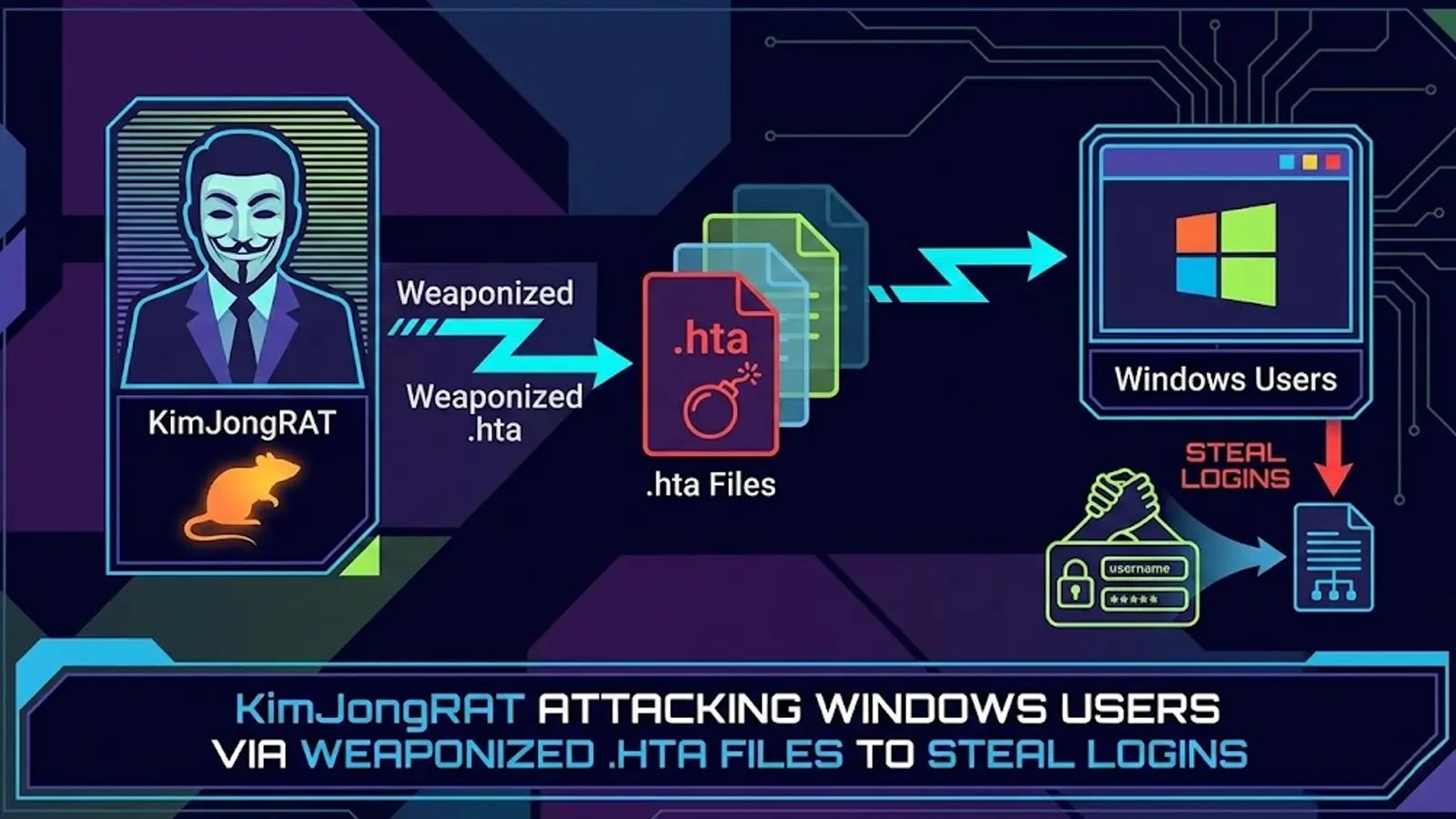
A brand new distant entry trojan dubbed KimJongRAT has surfaced, posing a extreme menace to Home windows customers.
This refined malware is believed to be orchestrated by the Kimsuky group, a menace actor with alleged state backing.
The marketing campaign usually begins with a phishing e-mail containing a misleading archive named Nationwide Tax Discover, which lures unsuspecting victims into initiating the an infection chain.
Upon opening the malicious archive, customers are introduced with a shortcut file disguised as a professional PDF doc.
