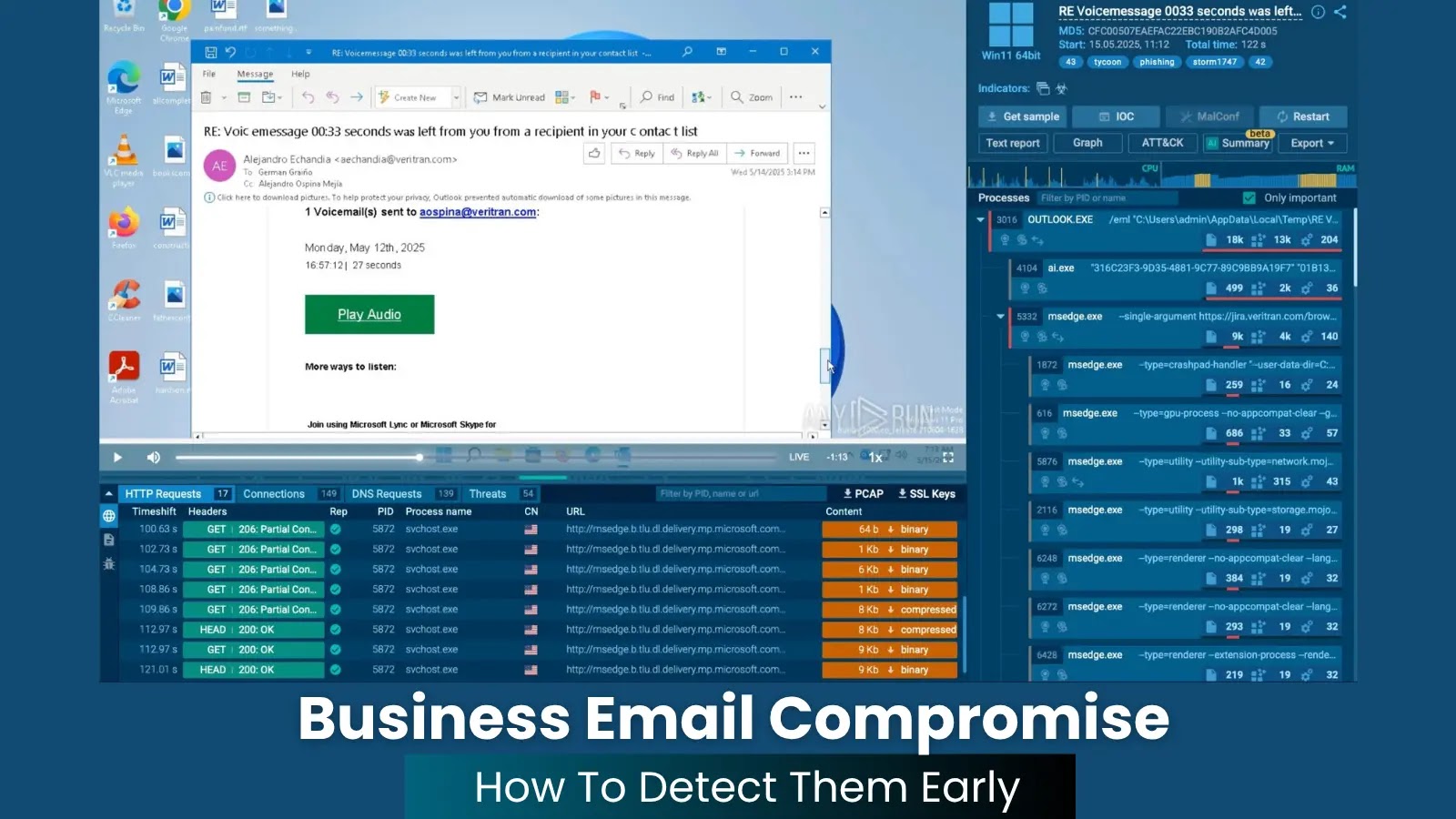
A extremely coordinated reconnaissance marketing campaign that deployed 251 malicious IP addresses in a single-day operation concentrating on cloud-based infrastructure.
