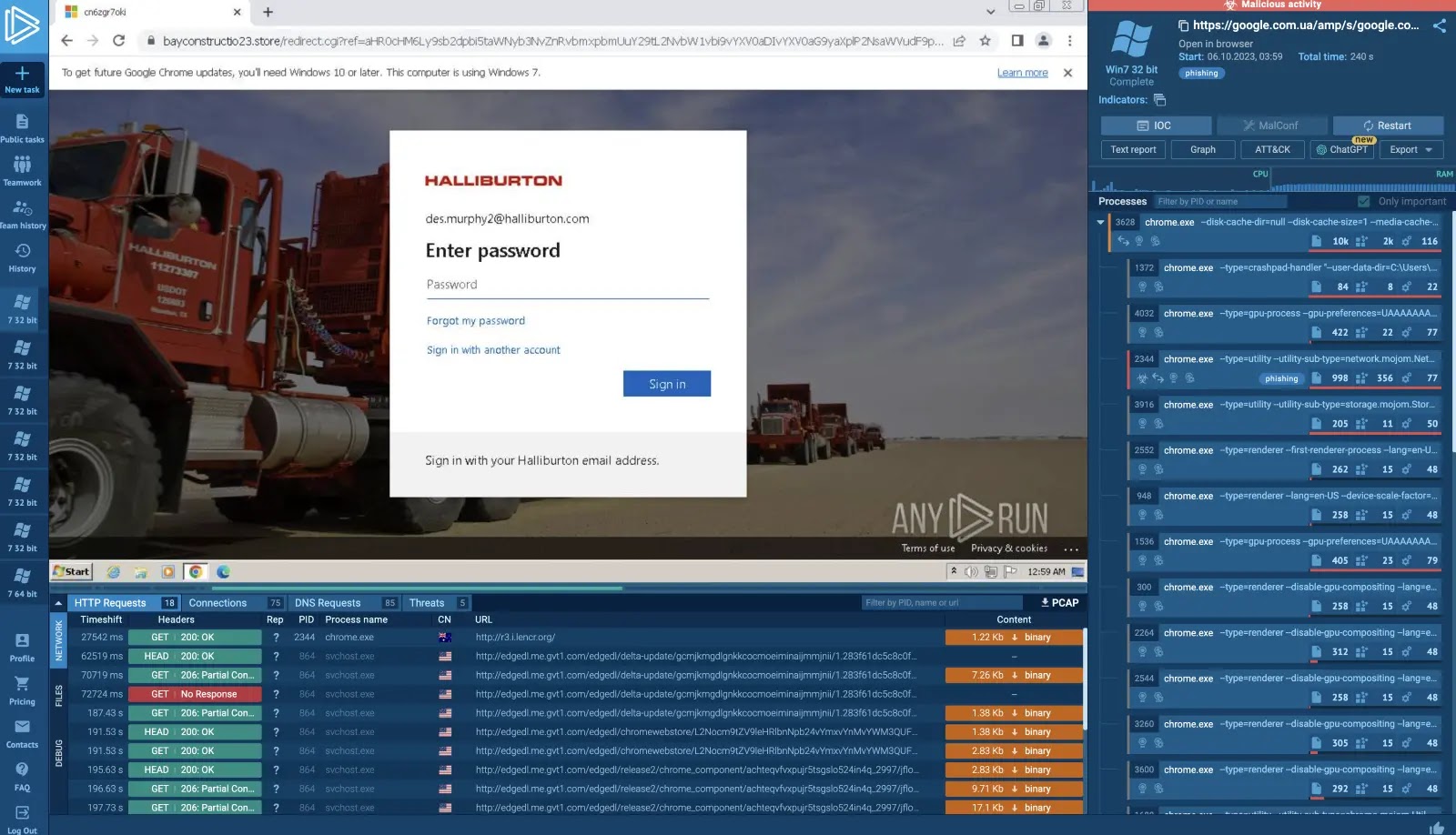
ANY.RUN consultants not too long ago uncovered a brand new XWorm marketing campaign that makes use of steganography to hide malicious payloads inside seemingly innocent PNG photographs.
What seems to be an odd graphic truly comprises encrypted loaders that execute fully in reminiscence, permitting the malware to bypass most conventional detection strategies and signature-based defenses.
Let’s break down how this assault works and what analysts and hunters ought to search for.
Assault Overview with Actual-World Instance
The an infection begins with a malicious JavaScript installer named PurchaseOrder_25005092.JS, delivered by way of phishing emails and internet pages (T1566.001).
The script is obfuscated utilizing an Instantly Invoked Operate Expression (IIFE) sample (T1027) and writes three staged recordsdata to: C:UsersPUBLIC
These recordsdata are named:
Whereas the .png extension suggests photographs, these will not be picture recordsdata. As a substitute, they act as storage containers for Base64-encoded and AES-encrypted payloads (T1036.008); a standard trick to keep away from fast signature-based detection.
