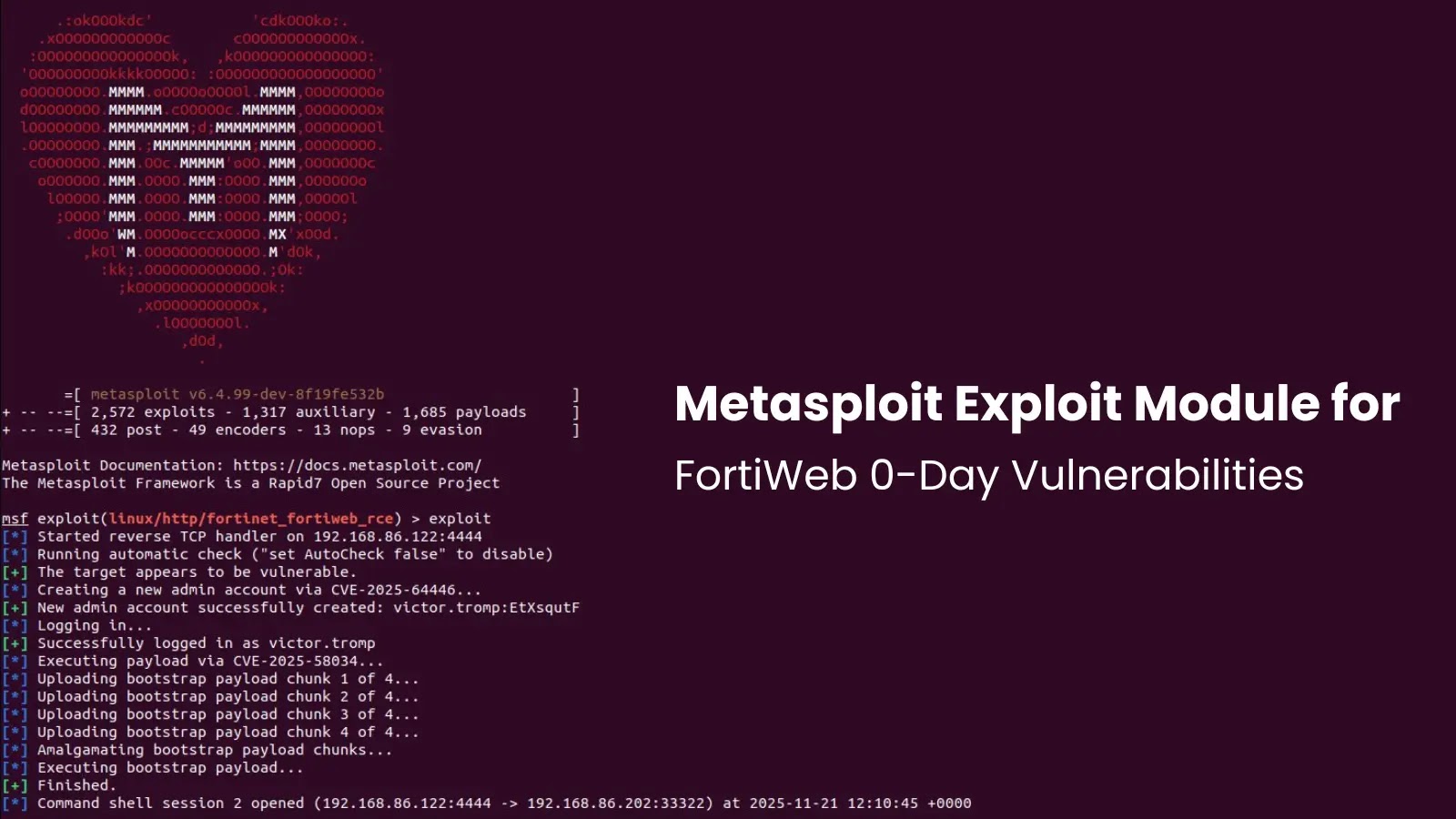
Hackers have begun actively exploiting a important distant code execution (RCE) vulnerability within the common file archiver 7-Zip, placing tens of millions of customers prone to malware an infection and system compromise.
The flaw, tracked as CVE-2025-11001, stems from improper dealing with of symbolic hyperlinks in ZIP archives, permitting attackers to traverse directories and execute arbitrary code on susceptible programs.
First disclosed in October 2025, this vulnerability has a CVSS v3 rating of seven.0, highlighting its excessive severity as a result of potential for widespread exploitation with out requiring elevated privileges.
7-Zip RCE Vulnerability Exploited
CVE-2025-11001 arises in the course of the parsing of ZIP information containing crafted symbolic hyperlinks, which trick 7-Zip into writing information outdoors the meant extraction listing.
This listing traversal can allow attackers to overwrite important system information or inject malicious payloads, resulting in full code execution within the context of the consumer or service account operating the appliance.
Safety researchers at Development Micro’s Zero Day Initiative (ZDI) detailed how an attacker might leverage this to flee sandboxed environments, making it significantly harmful for automated file processing in enterprise settings.
The vulnerability was found by Ryota Shiga of GMO Flatt Safety Inc., in collaboration with their AI-powered AppSec Auditor device, and reported promptly to the 7-Zip builders.
A proof-of-concept (PoC) exploit has since been publicly launched, demonstrating how a malicious ZIP file can abuse symbolic hyperlink dealing with to facilitate arbitrary file writes and, in sure situations, direct RCE.
This PoC has lowered the barrier for risk actors, accelerating real-world assaults noticed within the wild. Notably, exploitation requires minimal consumer interplay; merely opening or extracting a booby-trapped archive suffices, a typical vector in phishing campaigns and drive-by downloads.
This challenge isn’t remoted; 7-Zip model 25.00, launched in July 2025, additionally patches a associated flaw, CVE-2025-11002, which shares the identical symbolic hyperlink mishandling root trigger and carries an similar CVSS rating of seven.0.
Each vulnerabilities have been launched in model 21.02, affecting all prior releases of the open-source device utilized by over 100 million Home windows customers worldwide for compression duties. Early indicators recommend attackers are focusing on unpatched programs in sectors like healthcare and finance, the place file dealing with is routine.
The U.Okay.’s NHS England Digital issued an pressing advisory on November 18, 2025, confirming lively exploitation of CVE-2025-11001, urging rapid updates to mitigate dangers.
Risk actors might use this RCE to deploy ransomware, steal delicate knowledge, or set up persistent backdoors, amplifying the hazard in provide chain assaults the place compromised archives unfold by way of e mail or shared drives.
Organizations counting on 7-Zip for bulk file operations face elevated threats, as automated extractions might silently propagate malware throughout networks.
To counter this risk, customers and organizations should replace 7-Zip to model 25.00 or later, out there from the official web site, which enforces stricter path canonicalization to dam traversal makes an attempt.
The patch prevents symbolic hyperlinks from escaping extraction boundaries, neutralizing each CVE-2025-11001 and CVE-2025-11002. Affected platforms embrace all Home windows variations operating 7-Zip previous to 25.00, with no reported impacts on Linux or macOS ports but.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.