The assault, which occurred on Might 8, 2025, demonstrated unprecedented coordination as menace actors leveraged 75 distinct publicity factors to probe weak programs throughout a number of enterprise applied sciences.
Cloud-Based mostly Reconnaissance Operation
The coordinated marketing campaign utilized completely Amazon Net Companies infrastructure, with all 251 IP addresses geolocated to Japan and hosted by AWS cloud providers.
Safety analysts famous the operation’s surgical precision, as each IP handle remained energetic solely in the course of the Might 8 timeframe, with no observable exercise earlier than or after the coordinated surge.
This sample strongly signifies the short-term rental of cloud infrastructure particularly for this reconnaissance operation.
GreyNoise’s overlap evaluation revealed outstanding coordination among the many attacking infrastructure.
Particularly, 295 IP addresses have been scanned for Adobe ColdFusion vulnerabilities (CVE-2018-15961), whereas 265 IPs focused Apache Struts programs (CVE-2017-5638), and 260 IPs probed Elasticsearch implementations (CVE-2015-1427).
Essentially the most important discovering confirmed 251 IPs overlapping throughout all three vulnerability classes, triggering the entire set of 75 GreyNoise detection tags.
Technical evaluation demonstrates this wasn’t random scanning exercise however quite a centrally managed operation.
The infrastructure included IP addresses comparable to 13.112.127.102, 13.113.184.40, and 18.176.55.146, amongst others, within the complete 251-address listing compiled by GreyNoise researchers.
A number of Enterprise Vulnerabilities Focused
The assault marketing campaign systematically focused crucial vulnerabilities throughout numerous expertise stacks, focusing closely on enterprise edge infrastructure.
Major targets included Adobe ColdFusion distant code execution vulnerabilities (CVE-2018-15961), Apache Struts OGNL injection flaws (CVE-2017-5638), and Elasticsearch Groovy sandbox bypass vulnerabilities (CVE-2015-1427).
Further reconnaissance efforts encompassed Oracle WebLogic servers, Apache Tomcat installations, and numerous content material administration programs, together with WordPress, Drupal, and Atlassian Confluence platforms.
The attackers additionally deployed specialised scanning strategies concentrating on IoT units, together with GPON routers (CVE-2018-10561), Netgear wi-fi entry factors, and numerous network-attached storage programs.
Significantly regarding was the give attention to legacy vulnerabilities comparable to Shellshock (CVE-2014-6271) and older Elasticsearch implementations, suggesting attackers particularly focused organizations with delayed patching cycles.
The 2025 Verizon Information Breach Investigations Report had beforehand highlighted edge infrastructure as a crucial danger space, noting regarding developments in time-to-mass-exploit and remediation delays.
Defensive Suggestions
Major suggestions embody reviewing Might 8 safety logs for suspicious exercise, implementing IP blocking for the recognized 251 malicious addresses, and establishing dynamic blocking mechanisms for IPs concentrating on the 75 particular vulnerability classes.
GreyNoise has categorised all 251 IP addresses as malicious and recommends organizations implement automated blocking utilizing iptables instructions comparable to iptables -A INPUT -s [malicious_ip] -j DROP for Linux programs, or equal firewall guidelines for his or her respective infrastructure.
This coordinated marketing campaign displays broader developments in opportunistic however orchestrated scanning operations.
Related reconnaissance patterns have traditionally preceded the invention of zero-day vulnerabilities, as evidenced by current scanning exercise that preceded disclosed vulnerabilities in Ivanti EPMM programs.
Organizations ought to deal with coordinated scanning as an early warning sign and proactively harden uncovered programs in opposition to potential follow-up exploitation makes an attempt.
Attempt in-depth sandbox malware evaluation for your SOC staff. Get ANY.RUN particular provide solely till Might 31 -> Attempt Right here