Nov 19, 2025Ravie LakshmananVulnerability / Community Safety
Fortinet has warned of a brand new safety flaw in FortiWeb that it mentioned has been exploited within the wild.
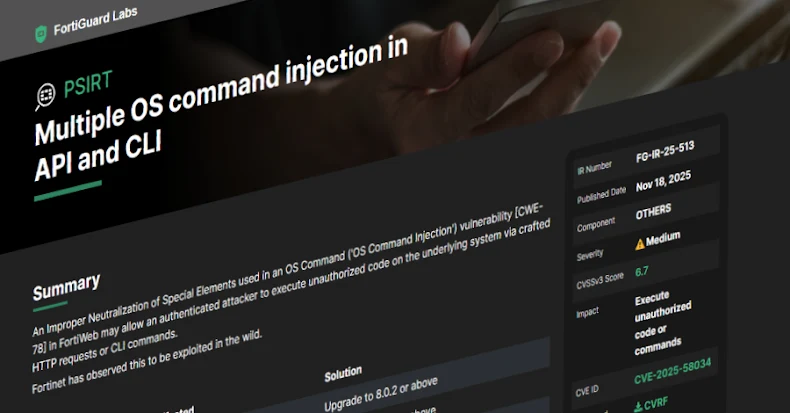
The medium-severity vulnerability, tracked as CVE-2025-58034, carries a CVSS rating of 6.7 out of a most of 10.0.
“An Improper Neutralization of Particular Components utilized in an OS Command (‘OS Command Injection’) vulnerability [CWE-78] in FortiWeb could enable an authenticated attacker to execute unauthorized code on the underlying system by way of crafted HTTP requests or CLI instructions,” the corporate mentioned in a Tuesday advisory.
In different phrases, profitable assaults require an attacker to first authenticate themselves via another means and chain it with CVE-2025-58034 to execute arbitrary working system instructions.
It has been addressed within the following variations –
FortiWeb 8.0.0 via 8.0.1 (Improve to eight.0.2 or above)
FortiWeb 7.6.0 via 7.6.5 (Improve to 7.6.6 or above)
FortiWeb 7.4.0 via 7.4.10 (Improve to 7.4.11 or above)
FortiWeb 7.2.0 via 7.2.11 (Improve to 7.2.12 or above)
FortiWeb 7.0.0 via 7.0.11 (Improve to 7.0.12 or above)
The corporate credited Development Micro researcher Jason McFadyen for reporting the flaw below its accountable disclosure coverage.
Apparently, the event comes days after Fortinet confirmed that it silently patched one other vital FortiWeb vulnerability (CVE-2025-64446, CVSS rating: 9.1) in model 8.0.2.
“We activated our PSIRT response and remediation efforts as quickly as we discovered of this matter, and people efforts stay ongoing,” a Fortinet spokesperson informed The Hacker Information. “Fortinet diligently balances our dedication to the safety of our clients and our tradition of accountable transparency.”
It is at the moment not clear why Fortinet opted to patch the failings with out releasing an advisory. However the transfer has left defenders at an obstacle, successfully stopping them from mounting an enough response.
“When in style know-how distributors fail to speak new safety points, they’re issuing an invite to attackers whereas selecting to maintain that very same info from defenders,” VulnCheck famous final week.