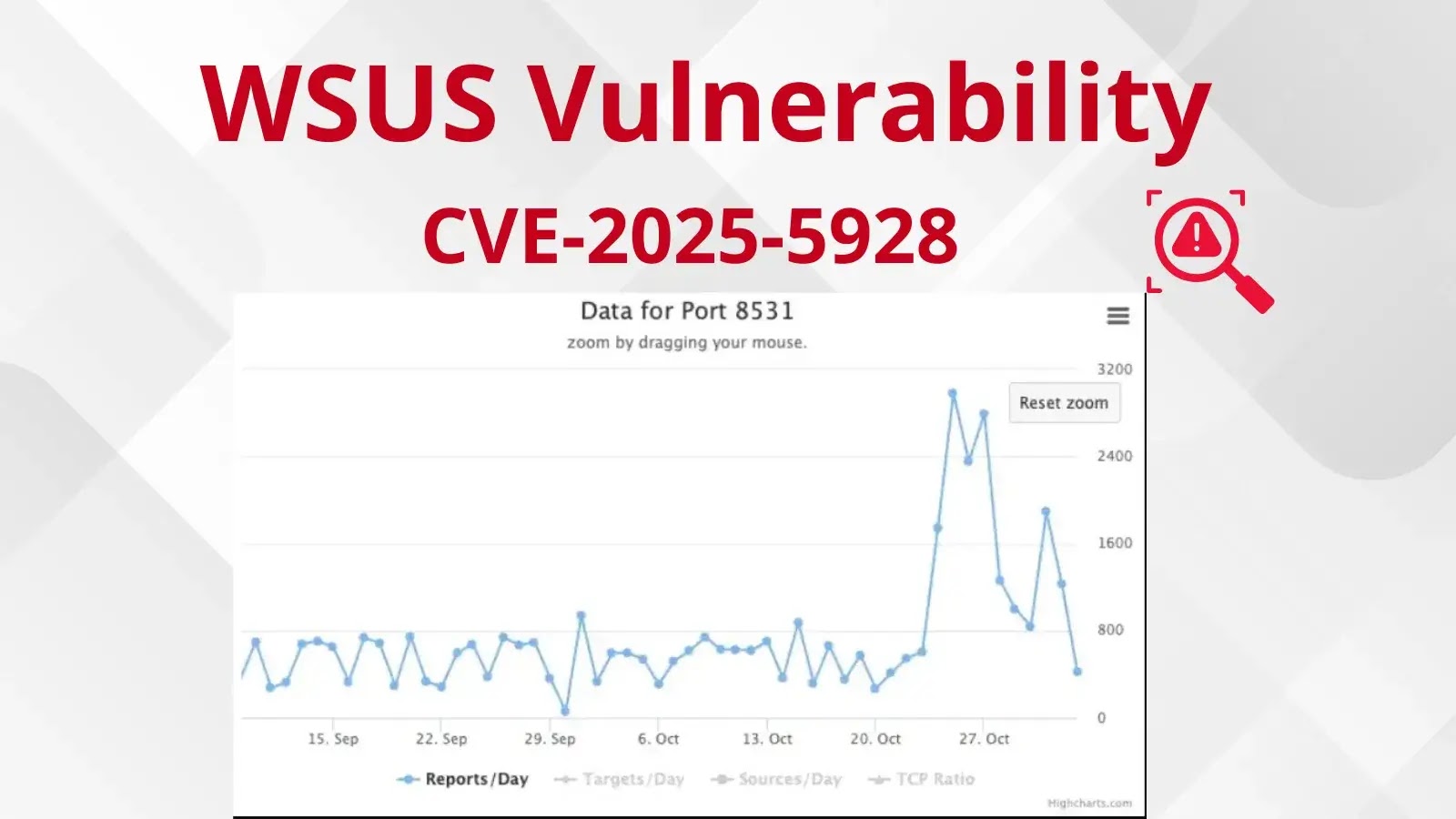
Community sensors collected from safety organizations, together with information from Shadowserver, present a major improve in scans directed at TCP ports 8530 and 8531 over the previous week.
Whereas some scanning exercise seems linked to respectable safety analysis initiatives, analysts have recognized further site visitors from unknown sources not related to identified analysis organizations, elevating issues about potential exploitation makes an attempt.
The scanning exercise correlates instantly with CVE-2025-59287, a crucial vulnerability in WSUS servers that allows distant code execution.
Attackers can exploit this flaw by connecting to weak WSUS infrastructure by way of both port 8530 (unencrypted) or 8531 (TLS-encrypted).
Efficiently establishing a connection permits risk actors to execute arbitrary scripts instantly on compromised servers with no authentication necessities.
Reconnaissance Adopted by Full Compromise
SANS evaluation reveals that risk actors usually comply with a two-stage assault sample when focusing on WSUS servers. The preliminary section entails reconnaissance and scanning to establish weak methods, which aligns with the latest surge in port scanning exercise.
As soon as attackers efficiently establish and connect with prone servers, they proceed to the exploitation section, deploying malicious scripts that grant them intensive management over the affected infrastructure.
Specialists emphasize that any publicly uncovered WSUS server displaying traits of vulnerability ought to be presumed compromised at this stage.
a major improve in scans for port 8531/TCP
The provision of adequate technical particulars in public disclosures has lowered the barrier to entry for potential attackers, enabling even reasonably expert risk actors to develop and deploy exploitation code.
Organizations ought to assume that exploitation makes an attempt have already occurred towards any methods matching the weak profile which have been linked to internet-facing networks.
The severity of this vulnerability calls for pressing motion from system directors and safety groups managing WSUS deployments. Organizations should instantly audit their community perimeter to establish any WSUS servers accessible from untrusted networks.
CVE IDVulnerabilityAffected ProductsCVSS ScoreCVE-2025-59287WSUS Script ExecutionWindows Server Replace Companies (A number of variations)9.8
These discovering uncovered situations ought to implement emergency isolation procedures and conduct complete forensic investigations to find out whether or not compromise has occurred.
Organizations with out instant patch availability ought to implement community segmentation, proscribing WSUS server entry to licensed inner networks solely.
Superior risk detection methods ought to be configured to alert on suspicious outbound connections and script execution originating from WSUS processes, as these behaviors typically point out profitable compromise.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.