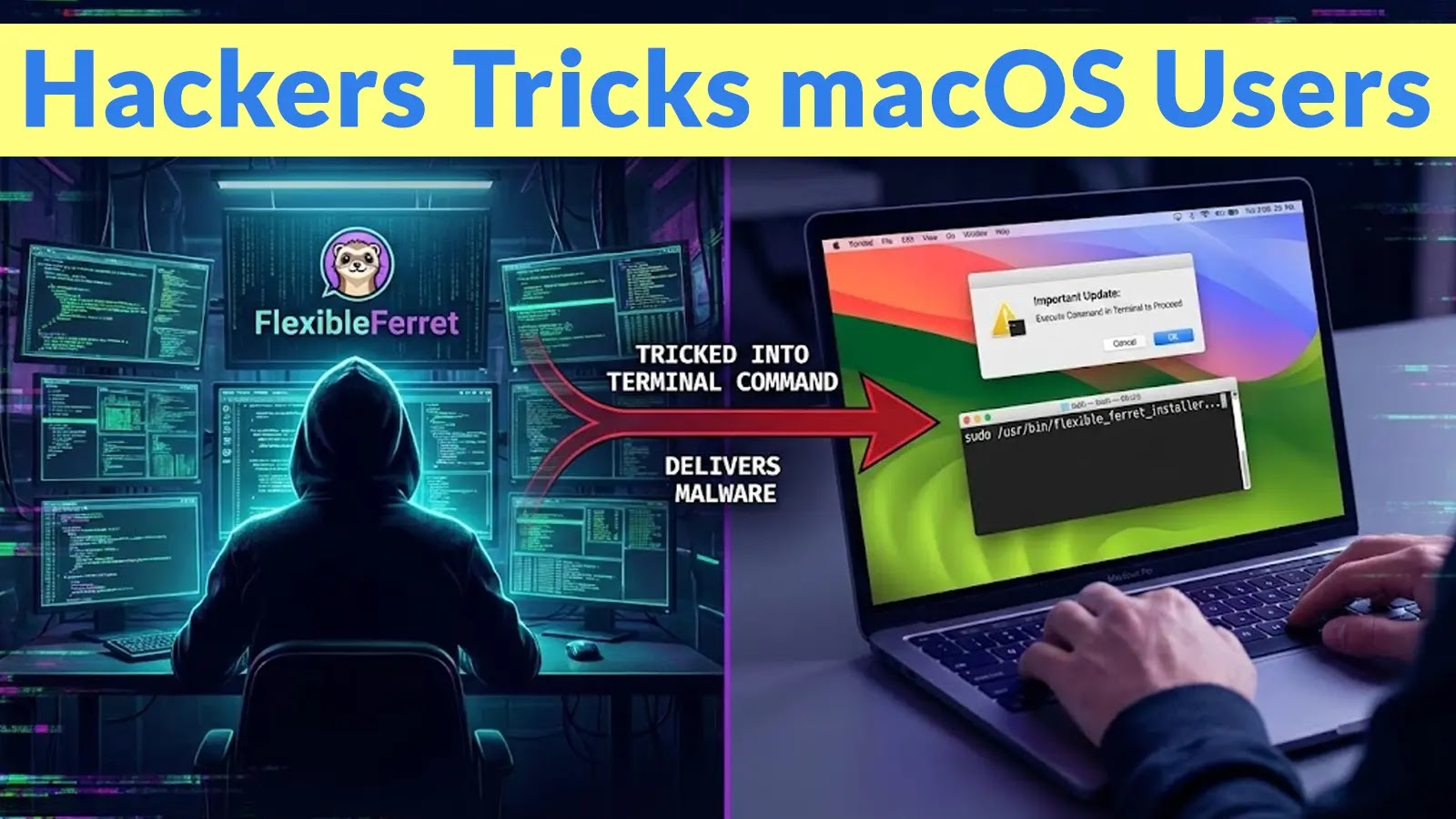
Cybercriminals are efficiently concentrating on Apple customers by a classy social engineering scheme that methods victims into operating dangerous instructions on their computer systems.
The menace, referred to as FlexibleFerret, is attributed to North Korean operators and represents a unbroken evolution of the Contagious Interview marketing campaign that has been energetic all through 2025.
The malware primarily spreads by faux job recruitment web sites that promise employment alternatives however finally ship credential-stealing backdoors and system entry to attackers.
LinkedIn put up highlighting recruitment scams (Supply – Jamf)
The assault begins innocuously with job seekers visiting realistic-looking hiring evaluation web sites like evaluza.com and proficiencycert.com.
Victims full faux job assessments branded with names like “Blockchain Capital Operations Supervisor Hiring Evaluation,” offering private particulars and even recording video introductions.
After finishing these levels, candidates obtain a crucial instruction to run a selected Terminal command, which the attackers declare is required to repair digicam or microphone entry points.
Jamf safety analysts recognized this new variant after discovering in-the-wild detections linked to the script named macpatch.sh.
The researchers discovered JavaScript recordsdata on fraudulent recruitment websites designed to construct and execute curl instructions that obtain malicious payloads on to victims’ computer systems.
An infection mechanism
The an infection mechanism employs a multi-stage supply course of that is still hidden from customers. When the preliminary curl command executes, it downloads a shell script that determines whether or not the sufferer’s Mac makes use of ARM64 or Intel structure, then fetches the suitable stage-two payload.
The script creates working directories in momentary places, establishes persistence by LaunchAgents that robotically launch the malware at login, and shows a convincing faux Chrome software that mimics a official password immediate.
Left – faux Chrome digicam entry immediate, Proper – Chrome-style password immediate (Supply – Jamf)
This decoy software captures no matter credentials customers enter and sends them to a Dropbox account managed by the attackers.
The third stage prompts when a bundled Golang backdoor runs, establishing communication with a command-and-control server.
This subtle element helps a number of operations together with system data assortment, file add and obtain capabilities, command execution, Chrome profile theft, and automatic credential harvesting.
The backdoor maintains persistence by LaunchAgent entries and contains error-handling mechanisms that reset the malware if momentary failures happen.
Organizations ought to educate staff to view unsolicited job evaluation requests and Terminal-based repair directions with excessive suspicion.
Any recruitment communication asking customers to execute system instructions represents a big pink flag and ought to be reported instantly to safety groups.
Comply with us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most popular Supply in Google.