Menace actors are actively exploiting a essential authentication bypass vulnerability in Fortinet’s FortiWeb internet software firewall (WAF) worldwide, prompting defenders to intensify vigilance.
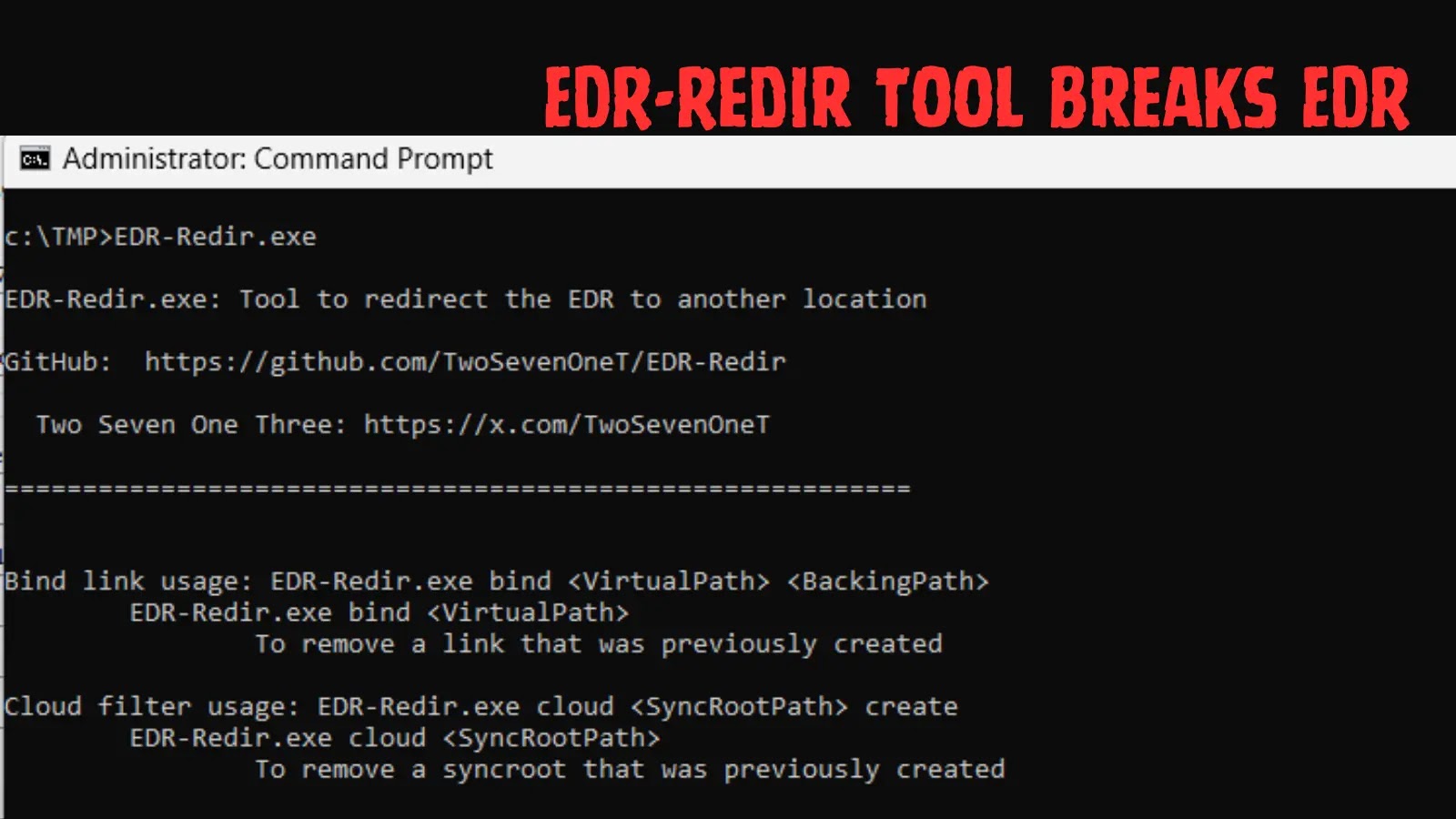
Researchers at watchTowr Labs have responded by releasing a Detection Artefact Generator script, designed to assist organizations scan their environments for susceptible FortiWeb home equipment and mitigate dangers swiftly.
The vulnerability, tracked as CVE-2025-52970, stems from improper parameter dealing with in FortiWeb, enabling unauthenticated distant attackers to log in as any current person by way of crafted requests.
With a CVSS rating of seven.7, it requires some personal data of the machine however poses extreme dangers, together with privilege escalation and potential distant code execution on affected techniques.
Fortinet patched the flaw in variations 8.0.2 and later, however in-the-wild assaults have surged since a partial proof-of-concept surfaced publicly in August 2025, focusing on uncovered FortiWeb situations indiscriminately.
Safety companies report dozens of compromises, underscoring the urgency for quick patching amid ongoing exploitation campaigns.
WatchTowr Labs’ open-source device, hosted on GitHub at watchTowr-vs-Fortiweb-AuthBypass, simplifies detection by simulating the bypass mechanism. The Python script generates a singular username and password (e.g., “35f36895”) and sends an exploit payload to the goal IP, comparable to python watchTowr-vs-Fortiweb-AuthBypass.py 192.168.1.99.
If profitable, it confirms vulnerability by creating a short lived person, alerting directors to remediate. Authored by Sina Kheirkhah (@SinSinology) and Jake Knott (@inkmoro), the script targets FortiWeb variations under 8.0.2, with specifics accessible by way of FortiGuard Labs PSIRT.
Organizations ought to prioritize scanning internet-facing home equipment, making use of patches, and monitoring for anomalous logins. As provide chain assaults evolve, instruments like this empower proactive protection in a menace panorama the place WAFs sarcastically turn out to be entry factors.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.