Main a Safety Operations Heart has by no means been tougher.
SOC managers as we speak juggle increasing assault surfaces, distant workforces, cloud migrations, and an explosion of safety instruments. All whereas making an attempt to maintain tempo with more and more automated assaults. Day-after-day seems like a mixture of firefighting and long-term planning that by no means absolutely materializes. Beneath this stress, it’s straightforward to imagine that the largest challenges come from no matter assault makes the headlines this week.
However in actuality, the true weak level in lots of SOCs hides deeper within the basis of their operations.
The Normal Suspects: What SOCs Blame for Hassle
When SOC leaders are requested what retains them up at evening, the solutions usually revolve round particular threats and useful resource limitations.
A survey of the shoppers of a cybersecurity options supplier ANY.RUN illustrates their principal issues:
The subsequent zero-day exploit lurking within the shadows, able to bypass all defenses earlier than signatures exist to detect it.
Infamous malware households like ransomware variants that threaten to cripple operations and demand hefty funds.
Superior Persistent Threats (APTs) from nation-state actors with limitless assets and persistence, slowly infiltrating networks.
Novel assault methods that evade conventional detection strategies, exploiting vulnerabilities earlier than they’re even found.
Price range constraints that forestall hiring extra analysts, buying higher instruments, or increasing protection.
These issues are respectable. Every represents an actual threat that may result in expensive breaches.
Nevertheless, focusing completely on these threats misses a extra basic downside that undermines the effectiveness of even the best-resourced SOCs.
The Actual Hole: High quality Menace Intelligence
The issue that quietly undermines detection, investigation, and response is inadequate entry to recent, actionable, context-rich menace intelligence.
SOCs not often fail as a result of analysts lack expertise. They fail as a result of analysts lack readability. With out reliable, up-to-date insights into energetic malware habits, real-world campaigns, and present attacker tooling, SOC groups are compelled to guess.
And guessing is pricey — each in time and in enterprise threat.
The true hole isn’t a specific adversary or a selected assault. It’s the absence of high-quality, repeatedly up to date knowledge that helps analysts perceive what they’re taking a look at and the right way to react.
Three Vital SOC Issues That Menace Intelligence Solves
1. Alert Fatigue and Investigation Burnout
When each alert appears the identical and lacks context, analysts waste hours chasing false positives.
High quality menace intelligence dramatically reduces this burden: Is that this IP related to recognized malware households? What assault methods does it use? Has it been seen in latest campaigns concentrating on comparable organizations?
With enriched menace knowledge, analysts can rapidly triage alerts, distinguishing between noise and real threats. This implies quicker responses to actual incidents.
2. Detection Gaps and Blind Spots
Conventional signature-based detection, firewalls, and endpoint detection can not uncover unknown threats, making it tough for SOCs to defend in opposition to zero-day assaults.
When menace intelligence contains Ways, Methods, and Procedures (TTPs) from latest assaults, SOCs can construct detection guidelines that determine malicious habits reasonably than simply recognized signatures.
This shifts protection from reactive to proactive, catching threats even once they use new infrastructure or modified payloads.
Detect rising threats early with real-time intelligence from Menace Intelligence Feeds -> Request trial to your crew
3. Gradual Incident Response and Investigation Instances
When an alert triggers, velocity issues. However with out correct context, investigations drag on whereas analysts hunt for data throughout a number of sources.
High quality menace intelligence accelerates response by offering all the things analysts want in a single place: associated file hashes to seek for throughout techniques, related domains and IPs to dam, hyperlinks to full sandbox evaluation exhibiting precisely how the menace behaves, and attribution to recognized menace actors or campaigns.
This contextual enrichment transforms investigation workflows from hours of analysis to minutes of decision-making, dramatically decreasing Imply Time to Detect (MTTD) and Imply Time to Reply (MTTR).
