The Open Net Software Safety Venture (OWASP) has unveiled the 2025 version of its flagship OWASP Prime 10 2025, marking the eighth installment and introducing important updates to handle evolving software program safety threats.
Launched on November 6, 2025, this revised model incorporates group survey enter and expanded information evaluation, highlighting two new classes whereas consolidating others to mirror root causes reasonably than signs higher.
The record stays a important useful resource for builders, safety professionals, and organizations aiming to prioritize net software dangers.
OWASP Prime 10 2025 Key Adjustments
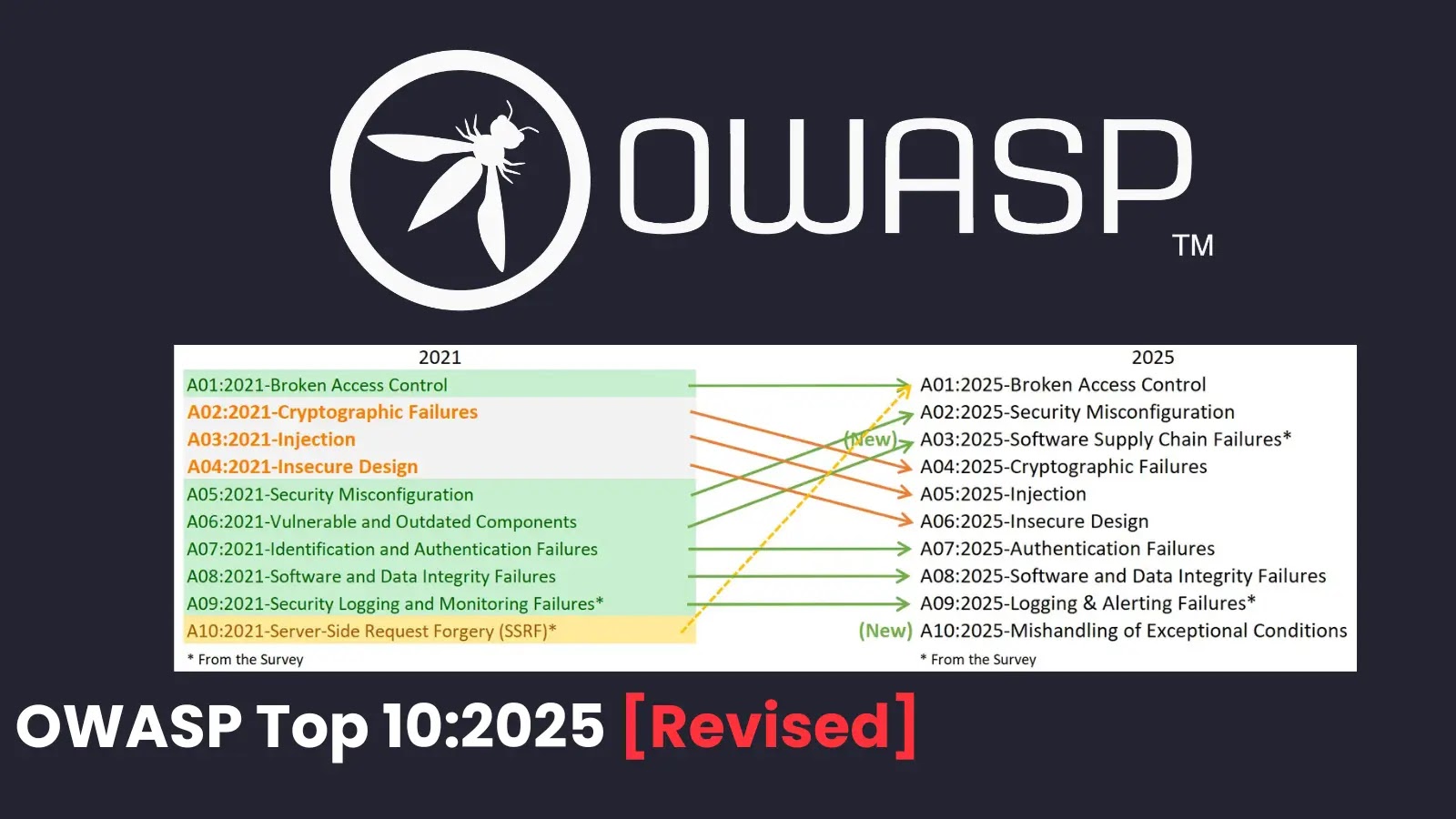
The 2025 Prime 10 options two recent entries: A03:2025 – Software program Provide Chain Failures and A10:2025 – Mishandling of Distinctive Circumstances.
The previous expands on the 2021’s Weak and Outdated Parts, encompassing broader ecosystem dangers like dependencies, construct methods, and distribution infrastructure.
