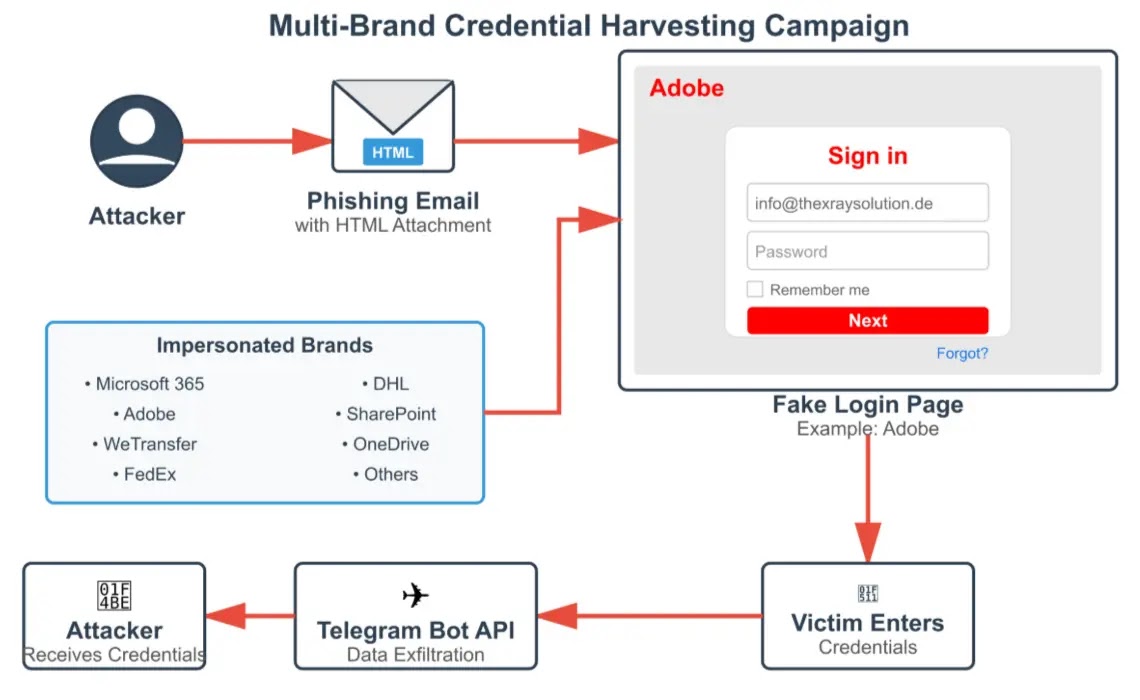
A complicated phishing marketing campaign has emerged, concentrating on organizations throughout Central and Japanese Europe by impersonating authentic international manufacturers to deceive customers into surrendering their login credentials.
The assault makes use of self-contained HTML recordsdata delivered as e mail attachments, eliminating the necessity for exterior server internet hosting or suspicious URLs that conventional safety programs sometimes detect.
As soon as opened, these attachments current convincing faux login pages for manufacturers together with Microsoft 365, Adobe, WeTransfer, FedEx, and DHL, making a seamless consumer expertise designed to bypass typical e mail safety controls.
The assault methodology demonstrates a transparent understanding of regional enterprise practices.
Menace actors distribute phishing emails posing as authentic clients or enterprise companions, requesting quotations or bill confirmations by RFC-compliant filenames equivalent to RFQ_4460-INQUIRY.HTML.
This focused strategy focuses on industries with common procurement workflows, together with agriculture, automotive, building, and schooling sectors, primarily within the Czech Republic, Slovakia, Hungary, and Germany.
Cyble safety analysts recognized that the marketing campaign’s success depends on embedded JavaScript inside HTML attachments that captures credentials and transmits them on to attacker-controlled Telegram bots fairly than conventional command-and-control servers.
Upon execution, victims encounter a rigorously replicated login interface displaying brand-authentic branding with blurred background photographs for added legitimacy.
Marketing campaign Overview
The credential seize mechanism features by studying type subject values and setting up API requests to ship stolen knowledge instantly by the Telegram Bot API.
Technical evaluation reveals two distinct implementation approaches amongst analyzed samples. The primary variant implements CryptoJS AES encryption for obfuscation whereas capturing e mail addresses, passwords, IP addresses, and user-agent data earlier than redirecting victims to authentic firm domains.
Marketing campaign Overview (Supply – Cyble)
The second pattern employs extra superior anti-forensics methods, blocking keyboard combos together with F12, Ctrl+U/S/C/A/X, and right-click context menus to forestall code inspection and evaluation.
The exfiltration operate demonstrates technical sophistication by using the native Fetch API for cleaner code implementation fairly than jQuery dependencies.
The JavaScript constructs POST requests containing harvested credentials despatched through HTTPS to api.telegram.org/bot endpoints with hardcoded bot tokens and chat IDs embedded instantly within the payload.
This strategy intentionally avoids suspicious community patterns whereas sustaining operational resilience by decentralized bot infrastructure.
Organizations ought to prioritize deploying HTML attachment controls and implementing content material inspection insurance policies to dam or sandbox probably malicious HTML recordsdata earlier than supply to finish customers.
Safety groups are suggested to hunt for api.telegram.org POST exercise originating from shopper programs and conduct retroactive menace hunts for recognized indicators to evaluate whether or not credentials have been compromised.
Comply with us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most well-liked Supply in Google.