Contemporary Intelligence from the Entrance Traces
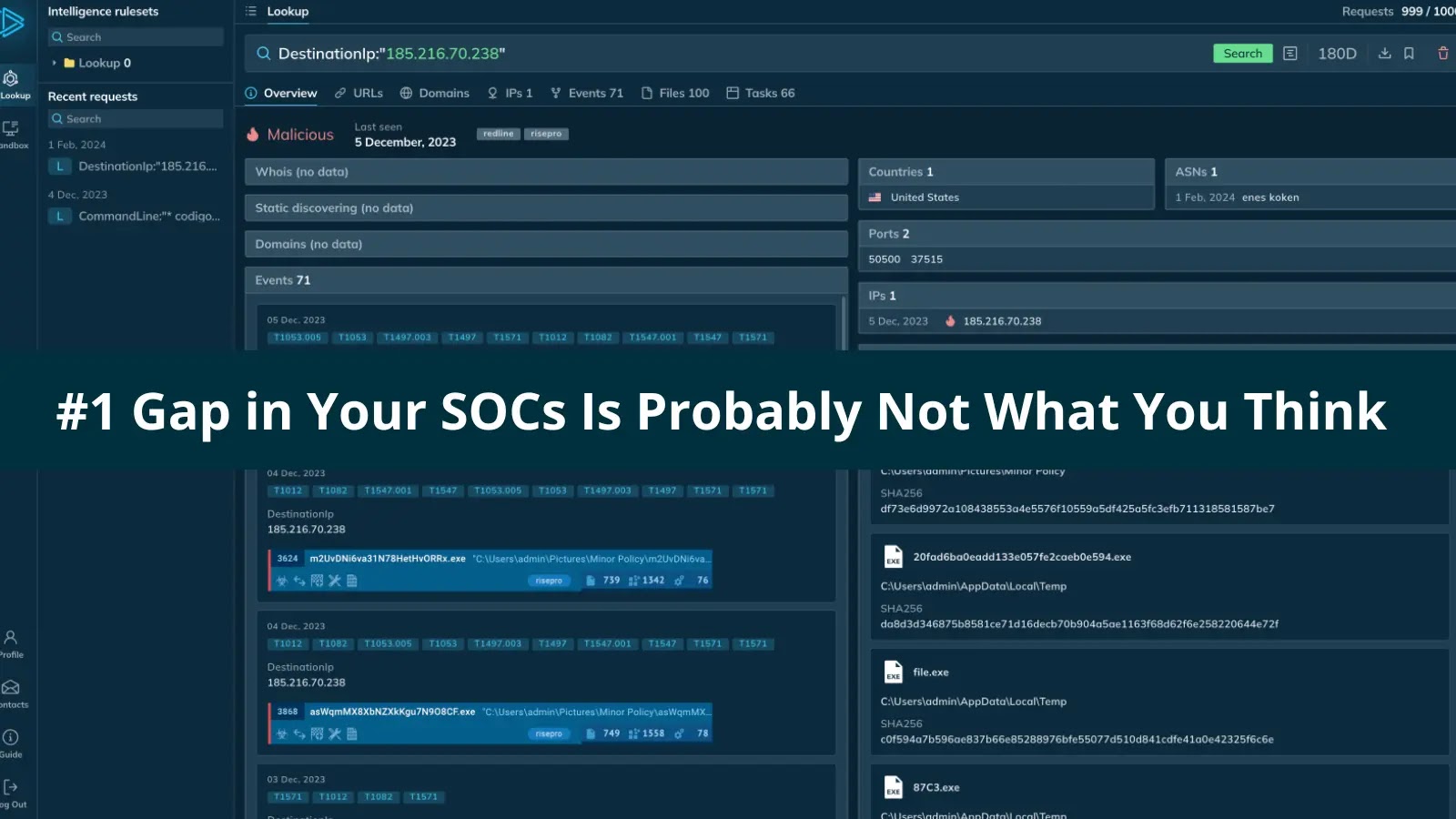
ANY.RUN’s Menace Intelligence Feeds deal with these challenges by offering one thing distinctive within the TI market: real-time indicators extracted from precise malware evaluation periods carried out by a worldwide community of over 15K SOC groups who add and analyze real-world malware and phishing samples day by day.
Menace Intelligence Feeds: IOC and context sources
Key benefits embody:
Stay behavior-driven indicators: IOCs generated by actual executions of energetic malware samples.
Context-rich detections: Every indicator comes with metadata, together with hyperlinks to sandbox periods with behaviors and TTPs.
