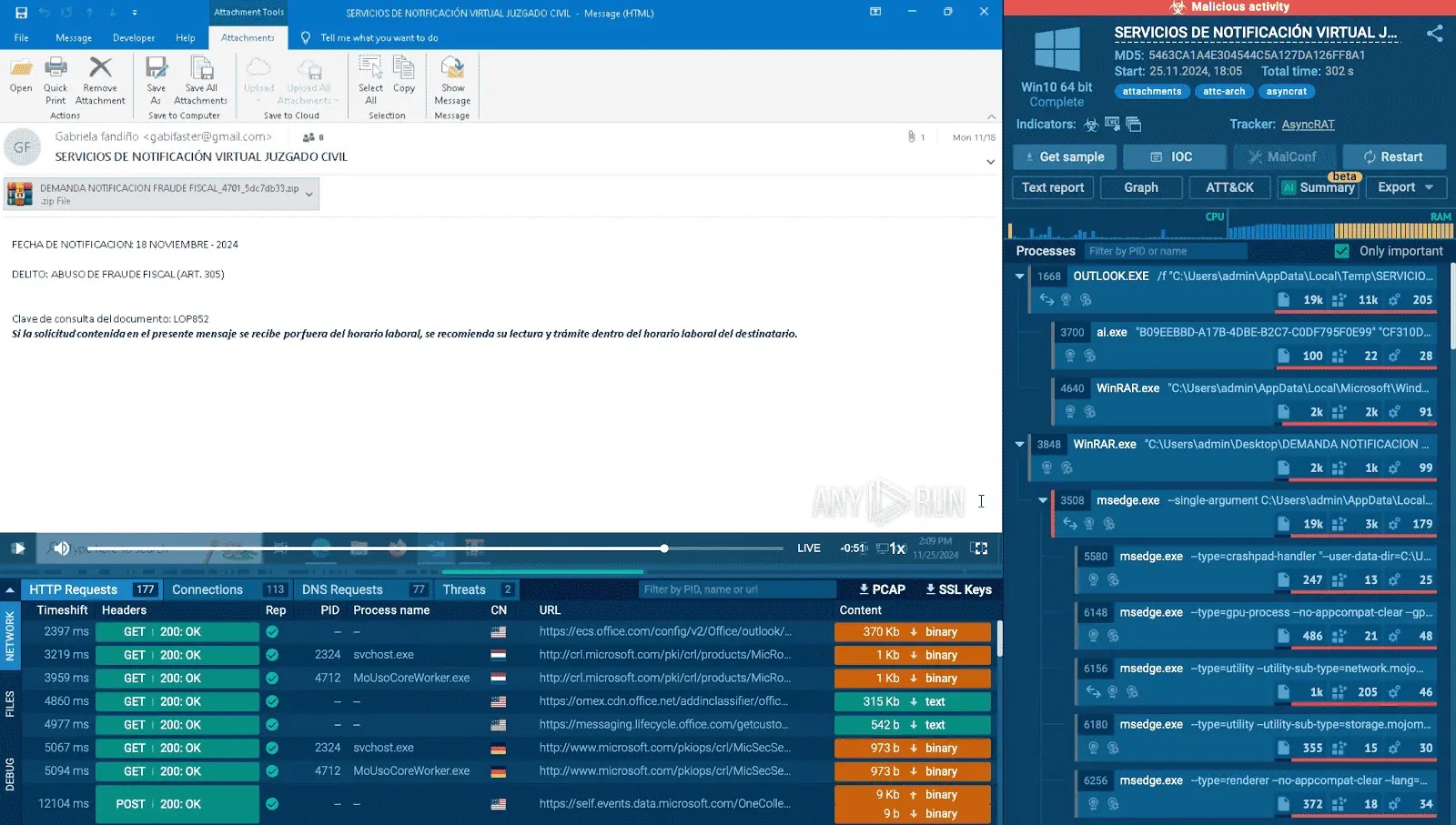
In case your instruments say a hyperlink is clear, do you absolutely belief it?
Most SOC leaders don’t anymore, and for good motive. Phishing has grow to be polished, quiet, and constructed to mix into on a regular basis visitors.
It slips via filters, lands in inboxes unnoticed, and solely reveals its intent after a consumer interacts. By the point the actual habits seems, your defenses have already stepped apart.
That’s the visibility hole attackers are exploiting day-after-day.
Right here’s how your group can shut that hole and lastly see what these “clear” hyperlinks are actually doing.