Tax discover.pdf (Supply – Alyac)
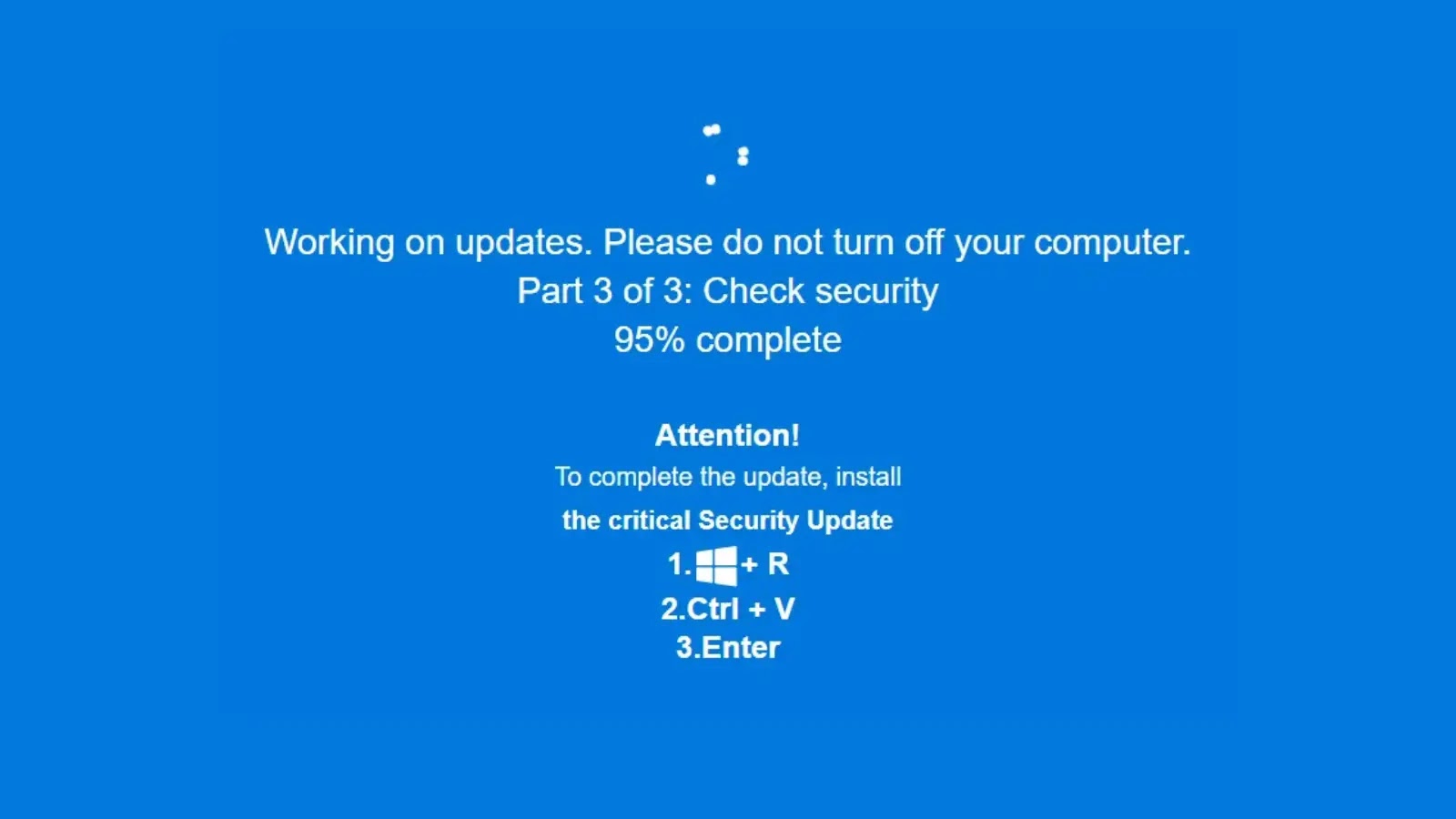
When executed, this shortcut file triggers a hidden command that decodes a Base64 URL and abuses the professional Microsoft HTML Utility utility to contact a distant server.
This course of stealthily downloads a further payload often known as tax.hta, successfully bypassing normal safety checks.
Alyac safety analysts recognized that this loader script is applied in VBScript and employs intelligent evasion methods.
The malware makes an attempt to evade detection by using professional providers like Google Drive to host its malicious parts.
As soon as lively, the loader retrieves each decoy paperwork to trick the person and the precise malicious binaries required for the subsequent stage of the assault.
Exfiltration of delicate information
The first goal of this marketing campaign is the exfiltration of delicate private and monetary information.
The malware targets a wide selection of knowledge, together with system particulars, browser storage information, and encryption keys.
It particularly hunts for cryptocurrency pockets data and credentials for communication platforms like Telegram and Discord, making it a extremely harmful device for identification theft and monetary fraud.
Probably the most notable facet of KimJongRAT is its means to adapt its habits based mostly on the goal setting’s safety posture.
The malware executes a selected VBScript command to verify the standing of Home windows Defender earlier than continuing.
It makes use of the code snippet Set exec = oShell.Exec(ss) adopted by If InStr(output, “STOPPED”) > 0 Then to find out if the safety service is lively.
If Home windows Defender is disabled, the malware downloads a file named v3.log, which executes the first payload.
Conversely, if safety is lively, it retrieves another file referred to as pipe.log to avoid detection.
Whatever the path taken, the malware establishes persistence by registering itself within the system registry, guaranteeing it runs routinely to transmit stolen information periodically.
Record of cryptocurrency wallets hijacked by malware (Supply – Alyac)
Whereas the Record of cryptocurrency wallets hijacked by malware highlights the breadth of focused functions, it additionally highlights the precise monetary intent behind this tailor-made menace.
Observe us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most well-liked Supply in Google.