You’ll be able to view the complete assault chain and obtain an actionable evaluation report from a real-world run inside ANY.RUN’s interactive sandbox:
View Latest Assault Hiding XWorm in PNG
Steganography assault found inside ANY.RUN sandbox
See each stage of execution unfold in seconds, extract IOCs robotically, and remodel hidden malware conduct into clear, shareable insights.
Get 14-Day Trial of ANY.RUN
Execution Chain Breakdown: What Analysts Must Know
Under is a concise, step-by-step breakdown of the execution chain to assist analysts shortly determine key artifacts and pivot factors.
Observe every stage to see the place to hunt, which logs to examine, and which indicators to extract for detection and response.
Persistence and setup
The JavaScript creates a scheduled process (T1053.005) to keep persistence after reboot. It checks for required artifacts and recreates them utilizing lengthy Base64 blobs and AES-encrypted strings (T1027.013).
Obfuscated batch staging (Kile.cmd)
Kile.cmd comprises heavy obfuscation: variable noise, percent-substitutions, and chunked Base64 fragments. At runtime it reassembles instructions and launches the PowerShell loader (T1059).
Two-stage PowerShell loader
Stage 1 – Command runner: Reads Mands.png, Base64-decodes and AES-decrypts it, then decodes the contained instructions and executes them through Invoke-Expression (IEX).
Stage 2 – In-memory meeting loader: Reads Vile.png, Base64-decodes and AES-decrypts it to uncooked bytes, then masses a .NET meeting instantly into reminiscence and invokes its entry level (T1620). The mixed result’s a fileless, in-memory loader that launches XWorm.
XWorm execution chain with hidden PNG
Professional Risk Looking Ideas: Detecting Fileless and Steganographic Loaders
Under is a targeted guidelines for analysts and hunters to determine steganography-backed, in-memory loaders like XWorm. Use these steps to identify uncommon patterns early and validate findings by way of behavioral evaluation:
Examine picture recordsdata: Scan .png and .jpg recordsdata for unusually lengthy Base64 strings, textual content chunks, or non-image knowledge. Excessive text-to-binary ratios or embedded AES-encrypted sections typically point out hidden payloads.
Monitor PowerShell exercise: Observe instructions utilizing Invoke-Expression, FromBase64String, or AES routines. Correlate these with script origins like wscript.exe or .cmd recordsdata to identify reflective execution and in-memory loaders.
Correlate scheduled process creation: Search for duties created by JavaScript or batch scripts from person directories somewhat than system paths. Such entries typically point out persistence after preliminary compromise.
Use dynamic evaluation: Static scans miss many steganographic loaders. Run suspicious scripts and recordsdata in an interactive sandbox like ANY.RUN to observe decryption, staging, and reminiscence execution in actual time, and extract IOCs from every stage.
How a Sandbox Speeds Up Detection in Steganographic Assaults
Steganographic loaders like XWorm depend on multi-stage execution and memory-only payloads, which makes them almost invisible to static scanners.
A sandbox surroundings adjustments that by exhibiting what’s truly taking place underneath the floor; file writes, decryption routines, and PowerShell instructions executed in actual time.
With ANY.RUN’s interactive sandbox, analysts can:
Watch the complete chain unfold; from the preliminary JavaScript dropper to in-memory execution.
Extract and visualize IOCs comparable to decoded scripts, file paths, and registry modifications.
Verify persistence and C2 exercise with out ready for signatures or EDR alerts.
This degree of visibility turns a stealthy, fileless an infection right into a clear, traceable course of, serving to menace hunters reply sooner and with evidence-based readability.
Flip Complicated Assaults into Clear Proof in Seconds
Attackers are getting higher at mixing in; the one dependable protection is to observe their conduct, not simply their dropped recordsdata.
In almost 90% of circumstances, ANY.RUN reveals full assault conduct in underneath 60 seconds, turning fleeting, fileless exercise into concrete proof analysts can act on instantly.
Key advantages for analysts & menace hunters:
Actual-time visibility for sooner choices: Immediately see how loaders unpack, decrypt, and execute with out ready for static scans or vendor signatures.
Fewer false positives: Behavioral context makes it straightforward to differentiate actual threats from benign automation or scripts.
Finish-to-end understanding: Watch how every course of connects, what recordsdata are written, and the way persistence is achieved.
Time financial savings in triage and investigation: Full evaluation and IOC extraction in minutes, not hours.
Seamless workflow integration: Push outcomes on to SIEM, SOAR, or case administration instruments by way of ready-made connectors.
Collaboration made straightforward: Share reside classes, findings, and visible reviews throughout groups for faster consensus.
Steady studying and searching: Mapped MITRE ATT&CK TTPs and decoded artifacts enrich detection logic and menace intelligence feeds.
Able to see it in motion? Speak to ANY.RUN consultants and uncover how interactive evaluation helps your workforce discover and cease threats static instruments miss.