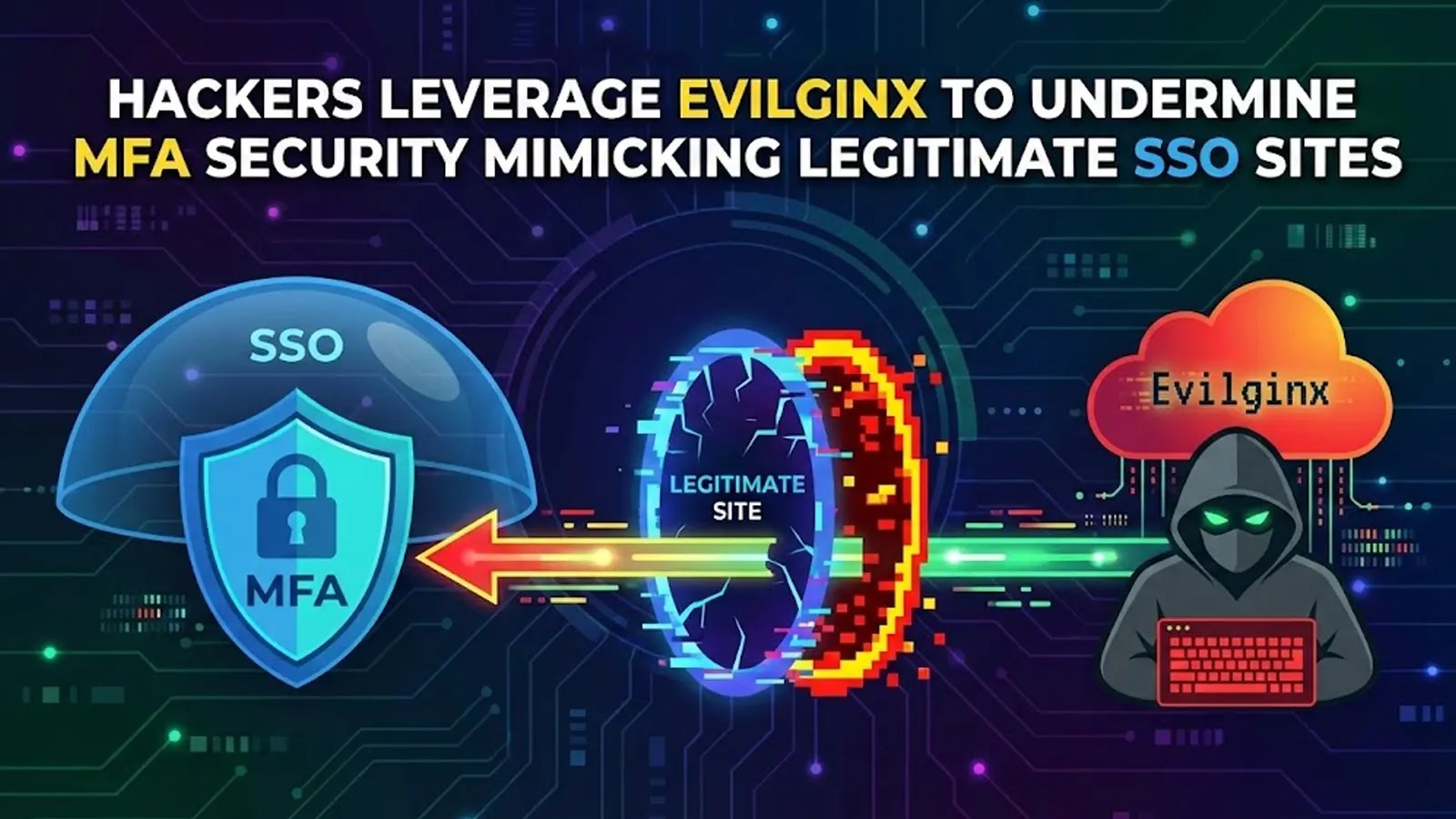
Phishing assaults proceed to be one of the vital persistent threats focusing on organizations worldwide.
Cybercriminals are continuously bettering their strategies to steal delicate data, and a lately found phishing equipment demonstrates simply how superior these operations have develop into.
This explicit framework was designed to impersonate the Italian IT and net providers supplier Aruba S.p.A., an organization that serves over 5.4 million clients throughout Italy’s digital infrastructure.
By focusing on such a extensively trusted service supplier, attackers may acquire entry to vital enterprise property, together with hosted web sites, area controls, and e mail programs.
The phishing marketing campaign begins with spear-phishing emails that create urgency by warning victims about expiring providers or failed funds.
These messages include hyperlinks to faux login pages that intently mimic the official Aruba.it webmail portal.
What makes this assault notably intelligent is using pre-filled login URLs that mechanically populate the sufferer’s e mail deal with within the login kind.
This small element provides a layer of authenticity that makes targets much less suspicious and extra prone to enter their passwords.
Group-IB safety researchers recognized this refined phishing framework via their ongoing monitoring of underground legal ecosystems.
The equipment represents greater than only a faux webpage. It features as an entire, automated platform constructed for effectivity and stealth, using a number of strategies to evade detection and maximize credential theft.
In contrast to primary phishing makes an attempt, this method makes use of CAPTCHA filtering to dam safety scanners and Telegram bots to ship stolen information to attackers immediately.
Multi-Stage Credential Harvesting Course of
The assault unfolds via 4 rigorously designed phases that systematically extract credentials and monetary data.
First, victims encounter a CAPTCHA problem that serves as an anti-bot filter, guaranteeing solely human targets proceed to the precise phishing pages.
After passing this test, victims land on a convincing reproduction of the Aruba login web page, the place they enter their username and password, that are despatched to the attacker instantly.
The method continues with a faux fee web page requesting bank card particulars for a small price, usually round €4.37, offered as a service renewal cost.
As soon as card data is submitted, victims are offered with a fraudulent 3D Safe verification web page that captures the one-time password despatched by their financial institution.
This ultimate piece of knowledge offers attackers the whole lot wanted to authorize real-time fraudulent transactions.
All through this course of, all stolen information is exfiltrated to Telegram chats that function exfiltration channels, offering attackers with immediate notifications.
After finishing the phases, victims are redirected to the authentic Aruba web site, remaining unaware that their data was compromised.
This operation highlights the rising pattern of phishing-as-a-service, the place pre-built kits dramatically decrease technical obstacles and allow widespread credential theft at an industrial scale.
Observe us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates, Set CSN as a Most well-liked Supply in Google.