Nov 27, 2025Ravie LakshmananMalware / Social Engineering
The risk actor referred to as Bloody Wolf has been attributed to a cyber assault marketing campaign that has focused Kyrgyzstan since a minimum of June 2025 with the aim of delivering NetSupport RAT.
As of October 2025, the exercise has expanded to additionally single out Uzbekistan, Group-IB researchers Amirbek Kurbanov and Volen Kayo mentioned in a report printed in collaboration with Ukuk, a state enterprise below the Prosecutor Basic’s workplace of the Kyrgyz Republic. The assaults have focused finance, authorities, and knowledge expertise (IT) sectors.
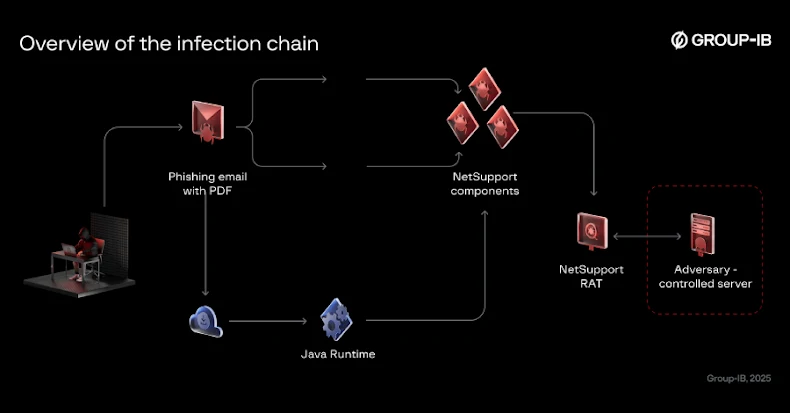
“These risk actors would impersonate the [Kyrgyzstan’s] Ministry of Justice by official wanting PDF paperwork and domains, which in flip hosted malicious Java Archive (JAR) recordsdata designed to deploy the NetSupport RAT,” the Singapore-headquartered firm mentioned.
“This mixture of social engineering and accessible tooling permits Bloody Wolf to stay efficient whereas preserving a low operational profile.”
Bloody Wolf is the identify assigned to a hacking group of unknown provenance that has used spear-phishing assaults to focus on entities in Kazakhstan and Russia utilizing instruments like STRRAT and NetSupport. The group is assessed to be energetic since a minimum of late 2023.
The focusing on of Kyrgyzstan and Uzbekistan utilizing related preliminary entry strategies marks an enlargement of the risk actor’s operations in Central Asia, primarily impersonating trusted authorities ministries in phishing emails to distribute weaponized hyperlinks or attachments.
The assault chains kind of observe the identical method in that the message recipients are tricked into clicking on hyperlinks that obtain malicious Java archive (JAR) loader recordsdata together with directions to put in Java Runtime.
Whereas the e-mail claims the set up is important to view the paperwork, the truth is that it is used to execute the loader. As soon as launched, the loader then proceeds to fetch the next-stage payload (i.e., NetSupport RAT) from infrastructure that is below the attacker’s management and arrange persistence in 3 ways –
Making a scheduled process
Including a Home windows Registry worth
Dropping a batch script to the folder “%APPDATApercentMicrosoftWindowsStart MenuProgramsStartup”
The Uzbekistan part of the marketing campaign is notable for incorporating geofencing restrictions, thereby inflicting requests originating outdoors of the nation to be redirected to the reputable knowledge.egov[.]uz web site. Requests from inside Uzbekistan have been discovered to set off the obtain of the JAR file from an embedded hyperlink throughout the PDF attachment.
Group-IB mentioned the JAR loaders noticed within the campaigns are constructed with Java 8, which was launched in March 2014. It is believed that the attackers are utilizing a bespoke JAR generator or template to spawn these artifacts. The NetSupport RAT payload is a previous model of NetSupport Supervisor from October 2013.
“Bloody Wolf has demonstrated how low-cost, commercially out there instruments will be weaponized into subtle, regionally focused cyber operations,” it mentioned. “By exploiting belief in authorities establishments and leveraging easy JAR-based loaders, the group continues to keep up a robust foothold throughout the Central Asian risk panorama.”