A complicated, advanced new cyber offensive has emerged from the “Scattered Lapsus$ Hunters,” a risk collective that has aggressively shifted towards exploiting supply-chain vulnerabilities.
This newest marketing campaign targets Zendesk, a vital buyer assist platform, successfully turning a trusted enterprise device right into a launchpad for company spying.
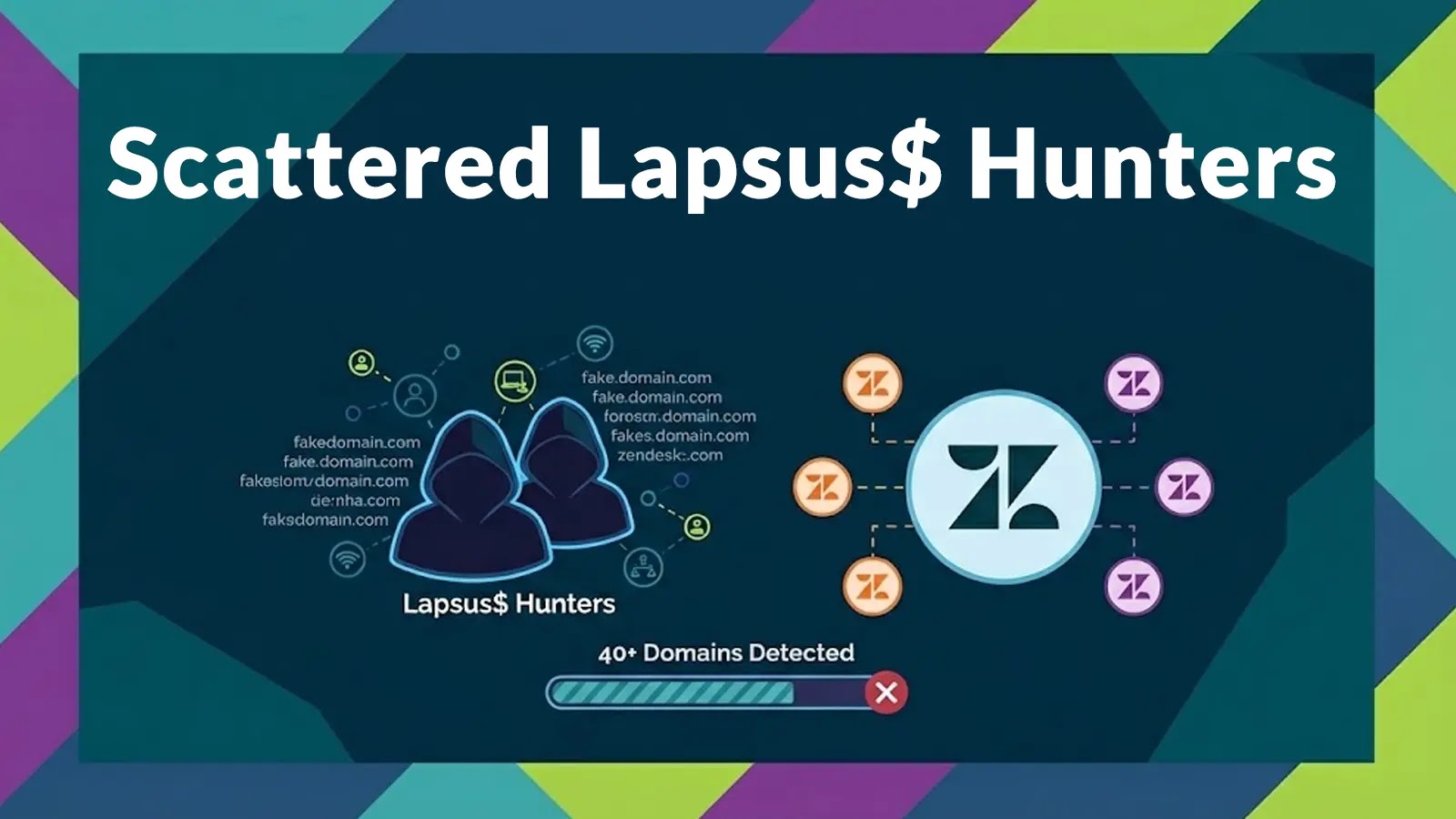
The attackers have efficiently registered over 40 typosquatted domains, together with misleading examples like znedesk[.]com and vpn-zendesk[.]com.
These websites are meticulously designed to imitate official login environments, internet hosting fraudulent Single Signal-On (SSO) portals that seize credentials from unsuspecting customers.
The marketing campaign’s infrastructure reveals a coordinated effort to bypass customary detection protocols. The domains had been constantly registered via NiceNic and use Cloudflare-masked nameservers to cover their true internet hosting origins.
By utilizing these hiding methods, the actors guarantee their phishing pages stay lively lengthy sufficient to reap vital volumes of high-privilege credentials earlier than defenders can react.
This demonstrates a transparent, strategic evolution of their capabilities, permitting them to keep up operational secrecy whereas concentrating on widespread platforms utilized by world enterprises.
The impression of this focused method extends far past easy credential theft. Reliaquest safety analysts recognized the malware and famous that the marketing campaign shares distinct area registry traits with the group’s earlier assaults on Salesforce in August 2025.
As soon as attackers bypass the preliminary authentication layer, they set up a persistent foothold that facilitates lateral motion throughout the company community.
This entry permits them to steal extremely delicate buyer information, together with billing data and authorities IDs, mirroring the huge information theft seen of their September 2025 breach of Discord.
Weaponizing Help Tickets
The group’s most harmful tactic entails the direct weaponization of official assist tickets to bypass conventional perimeter defenses.
As a substitute of relying solely on exterior phishing emails, they submit fraudulent tickets immediately into a corporation’s Zendesk portal.
These tickets sometimes masquerade as pressing system administration requests or password reset inquiries, making a fabricated sense of urgency that compels assist brokers to behave with out verification.
Embedded inside these tickets are hyperlinks to the typosquatted domains or malicious payloads designed to compromise the endpoint.
When a help-desk worker interacts with the ticket, they by chance set off the obtain of Distant Entry Trojans (RATs).
This grants the attackers persistent distant management, permitting them to execute instructions and monitor exercise.
Scattered Lapsus$ Hunters Telegram submit (Supply – Reliaquest)
The group has openly boasted about these advanced operations, particularly warning incident response groups to look at their logs carefully as they put together to gather important buyer databases via the upcoming 2026 vacation season.
Comply with us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most well-liked Supply in Google.