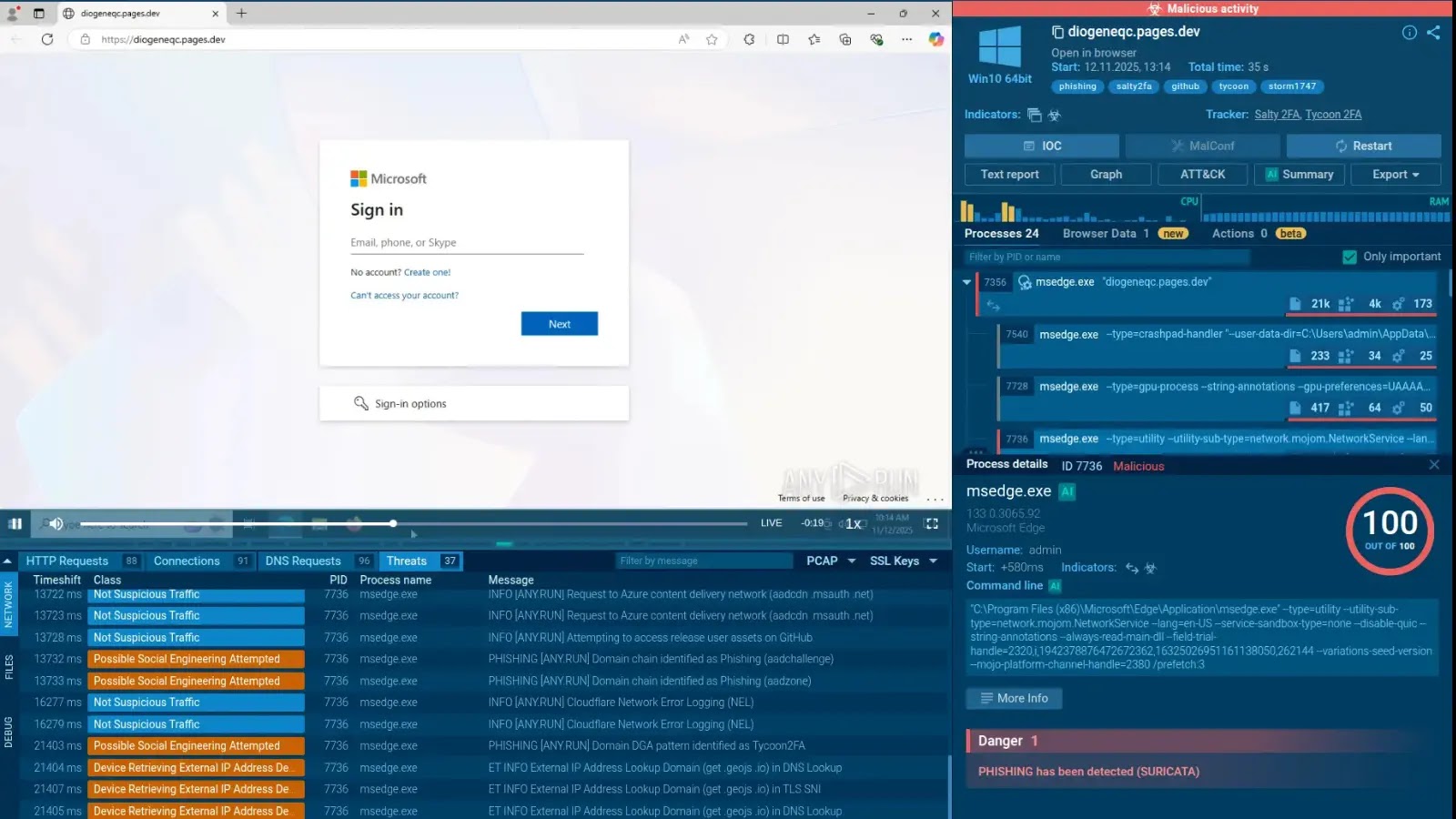
A brand new kind of phishing assault that mixes two totally different phishing kits: Salty2FA and Tycoon2FA. This marks a major change within the Phishing-as-a-Service (PhaaS) panorama.
Whereas phishing kits sometimes preserve distinctive signatures of their code and supply mechanisms, latest campaigns concentrating on enterprise customers have begun deploying payloads that mix parts from each frameworks.
This convergence complicates attribution efforts and suggests a possible operational merger or collaboration between the menace actors behind these subtle instruments.
The Collapse of Salty2FA
The invention follows a dramatic decline in standalone Salty2FA exercise noticed in late 2025, in keeping with an evaluation by ANY.RUN, submissions of Salty2FA samples to their interactive sandbox dropped precipitously from lots of of weekly uploads to fewer than 50 by early November.
Coinciding with this drop, analysts detected a wave of “hybrid” samples the place Salty2FA’s infrastructure appeared to fail, triggering a fallback mechanism that retrieved Tycoon2FA payloads as a substitute.
Code-level evaluation by ANY.RUN revealed that these hybrid payloads start with Salty2FA’s conventional “trampoline” scripts, which load the following stage of the assault.
Nonetheless, when the first Salty2FA domains didn’t resolve (returning DNS SERVFAIL errors), the scripts executed a hardcoded fallback command, fetching malicious content material from Tycoon2FA infrastructure.
This seamless handoff signifies that the operators anticipated infrastructure instability and engineered a redundancy utilizing a rival or accomplice equipment.
The overlap in techniques, methods, and procedures (TTPs) strengthens the speculation that each kits could also be operated by the identical menace group, tracked by Microsoft as Storm-1747.
Storm-1747 has lengthy been related to Tycoon2FA, a equipment recognized for bypassing multifactor authentication (MFA) by way of adversary-in-the-middle (AiTM) methods.
The newly noticed hybrid samples replicate Tycoon2FA’s execution chain virtually line-for-line of their later levels, together with particular variable naming conventions and knowledge encryption strategies.
This structural similarity means that Salty2FA might not be an impartial competitor however relatively one other software in Storm-1747’s arsenal, probably used for various concentrating on profiles or as a testing floor for brand spanking new evasion options.
For safety operations facilities (SOCs), the blurring of strains between Salty2FA and Tycoon2FA requires an up to date protection technique. Reliance on static indicators of compromise (IOCs) for a single equipment is not ample, as a marketing campaign may pivot from one framework to a different mid-execution.
Specialists advocate treating these kits as a single menace cluster. Defenders ought to correlate alerts involving Salty2FA’s preliminary supply vectors, reminiscent of HTML trampoline recordsdata, with Tycoon2FA’s recognized community behaviors, together with visitors to DGA-generated domains and fast-flux infrastructure.
By unifying detection logic for each households, organizations can higher detect these resilient, multi-stage assaults earlier than credentials are stolen.
Detect phishing threats in below 60 seconds with ANY.RUN’s Sandbox in your SOC => Join now