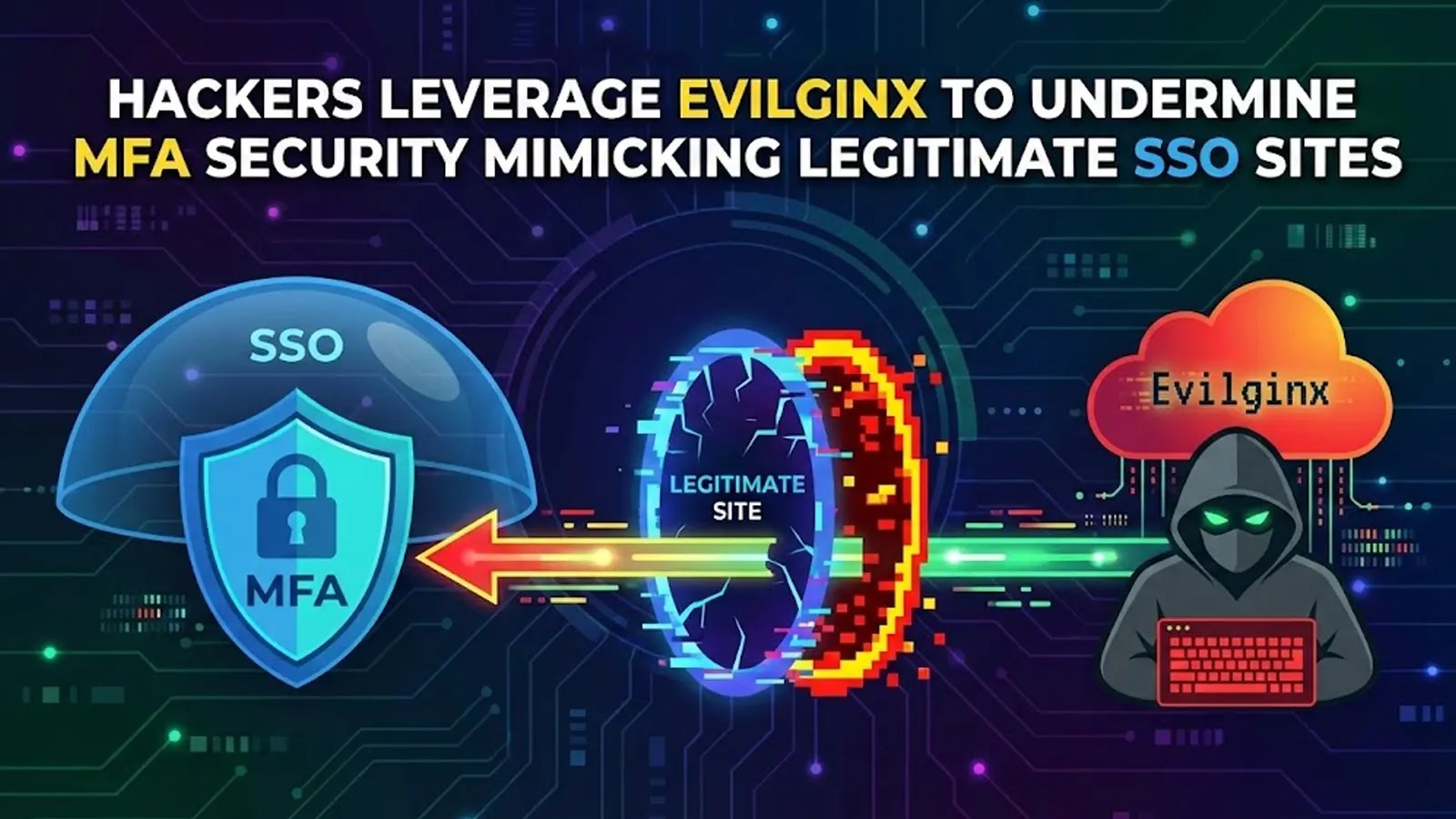
Hackers are turning to Evilginx, a robust adversary-in-the-middle device, to get round multi-factor authentication and take over cloud accounts.
The framework acts as a reverse proxy between the sufferer and actual single sign-on pages, so the login display screen seems and behaves identical to the true factor.
To the person, the pretend website feels regular, with legitimate TLS and acquainted branding. Attackers begin with focused phishing emails that push victims to rigorously crafted pretend SSO portals.
These pages copy the format, scripts, and flows of widespread id platforms, together with enterprise SSO gateways. As soon as the person enters credentials and completes MFA, Evilginx quietly captures session cookies and tokens whereas nonetheless passing site visitors to the true supplier.
This reveals the staged relay from the sufferer to the id supplier. Infoblox safety analysts recognized latest campaigns the place Evilginx was used to imitate legit company SSO websites and steal tokens for e mail and collaboration platforms.
A timeline of SSO phishing assaults towards increased academic establishments (Supply – Infoblox)
They famous that the stolen cookies permit attackers to replay periods with out ever needing passwords or MFA codes once more. This shifts the danger from basic credential theft to full session hijack.
The influence is severe for each corporations and customers. With an energetic session token, attackers can learn mail, reset passwords on linked apps, deploy new MFA strategies, and plant backdoor entry.
Assault evaluation
This will result in enterprise e mail compromise, knowledge theft, and long-term stealth entry that’s laborious to hint again to the primary phishing click on. In distinction, the assault circulation reveals how stolen cookies unlock downstream providers.
Assault circulation (Supply – Infoblox)
One key focus within the full technical breakdown is how Evilginx evades detection throughout this course of.
The framework forwards all content material from the true SSO website, together with scripts, types, and dynamic prompts, which makes conventional visible checks virtually ineffective.
It additionally makes use of actual certificates on lookalike domains, so browser padlocks nonetheless seem inexperienced and reassuring.
Underneath the hood, Evilginx proxies and rewrites headers to maintain the session alive whereas stripping out delicate cookies for theft.
A easy, high-level phishlet can appear like:-
server_name login.instance.com;
proxy_pass
proxy_set_header Host login.real-sso.com;
By logging cookies on the proxy layer, attackers seize session knowledge earlier than it’s protected by the person’s system or company instruments.
Universities focused by the Evilginx actor (Supply – Infoblox)
This reveals how headers and cookies circulation by way of the proxy, highlighting the factors the place tokens are intercepted.
Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most popular Supply in Google.