Nov 28, 2025Ravie LakshmananMalware / Vulnerability
Cybersecurity researchers have found weak code in legacy Python packages that would doubtlessly pave the best way for a provide chain compromise on the Python Package deal Index (PyPI) by way of a website takeover assault.
Software program provide chain safety firm ReversingLabs stated it discovered the “vulnerability” in bootstrap recordsdata offered by a construct and deployment automation software named “zc.buildout.”
“The scripts automate the method of downloading, constructing, and putting in the required libraries and instruments,” safety researcher Vladimir Pezo stated. “Particularly, when the bootstrap script is executed, it fetches and executes an set up script for the package deal Distribute from python-distribute[.]org – a legacy area that’s now obtainable on the market within the premium worth vary whereas being managed to drive advert income.”
The PyPI packages that embrace a bootstrap script that accesses the area in query embrace twister, pypiserver, slapos.core, roman, xlutils, and testfixtures.
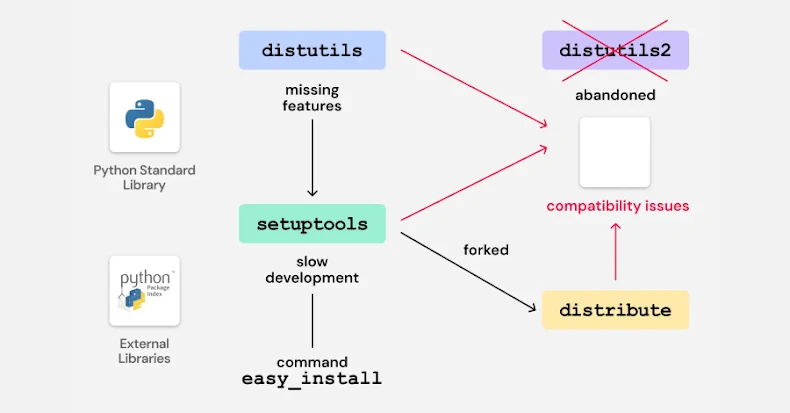
The crux of the issue considerations an previous bootstrap script (“bootstrap.py”) that was used together with the zc.buildout software to initialize the Buildout setting. The Python script additionally supported the flexibility to put in a packaging utility referred to as “Distribute,” a short-lived fork of the Setuptools challenge, into the native setting.
To attain this, the Distribute set up script (“distribute_setup.py”) is fetched from the python-distribute[.]org, a website that has been up on the market since 2014. In including the choice, the concept was to instruct the bootstrap script to obtain and set up the Distribute package deal as a substitute of the older Setuptools package deal to handle eggs and dependencies for the buildout.
It is vital to notice that the Distribute fork got here into being as a result of lack of lively growth of Setuptools, the principle package deal administration software used at the moment. Nevertheless, the options from Distribute have been built-in again into Setuptools in 2013, rendering Distribute out of date.
The problem recognized by ReversingLabs considerations the truth that many packages have continued to ship the bootstrap script that both makes an attempt to put in Distribute by default or when the command-line choice (“-d” or “–distribute”) is specified. This, coupled with the truth that the area in query is up for grabs, places customers at latent danger as an attacker may weaponize this setup to serve malicious code when the bootstrap script is inadvertently run and doubtlessly steal delicate information.
Whereas among the affected packages have taken steps to take away the bootstrap script, the slapos.core package deal nonetheless continues to ship the weak code. It is also included within the growth and upkeep model of Twister.
One other vital facet to contemplate right here is that the bootstrap script is just not executed routinely throughout the package deal set up and is written in Python 2. This implies the script can’t be executed with Python 3 with out modifications. However the mere presence of the file leaves an “pointless assault floor” that attackers can exploit if builders are tricked into working code that triggers the execution of the bootstrap script.
The specter of a website takeover is just not theoretical. In 2023, it got here to mild that the npm package deal fsevents was compromised by a nasty actor who seized management of an unclaimed cloud useful resource hosted at fsevents-binaries.s3-us-west-2.amazonaws[.]com to push malicious executables to customers putting in sure variations of the package deal (CVE-2023-45311, CVSS rating: 9.8).
“The problem lies within the programming sample that features fetching and executing a payload from a hard-coded area, which is a sample generally noticed in malware exhibiting downloader habits,” Pezo stated. “The failure to formally decommission the Distribute module allowed weak bootstrap scripts to linger and left unknown numbers of initiatives uncovered to a possible assault.”
The disclosure comes as HelixGuard found a malicious package deal in PyPI named “spellcheckers” that claims to be a software for checking spelling errors utilizing OpenAI Imaginative and prescient, however comprises malicious code that is designed to connect with an exterior server and obtain a next-stage payload, which then executes a distant entry trojan (RAT).
The package deal, first uploaded to PyPI on November 15, 2025, by a person named leo636722, has been downloaded 955 occasions. It is now not obtainable for obtain.
“This RAT can obtain distant instructions and execute attacker-controlled Python code by way of exec(), enabling full distant management over the sufferer’s host,” HelixGuard stated. “When the person installs and runs the malicious package deal, the backdoor turns into lively, permitting the attacker to remotely management the person’s pc.”