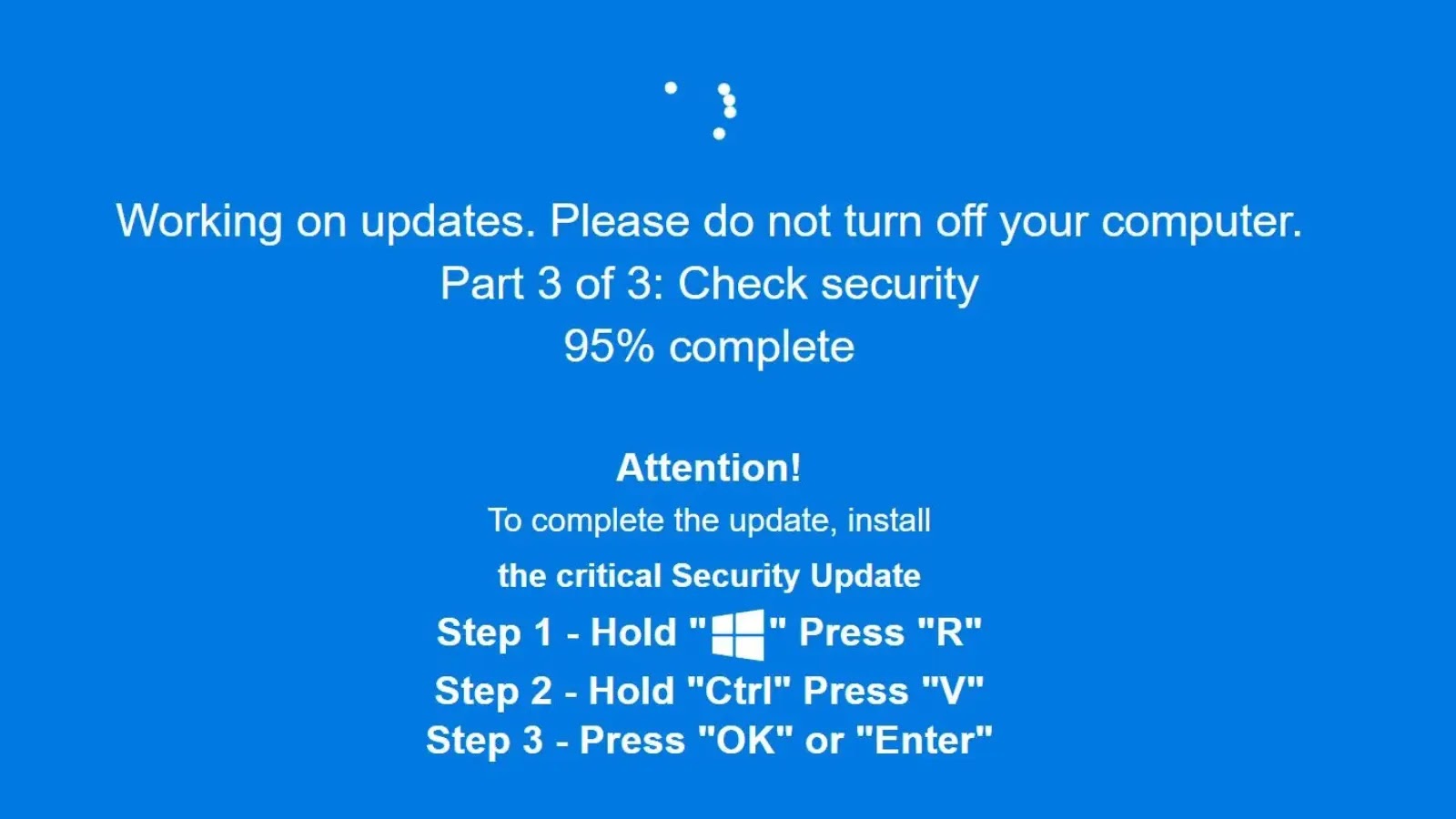
A brand new wave of ClickFix assaults is abusing extremely lifelike pretend Home windows Replace screens and PNG picture steganography to secretly deploy infostealing malware akin to LummaC2 and Rhadamanthys on sufferer methods.
The campaigns depend on tricking customers into manually operating a pre-staged command, turning easy social engineering right into a multi-stage, file-light an infection chain that’s onerous for conventional defenses to identify.
ClickFix is a social engineering method during which an online web page convinces customers to press Win+R, then paste and run a command that has been silently copied to the clipboard.
Earlier lures posed as “Human Verification” or robot-check pages, however newer exercise noticed by Huntress swaps this for a full-screen, blue Home windows Replace-style splash display with convincing progress messages.
As soon as the pretend replace “completes,” the web page instructs customers to comply with the acquainted sample and execute the malicious Run-box command.
That command usually launches mshta.exe with a URL whose second IP octet is hex-encoded, kicking off a staged chain that downloads obfuscated PowerShell and reflective .NET loaders. This strategy leans closely on trusted “dwelling off the land” binaries, making the exercise mix in with respectable Home windows habits.
Malware hidden in PNG pixels
Probably the most distinctive function of this marketing campaign is its use of a .NET steganographic loader that hides shellcode contained in the pixel knowledge of a PNG picture.
As a substitute of appending knowledge, the loader AES-decrypts an embedded PNG useful resource, reads the uncooked bitmap bytes, and reconstructs shellcode from a selected coloration channel, utilizing a customized XOR-based routine to recuperate the payload in reminiscence.
The recovered shellcode is Donut-packed after which injected right into a goal course of akin to explorer.exe by way of dynamically compiled C# code that calls normal Home windows APIs like VirtualAllocEx, WriteProcessMemory, and CreateRemoteThread.
In analyzed instances, this last stage has delivered LummaC2 and, in a separate Home windows Replace cluster, the Rhadamanthys info stealer.
Huntress has tracked ClickFix Home windows Replace clusters since early October, noting repeated use of the IP handle 141.98.80[.]175 and rotating paths akin to /tick.odd, /gpsc.dat, and /one.dat for the primary mshta.exe stage.
Subsequent PowerShell phases have been hosted on domains like securitysettings[.]dwell and xoiiasdpsdoasdpojas[.]com, pointing again to the identical backend infrastructure.
These campaigns continued to seem across the time of Operation Endgame 3.0, which focused Rhadamanthys’ infrastructure in mid-November, disrupting servers and seizing domains linked to the stealer.
Even after the takedown announcement, researchers noticed a number of energetic domains nonetheless serving the Home windows Replace ClickFix lure, although the Rhadamanthys payload itself seemed to be unavailable.
As a result of the assault hinges on person interplay with the Run dialog, one robust management is to disable the Home windows Run field by way of Group Coverage or registry settings (for instance, configuring the NoRun coverage beneath the Explorer key).
Safety groups also needs to use EDR telemetry to look at for explorer.exe spawning mshta.exe, powershell.exe, or different scripting binaries with suspicious command traces.
Person consciousness stays essential: staff needs to be skilled that neither CAPTCHA checks nor Home windows Replace processes will ever require pasting instructions into the Run immediate from an online web page.
Throughout investigations, analysts can additional validate potential ClickFix abuse by reviewing the RunMRU registry key, which information latest instructions executed by way of the Run dialog.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.