The rise of cryptocurrency has created new alternatives for cybercriminals to use unsuspecting customers.
Attackers at the moment are disguising the infamous DarkComet distant entry trojan as Bitcoin-related purposes, focusing on cryptocurrency fanatics who obtain instruments from unverified sources.
This malware marketing campaign demonstrates how outdated threats proceed to resurface with trendy social engineering methods.
DarkComet RAT is a widely known distant entry trojan that permits attackers to realize full management over contaminated techniques.
Regardless of being discontinued by its creator years in the past, the malware continues to flow into in underground boards and stays extremely efficient.
It supplies attackers with intensive capabilities together with keystroke logging, file theft, webcam surveillance, and distant desktop management.
These options make it notably harmful for cryptocurrency customers, as stolen credentials can lead on to monetary losses.
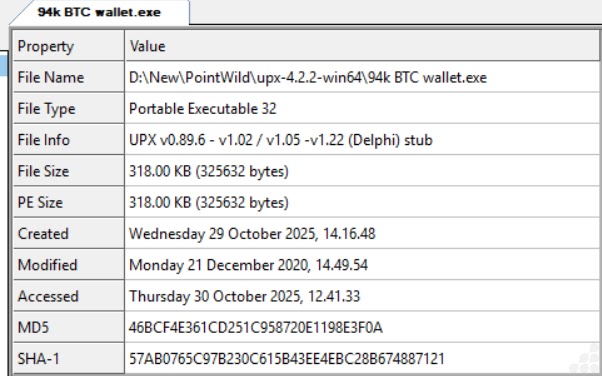
The malicious file analyzed on this marketing campaign was distributed as a compressed RAR archive containing an executable disguised as “94k BTC pockets.exe.”
This supply methodology helps attackers bypass e mail filters and reduces detection charges. The executable was full of UPX (Final Packer for Executables) to additional evade antivirus software program and conceal its true nature from safety evaluation.
Level Wild safety analysts recognized the malware after investigating suspicious Bitcoin-related purposes. The analysis crew found that after extracted and executed, the pretend Bitcoin software instantly prompts DarkComet’s full capabilities.
As a substitute of offering any reliable cryptocurrency performance, the malware begins establishing persistence on the contaminated system and makes an attempt to speak with its command-and-control server.
Technical Breakdown and An infection Mechanism
The malware establishes persistence by copying itself to %AppDatapercentRoamingMSDCSCexplorer.exe and making a registry key beneath HKCUSoftwareMicrosoftWindowsCurrentVersionRun.
File Information picture (Supply – Level Wild)
This ensures the malware executes routinely each time the system restarts. This reveals the file data of the compressed RAR archive, whereas the one under reveals the UPX packing construction seen in CFF Explorer.
UPX Packed (Supply – Level Wild)
Evaluation revealed the pattern’s embedded configuration containing vital operational particulars.
The malware makes use of a mutex named DC_MUTEX-ARULYYD to forestall a number of cases from working concurrently.
Community evaluation confirmed tried connections to the command-and-control server at kvejo991.ddns.internet over TCP port 1604.
Though the C2 server was offline throughout testing, the repeated connection makes an attempt confirmed lively beaconing conduct per DarkComet operations.
The unpacked executable revealed a number of commonplace PE sections, together with .textual content, .knowledge, and .idata.
The malware injects its payload into reliable Home windows processes like notepad.exe to carry out keylogging and display seize whereas remaining hidden.
Captured keystrokes are saved in log recordsdata with names like “2025-10-29-4.dc” earlier than being exfiltrated by the C2 channel.
File hashes for detection embrace SHA256: 11bf1088d66bc3a63d16cc9334a05f214a25a47f39713400279e0823c97eb377 for the compressed archive and SHA256: 5b5c276ea74e1086e4835221da50865f872fe20cfc5ea9aa6a909a0b0b9a0554 for the packed executable.
Customers ought to keep away from downloading cryptocurrency instruments from untrusted sources and preserve up to date safety software program to detect such threats successfully.
Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most popular Supply in Google.