Why Phishing Is Tougher to Detect Than Ever
Phishing hardly ever appears suspicious anymore. It blends into regular visitors and hides the actual hazard till the final second, lengthy after most instruments cease analyzing.
Right here’s the brand new phishing actuality we’re dwelling in:
It appears clear at first look: Pages and emails now copy actual providers nearly completely.
The dangerous half seems late: Dangerous habits triggers solely after clicks or type inputs.
QR codes bypass filters: Scanners typically can’t learn what’s behind the code, so threats enter unnoticed.
Redirect chains cover the ultimate payload: Every hop appears innocent, whereas the actual web page sits on the finish.
Domains rotate consistently: Brief-lived infrastructure makes blocklists simple to evade.
The Repair: See the Full Phishing Assault, Not the Secure-Wanting First Step
Many SOC groups have already shifted to superior behavioral instruments, particularly interactive sandboxes, as a result of they reveal the components of phishing assaults that conventional controls by no means attain.
As an alternative of stopping on the first “clear” web page, the sandbox follows the whole chain and exhibits the actual habits in minutes.
For instance, ANY.RUN’s sandbox can expose 90% of full phishing chains in below 60 seconds, even when the assault hides or makes use of rediraction as evasion approach.
Examine real-world instance: phishing assault with rediraction strategies
Faux phishing login web page uncovered inside ANY.RUN sandbox in 1 min
A latest case confirmed attackers utilizing ClickUp because the entry level, then quietly redirecting victims via respectable Microsoft microdomains and eventually to an Azure-hosted pretend login web page.
Contained in the sandbox, the entire sequence unfolded mechanically in 1 minute, together with the redirects and credential-harvesting actions.
Get clear, real-time visibility into phishing assaults your instruments at present miss, and see how your group can examine quicker -> Discuss to ANY.RUN consultants
The Secret of the Repair: Interactivity + Automation
Most safety instruments fail to expose fashionable phishing for one easy motive: they will automate, or they will imitate a human, however they can’t do each on the identical time.
That’s precisely the mix at this time’s evasive assaults are constructed to defeat.
Phishing kits now rely closely on human-only actions, clicking via pages, fixing CAPTCHA gates, opening hyperlinks from QR codes, triggering habits with mouse motion, steps that static scanners and automatic crawlers by no means carry out.
Automation alone stops too early.
Handbook evaluation alone is just too sluggish.
The true breakthrough comes from combining each.
That’s why options constructed on interactive automation have grow to be important for SOC groups. As an illustration, ANY.RUN’s interactive sandbox provides analysts one of the best of each worlds:
Automation handles the repetitive duties: It follows redirects, extracts and opens hidden hyperlinks from QR codes, launches the appropriate browser, and solves CAPTCHA gates mechanically.
Interactivity provides analysts management: They will pause the run, comply with suspicious paths, click on via pages, or set off actions at any time when wanted.
ANY.RUN recognized the hyperlink hidden within the QR
This mixture delivers one thing most instruments can’t: full visibility into the whole phishing chain.
It reveals assaults that cover their payload a number of steps deep, depend on human habits, or change relying on who’s visiting. And it does it quick sufficient for analysts to make assured choices with out losing hours recreating the circulate.
The Outcomes SOC Leaders Are Already Seeing
Groups that added an interactive sandbox into their workflow are seeing measurable enhancements throughout their complete response course of.
SOC leaders report:
As much as 58% extra threats recognized total, together with assaults that bypassed different instruments.
94% of customers expertise quicker triage, due to clear behavioral reviews and instantaneous IOCs.
As much as 20% decrease workload for Tier 1, as automation handles the tedious steps.
30% fewer escalations from Tier 1 to Tier 2, as a result of junior analysts can resolve extra instances with richer context.
95% of SOC groups velocity up investigations, supported by collaboration instruments and shared behavioral visibility.
Discuss to ANY.RUN consultants to see how an interactive sandbox can strengthen your group’s detection, investigation velocity, and response workflow.
Free Webinar: SOC Chief’s Playbook – 3 Steps to Sooner MTTR
In order for you a deeper, sensible take a look at how prime SOCs speed up detection and response, ANY.RUN is internet hosting a one-hour session titled “SOC Chief’s Playbook: 3 Steps to Sooner MTTR” on 25 November 2025 at 16:00 CET.
On this session, consultants will break down how main groups:
Minimize MTTR by 21 minutes per incident
Detect new threats earlier with intelligence from 15,000 organizations
Obtain a 3× efficiency enhance by decreasing false positives
Save your seat now to get a transparent, confirmed playbook for dashing up your SOC’s response.