This class, which incorporates 5 Widespread Weak spot Enumerations (CWEs), topped group considerations regardless of restricted testing information, underscoring its excessive exploit and influence potential from CVEs.
A10:2025 introduces 24 CWEs targeted on improper error dealing with, logical flaws, and insecure failure states, reminiscent of failing open throughout irregular situations.
Beforehand scattered below “poor code high quality,” this class addresses how mishandled exceptions can expose delicate information or allow denial-of-service assaults.
In the meantime, A01:2021 – Server-Aspect Request Forgery (SSRF) has been merged into A01:2025 – Damaged Entry Management, which retains its high spot with 40 CWEs affecting 3.73% of examined purposes on common.
Different shifts embrace A02:2025 – Safety Misconfiguration rising to second place (from fifth in 2021), impacting 3.00% of apps resulting from rising configuration complexities.
A04:2025 – Cryptographic Failures dropped to fourth, whereas A05:2025 – Injection and A06:2025 – Insecure Design every fell two spots. Authentication Failures (A07) noticed a reputation tweak for precision, and Logging & Alerting Failures (A09) emphasised actionable alerts over mere monitoring.
RankCategory CodeNameSummaryChange from 20211A01:2025Broken Entry ControlFlaws permitting attackers to bypass authorization or achieve unauthorized entry to information or capabilities. Consists of 40 CWEs, affecting 3.73% of examined purposes on common.Maintains #1; SSRF (A10:2021) consolidated into this class.2A02:2025Security MisconfigurationWeak default settings, uncovered companies, or inconsistent safety controls throughout environments. Impacts 3.00% of purposes.Moved up from #5 resulting from elevated configuration complexity.3A03:2025Software Provide Chain FailuresVulnerabilities in dependencies, CI/CD methods, construct processes, and distribution infrastructure. Covers 5 CWEs with excessive exploit scores.New; expands A06:2021 Weak and Outdated Parts.4A04:2025Cryptographic FailuresInsecure or outdated encryption practices resulting in delicate information publicity or system compromise. Consists of 32 CWEs, affecting 3.80% of apps.Dropped from #2.5A05:2025InjectionInput validation flaws like SQL, OS command, or XSS injections. Related to 38 CWEs and quite a few CVEs.Dropped from #3.6A06:2025Insecure DesignRisks from poor architectural choices or insufficient menace modeling throughout design.Dropped from #4; exhibits trade enhancements in safe design.7A07:2025Authentication FailuresIssues in login, password insurance policies, or session dealing with enabling unauthorized entry. Covers 36 CWEs.Maintains #7; renamed from Identification and Authentication Failures.8A08:2025Software or Information Integrity FailuresFailures to confirm integrity of software program, code, or information, permitting tampering. Focuses on lower-level belief boundaries.Maintains #8; minor concentrate on integrity verification.9A09:2025Logging & Alerting FailuresGaps in monitoring, logging, or alerting that allow assaults go undetected.Maintains #9; renamed to emphasise alerting over simply logging.10A10:2025Mishandling of Distinctive ConditionsImproper error dealing with, logical flaws, or insecure failure states exposing information or inflicting DoS. Consists of 24 CWEs.New class; beforehand below poor code high quality.OWASP Prime 10 2025 (Desk: Cybersecuritynews.com)
A visible mapping diagram illustrates these evolutions, displaying arrows from 2021 classes like SSRF and Weak Parts to their 2025 counterparts, with new additions branching out.
OWASP Prime 10 2025 Classification Methodology
OWASP’s method blends information from over 175,000 CVEs mapped to 643 CWEs, prioritizing prevalence over frequency, specializing in apps with not less than one occasion per CWE.
This version analyzed 589 CWEs throughout classes, averaging 25 every, capped at 40 for practicality, to assist language-specific coaching. Group surveys elevated the visibility of underrepresented dangers, balancing historic information with frontline insights from practitioners.
Exploitability and influence scores drawn from CVSS v2, v3, and v4, revealing shifts like greater influence weighting in newer variations. The consequence: a forward-looking record emphasizing systemic vulnerabilities in fashionable, cloud-native environments.
This replace alerts a maturing subject, with enhancements in areas like menace modeling evident in Insecure Design’s slide.
Challenges like entry management points, present in 9 out of 10 safety checks, nonetheless require shut consideration. Organizations ought to embrace these of their DevSecOps processes, prioritizing provide chain checks and robust error dealing with.
As OWASP welcomes suggestions till November 20, 2025, the ultimate model is anticipated to be additional refined earlier than its full adoption in 2026.
This Prime 10 record not solely supplies steering for remediation but in addition promotes secure-by-design rules, serving to organizations navigate an more and more complicated menace panorama.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.