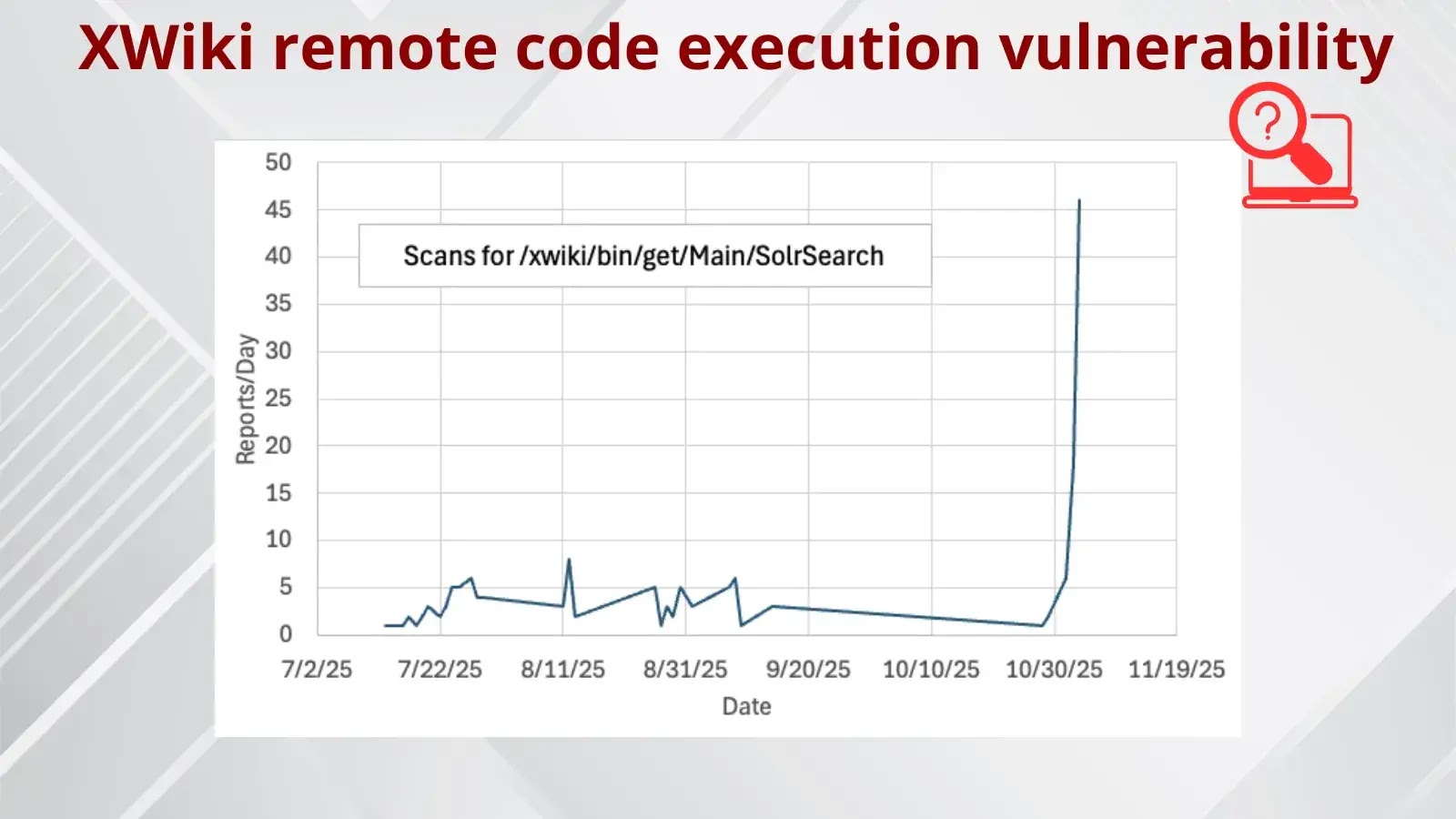
Prompt visibility into rising exercise: Newly uploaded samples set off fast evaluation, permitting the feed to mirror what attackers are utilizing proper now.
Protection throughout many malware households: From commodity stealers and loaders to extra focused threats.
Excessive signal-to-noise ratio: As a result of the info is collected from actual sandbox runs, it avoids inflated or outdated data that clutters many conventional feeds.
All of this leads to intelligence that analysts can belief and act on instantly.
TI Feeds knowledge: fullness and accuracy Implementing ANY.RUN’s Menace Intelligence Feeds delivers measurable enterprise outcomes that stretch past technical metrics:
Scale back incident response prices by enabling quicker, extra assured investigation.
Decrease threat of operational disruption by bettering early detection of energetic threats.
Optimize SOC effectivity so groups spend much less time chasing false leads.
Improve strategic planning by means of visibility into persistent attacker tooling.
Help compliance and audit readiness with evidence-based menace monitoring.
Strengthen safety investments by informing which controls want tuning, updating, or changing.
Menace Intelligence Feeds enterprise advantages
Conclusion
The most important hole in most SOCs isn’t a lacking device or perhaps a lacking individual. it’s lacking knowledge: recent, detailed, actionable intelligence on the precise threats which might be actively concentrating on organizations like yours proper now. By equipping analysts with dependable intelligence drawn from actual malware habits, ANY.RUN’s TI Feeds shut this hole.
They empower groups to reply quicker, get rid of uncertainty, and help enterprise management with clearer insights and stronger outcomes. When a SOC has the fitting intelligence at its core, all the things else, from day-to-day operations to long-term technique, turns into far more practical.
Lower MTTR, broaden menace protection, scale back enterprise dangers -> Get your trial & ask any questions