A important safety vulnerability in Ubiquiti UniFi Shield Cameras might permit attackers to execute arbitrary code remotely.
The flaw, which acquired the very best attainable CVSS rating of 10.0, impacts all digital camera firmware variations 4.75.43 and earlier, prompting an pressing name for customers to replace their techniques instantly.
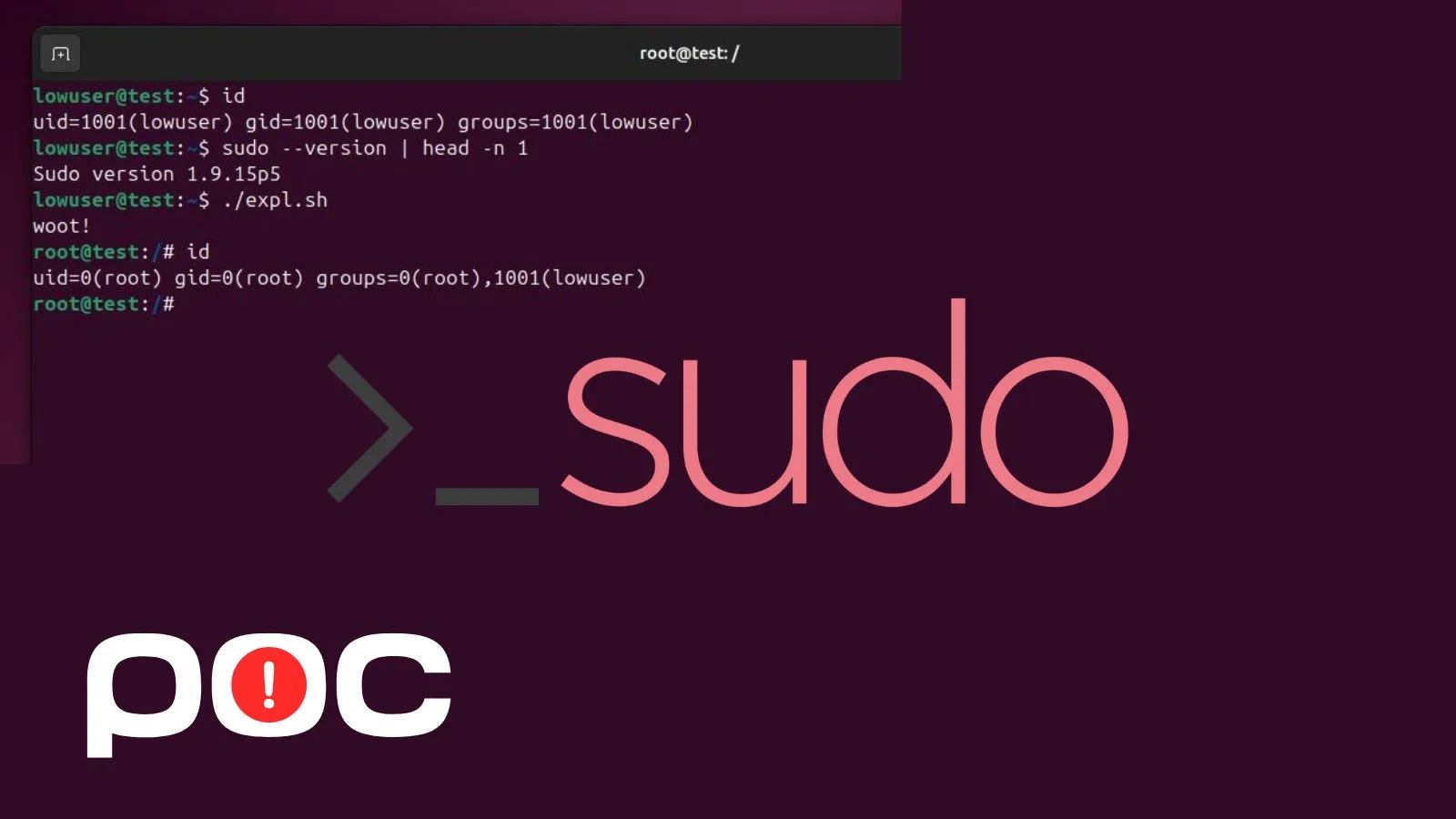
The vulnerability, tracked as CVE-2025-23123, includes a heap buffer overflow within the digital camera firmware that permits distant code execution (RCE) capabilities.
Vital RCE in UniFi Shield Cameras
In line with the Safety Advisory Bulletin launched by Ubiquiti, “A malicious actor with entry to the administration community might execute a distant code execution (RCE) by exploiting a heap buffer overflow vulnerability within the UniFi Shield Cameras.”
Safety researchers observe that reaching an ideal CVSS rating of 10.0 is uncommon, highlighting the important nature of this vulnerability.
The whole CVSS vector – CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H – signifies that the vulnerability requires no consumer interplay to use, could be accessed by way of the community, and will result in full system compromise.
The heap buffer overflow vulnerability might permit attackers who acquire entry to the administration community to probably:
Acquire full management over digital camera techniques
Listen in on surveillance feeds
Manipulate video recordings or stay footage
Use compromised cameras as entry factors to pivot deeper into secured networks
Safety knowledgeable Mathew Marcus, who found the vulnerability, emphasised that whereas attackers want entry to the administration community, many residence and small enterprise deployments lack correct community segmentation, making exploitation comparatively simple in non-segmented environments.
Danger FactorsDetailsAffected ProductsUniFi Shield Cameras (Model 4.75.43 and earlier)ImpactRemote Code Execution (RCE)Exploit PrerequisitesAccess to administration community; no privileges or consumer interplay requiredCVSS 3.1 Score10.0 (Vital)
Mitigation Steps
Ubiquiti strongly urges all UniFi Shield Digital camera customers to instantly replace to firmware model 4.75.62 or later to handle the vulnerability. The replace is obtainable by way of the usual UniFi firmware replace course of.
In the identical safety advisory, Ubiquiti additionally disclosed a second, much less important vulnerability (CVE-2025-23164) affecting the UniFi Shield Software variations 5.3.41 and earlier.
This secondary subject includes a misconfigured entry token mechanism that might permit continued entry to livestream feeds even after hyperlinks have been disabled.
To handle this subject, customers ought to replace the UniFi Shield Software to model 5.3.45 or later.
This isn’t the primary high-severity vulnerability found in Ubiquiti’s UniFi Shield ecosystem in current months. Earlier this 12 months, safety researchers recognized different important flaws, together with CVE-2025-23115 and CVE-2025-23116, which additionally affected the digital camera techniques
Organizations utilizing UniFi Shield cameras implement correct community segmentation as an extra safety measure to restrict the potential impression of such vulnerabilities, even after making use of the required firmware updates.
Setting Up SOC Crew? – Obtain Free Final SIEM Pricing Information (PDF) For Your SOC Crew -> Free Obtain