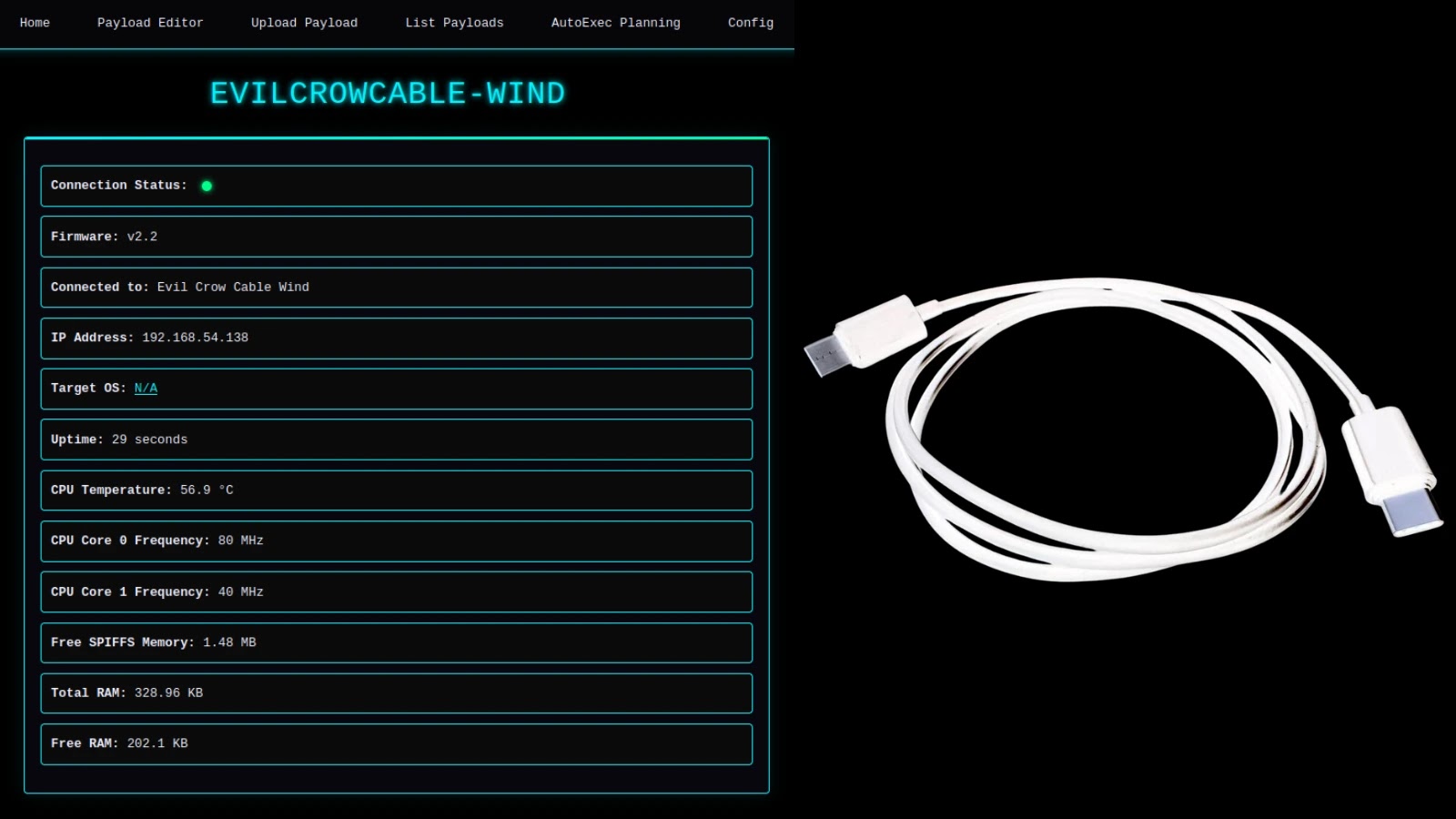
The Evil Crow Cable Wind is a stealthy instrument for pink teamers that hides a strong hacking implant inside what seems to be a normal USB charging cable.
Designed by safety researcher Joel Serna Moreno, this system features as a Human Interface Machine (HID) able to executing automated keystroke assaults at speeds of as much as 1,000 characters per minute.
Not like conventional BadUSB instruments that require pre-configured scripts, the Evil Crow Cable Wind integrates an ESP32-S3 chip, permitting attackers to manage the system remotely through Wi-Fi by means of a web-based interface.
This particular mannequin follows the lineage of high-end espionage instruments just like the NSA’s $20,000 COTTONMOUTH-I implant, however makes related capabilities obtainable to penetration testers for roughly $43.
The defining function of the Evil Crow Cable Wind is its wi-fi administration, with out putting in specialised software program or cell functions.
Customers can connect with the cable’s Wi-Fi hotspot and entry a browser-based dashboard to deploy payloads, handle configurations, or replace firmware over the air.
This internet interface features a reside payload editor with syntax highlighting and an “AutoExec” function that robotically runs particular scripts when the cable is plugged right into a goal system.
The {hardware} is flexible, obtainable in each USB-A to USB-C and USB-C to USB-C configurations, making it suitable with a broad vary of recent laptops and smartphones.
Superior Options: OS Detection and Distant Shell
In response to Cellular-hacker evaluation, Past easy keystroke injection, the EvilCrow CableWind presents refined reconnaissance and management options.
The system can detect the working system of the host machine, figuring out Home windows, macOS, Linux, or Android, and conditionally execute payloads tailor-made to that particular surroundings.
Moreover, the instrument helps a “Distant Shell” functionality that establishes a serial connection between the goal and the attacker’s interface.
This enables pink teamers to execute system instructions on air-gapped machines that lack web entry, bridging the hole between bodily entry and distant execution, Joel Serna Moreno added.
When positioned alongside opponents just like the O.MG Cable and USB Ninja, the Evil Crow Cable Wind positions itself as an economical open-source different that prioritizes important performance over premium stealth options.
Whereas the O.MG Cable Elite presents superior capabilities like {hardware} keylogging and geo-fencing, it prices considerably extra. Conversely, the USB Ninja presents a stealthy design however lacks the dynamic web-based management present in Serna Moreno’s creation.
The next desk outlines the important thing variations between these standard {hardware} implants.
FeatureEvil Crow Cable WindUSB NinjaO.MG Cable (Elite)Worth~$43~$161$150–$180Control MechanismWi-Fi (Net Interface)RF RemoteWi-Fi, AppPayload EditingWeb-based (Reside)NoneWeb-basedOS DetectionYesNoYesRemote ShellYesNoYesKeyloggerNoNoYesOpen SourceYesNoNoComparison desk (Supply: Cellular-hacker)
The Evil Crow Cable Wind represents a major evolution in accessible bodily safety testing instruments. By combining the benefit of Wi-Fi management with highly effective options like OS detection and air-gap bridging, it presents a strong answer for safety professionals simulating insider threats.
Though it lacks the {hardware} keylogging present in costlier alternate options, its open-source nature and assist for customized firmware such because the USB Military Knife undertaking guarantee it stays a versatile and adaptable asset for pink staff operations.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.