Nov 25, 2025Ravie LakshmananMalware / Vulnerability
The risk actor generally known as ToddyCat has been noticed adopting new strategies to acquire entry to company electronic mail information belonging to focus on firms, together with utilizing a customized device dubbed TCSectorCopy.
“This assault permits them to acquire tokens for the OAuth 2.0 authorization protocol utilizing the consumer’s browser, which can be utilized outdoors the perimeter of the compromised infrastructure to entry company mail,” Kaspersky stated in a technical breakdown.
ToddyCat, assessed to be lively since 2020, has a observe document of focusing on numerous organizations in Europe and Asia with numerous instruments, Samurai and TomBerBil to retain entry and steal cookies and credentials from internet browsers like Google Chrome and Microsoft Edge.
Earlier this April, the hacking group was attributed to the exploitation of a safety flaw in ESET Command Line Scanner (CVE-2024-11859, CVSS rating: 6.8) to ship a beforehand undocumented malware codenamed TCESB.
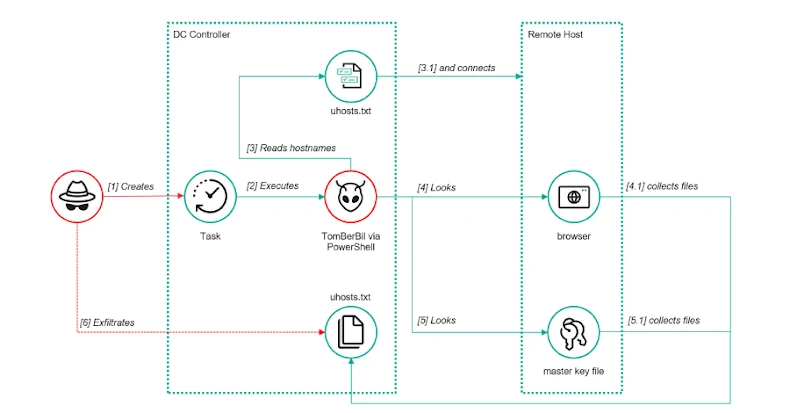
Kaspersky stated it detected a PowerShell variant of TomBerBil (versus C++ and C# variations flagged earlier than) in assaults that came about between Might and June 2024, which comes with capabilities to extract information from Mozilla Firefox. A notable function of this model is that it runs on area controllers from a privileged consumer and may entry browser recordsdata by way of shared community assets utilizing the SMB protocol.
The malware, the corporate added, was launched via a scheduled process that executed a PowerShell command. Particularly, it searches for browser historical past, cookies, and saved credentials within the distant host over SMB. Whereas the copied recordsdata containing the data are encrypted utilizing the Home windows Information Safety API (DPAPI), TomBerBil is provided to seize the encryption key essential to decrypt the information.
“The earlier model of TomBerBil ran on the host and copied the consumer token. Consequently, DPAPI was used to decrypt the grasp key within the consumer’s present session, and subsequently the recordsdata themselves,” researchers stated. “Within the newer server model, TomBerBil copies recordsdata containing consumer encryption keys which might be utilized by DPAPI. Utilizing these keys, in addition to the consumer’s SID and password, attackers can decrypt all copied recordsdata regionally.”
The risk actors have additionally been discovered to entry company emails saved in native Microsoft Outlook storage within the type of OST (brief for Offline Storage Desk) recordsdata utilizing TCSectorCopy (“xCopy.exe”), bypassing restrictions that restrict entry to such recordsdata when the appliance is working.
Written in C++, TCSectorCopy accepts as enter a file to be copied (on this case, OST recordsdata) after which proceeds to open the disk as a read-only gadget and sequentially copy the file contents sector by sector. As soon as the OST recordsdata are written to a path of the attacker’s selecting, the contents of the digital correspondence are extracted utilizing XstReader, an open-source viewer for Outlook OST and PST recordsdata.
One other tactic adopted by ToddyCat includes efforts to acquire entry tokens straight from reminiscence in circumstances the place sufferer organizations used the Microsoft 365 cloud service. The JSON internet tokens (JWTs) are obtained by way of an open-source C# device named SharpTokenFinder, which enumerates Microsoft 365 purposes for plain textual content authentication tokens.
However the risk actor is alleged to have confronted a setback in a minimum of one investigated incident after safety software program put in on the system blocked SharpTokenFinder’s try and dump the Outlook.exe course of. To get round this restriction, the operator used the ProcDump device from the Sysinternals bundle with particular arguments to take a reminiscence dump of the Outlook course of.
“The ToddyCat APT group is consistently growing its strategies and searching for those who would cover exercise to achieve entry to company correspondence throughout the compromised infrastructure,” Kaspersky stated.