Nov 04, 2025Ravie LakshmananVulnerability / Provide Chain Safety
Particulars have emerged a couple of now-patched crucial safety flaw within the well-liked “@react-native-community/cli” npm bundle that may very well be doubtlessly exploited to run malicious working system (OS) instructions beneath sure situations.
“The vulnerability permits distant unauthenticated attackers to simply set off arbitrary OS command execution on the machine working react-native-community/cli’s growth server, posing a major danger to builders,” JFrog Senior Safety Researcher Or Peles stated in a report shared with The Hacker Information.
The vulnerability, tracked as CVE-2025-11953, carries a CVSS rating of 9.8 out of a most of 10.0, indicating crucial severity. It additionally impacts the “@react-native-community/cli-server-api” bundle variations 4.8.0 by way of 20.0.0-alpha.2, and has been patched in model 20.0.0 launched early final month.
The command-line instruments bundle, which is maintained by Meta, allows builders to construct React Native cell functions. It receives roughly 1.5 million to 2 million downloads per week.
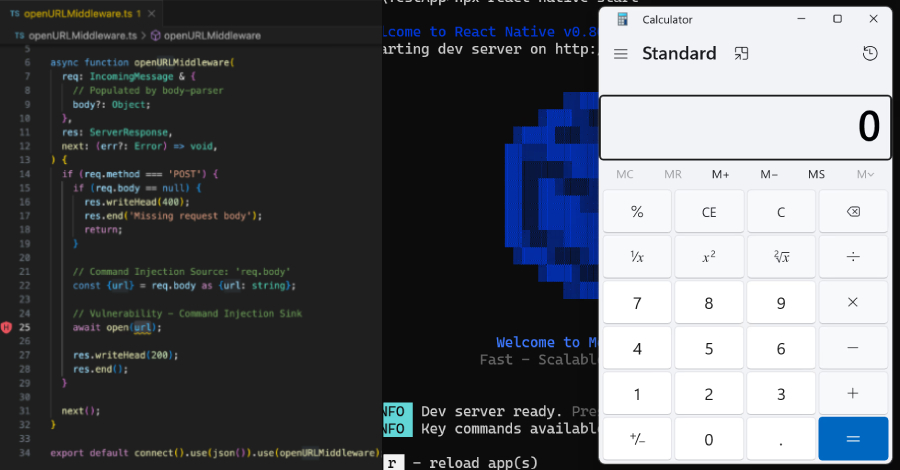
In keeping with the software program provide chain safety agency, the vulnerability arises from the truth that the Metro growth server utilized by React Native to construct JavaScript code and belongings binds to exterior interfaces by default (as an alternative of localhost) and exposes an “/open-url” endpoint that’s inclined to OS command injection.
“The server’s ‘/open-url’ endpoint handles a POST request that features a user-input worth that’s handed to the unsafe open() operate offered by the open NPM bundle, which is able to trigger OS command execution,” Peles stated.
Because of this, an unauthenticated community attacker may weaponize the flaw to ship a specifically crafted POST request to the server and run arbitrary instructions. On Home windows, the attackers may execute arbitrary shell instructions with totally managed arguments, whereas on Linux and macOS, it may be abused to execute arbitrary binaries with restricted parameter management.
Whereas the difficulty has since been addressed, builders who use React Native with a framework that does not depend on Metro as the event server should not impacted.
“This zero day vulnerability is especially harmful because of its ease of exploitation, lack of authentication necessities and broad assault floor,” Peles stated. “It additionally exposes the crucial dangers hidden in third-party code.”
“For developer and safety groups, this underscores the necessity for automated, complete safety scanning throughout the software program provide chain to make sure simply exploitable flaws are remediated earlier than they influence your group.”