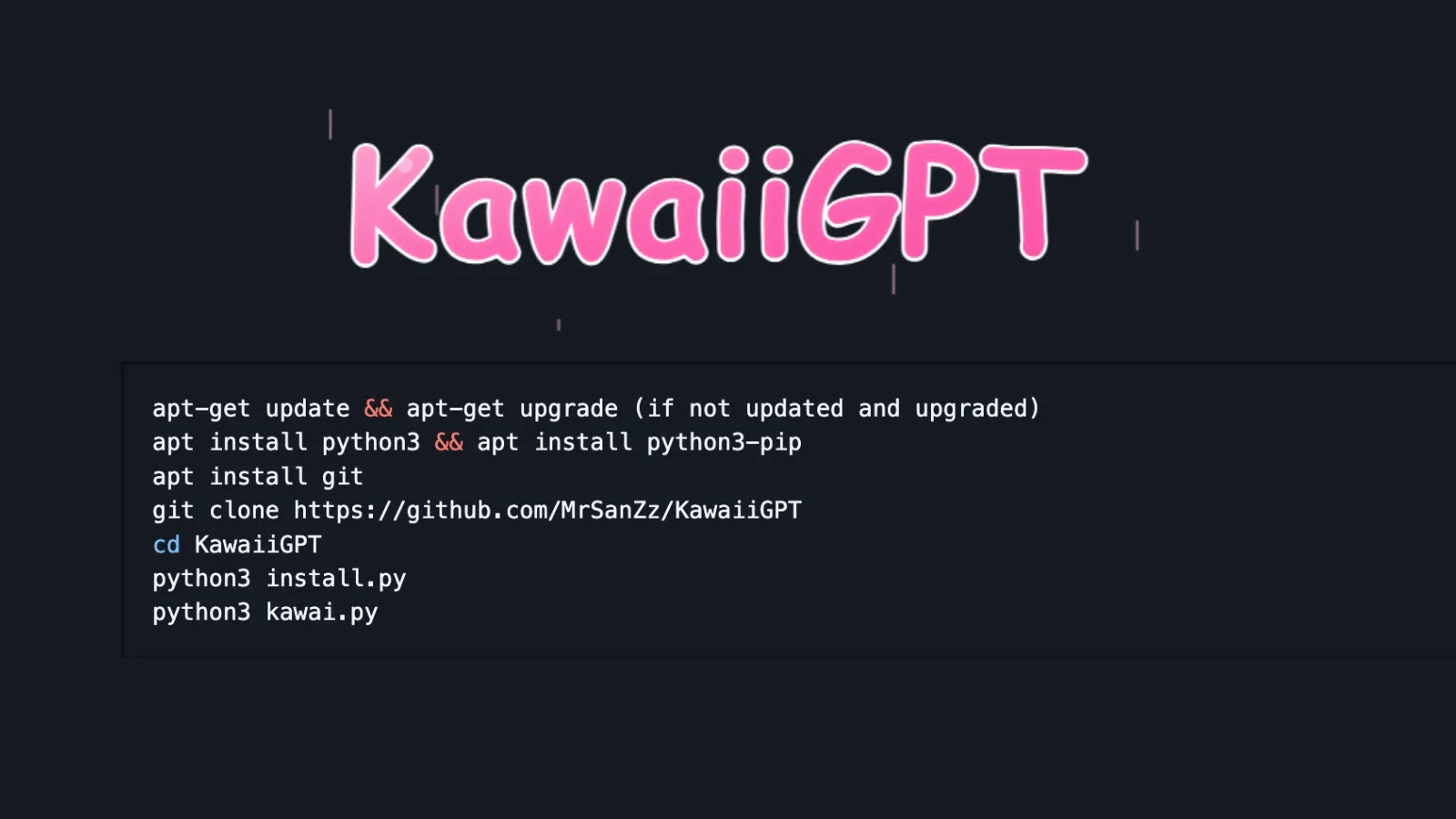
KawaiiGPT emerges as an accessible, open-source instrument that mimics the controversial WormGPT, offering unrestricted AI help through jailbroken giant language fashions. Hosted on GitHub with over 188 stars and 52 forks, it requires no API keys and installs shortly on Linux or Termux environments.
Customers can deploy KawaiiGPT in minutes by updating packages, putting in Python and Git, cloning the repository, and operating easy set up and launch scripts.
Linux distributions use apt-get instructions, whereas Termux customers use pkg equivalents, highlighting its light-weight design for pentesting or informal experimentation. The developer encourages starring the mission for assist and directs queries to a Telegram discussion board.
At its core, KawaiiGPT employs a reverse-engineered API wrapper derived from pollinations brokers, routing queries to backend servers internet hosting fashions like DeepSeek, Gemini, and Kimi-K2.
These integrations allow prompt-injection responses that bypass security guardrails, producing uncensored outputs labeled as “enjoyable” reasonably than malicious. Not like fine-tuned fashions, it depends on ready LLMs with embedded jailbreaks accessible through a assist menu.
Safety researchers spotlight KawaiiGPT’s course of in producing phishing emails, ransomware notes, lateral motion scripts utilizing Paramiko, and knowledge exfiltration instruments.
Its informal “kawaii” persona that includes playful greetings masks potent outputs for social engineering and elemental assaults, decreasing boundaries for novice menace actors. First famous in July 2025 and now at model 2.5, it contrasts paid instruments like WormGPT 4 by providing free, community-driven enhancements.
The codebase’s obfuscation sparks debate, with the creator explaining that it prevents unauthorized repackaging and resale whereas denying the presence of malware, RATs, or spyware and adware. Warnings urge verifying sources to keep away from fakes, and the MIT-licensed mission prohibits modifications for revenue.
A 180-500 member Telegram group shares suggestions, fueling its evolution amid Palo Alto Networks’ alerts on rising cybercrime automation.
Organizations face heightened threats from such instruments, demanding superior electronic mail filters, MFA, EDR, and coaching to counter AI-aided phishing and scripts. Whereas positioned for moral pentesting, KawaiiGPT’s free nature amplifies dangers in an period of dual-use AI.
FeatureKawaiiGPTWormGPT 4CostFree (Open Supply)Paid Subscription (~$50/mo)Underlying TechJailbroken Industrial Fashions (Gemini, DeepSeek)Customized/Tremendous-Tuned ModelAccess MethodPython Script / GitHubDark Internet / Personal ForumPrimary RiskLowers entry barrier for novicesAdvanced, optimized assault scriptsGuardrailsBypassed through Immediate InjectionNatively Uncensored
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.