Russian-backed risk actors proceed their refined cyber espionage operations in opposition to Western establishments via superior phishing ways.
Calisto, a Russia-nexus intrusion set attributed to the Russian FSB’s Middle 18 for Info Safety (navy unit 64829), has emerged as a persistent risk concentrating on NATO analysis entities and strategic organizations.
The group has expanded its assault scope to incorporate NGOs and suppose tanks, specializing in nations supporting Ukraine and Japanese European nations.
The malware campaigns leverage social engineering strategies paired with the ClickFix methodology, a social engineering tactic that manipulates customers into taking actions that compromise safety.
These assaults function via fastidiously crafted spear-phishing emails that impersonate trusted contacts, utilizing psychological manipulation to lure victims into downloading malicious information or visiting compromised infrastructure.
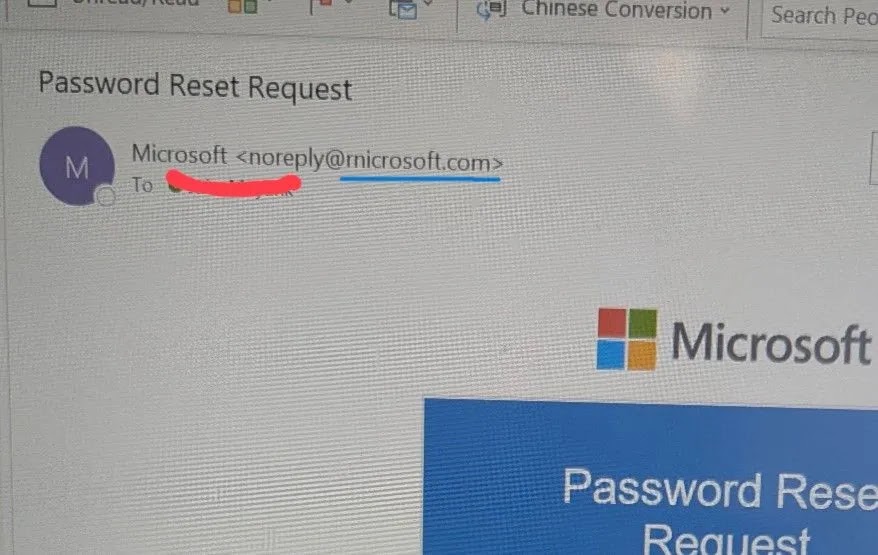
Phishing electronic mail in opposition to reporters (Supply – Sekoia)
Sekoia safety analysts recognized the malware after observing coordinated assaults in opposition to high-value targets.
The group employed decoy emails with lacking attachments or damaged PDF information, prompting victims to request resends.
Calisto PDFs resulting in phishing webpages (Supply – Sekoia)
As soon as engaged in correspondence, attackers ship malicious payloads via redirected hyperlinks hosted on compromised web sites.
This multi-stage method will increase credibility whereas sustaining operational safety. The technical infrastructure reveals refined assault chains.
Phishing redirectors make the most of PHP scripts deployed on compromised servers, accepting token parameters via GET requests resembling commonplace monitoring codes.
Upon activation, malicious JavaScript redirects customers to credential harvesting portals. The customized phishing package, hosted on account.simpleasip[.]org, particularly targets ProtonMail accounts via an Adversary-in-the-Center method.
Calisto phishing package for Protonmail (Supply – Sekoia)
The interface injects malicious JavaScript code that maintains compelled cursor give attention to password fields each 250 milliseconds, stopping consumer navigation.
When customers enter credentials, the injected code interacts with attacker-controlled APIs positioned on scorelikelygateway.simLeasip[.]org, relaying authentication knowledge whereas presenting legitimate-appearing CAPTCHA and two-factor authentication prompts to keep up the deception.
An infection Mechanism and Persistence Techniques
Upon profitable credential seize, the phishing package makes an attempt to fetch legitimate endpoints from ProtonMail’s infrastructure to keep up operational look.
The attackers make the most of proxy companies, with logs revealing entry from IP tackle 196.44.117[.]196 related to the Large Mama Proxy service. The infrastructure evaluation demonstrates persistent evolution of assault patterns.
Calisto registers domains via a number of registrars, initially utilizing Regway earlier than transitioning to Namecheap’s free and commonplace authoritative servers, enabling risk intelligence analysts to trace and correlate assault campaigns with medium confidence.
Regardless of in depth public disclosures, Calisto continues increasing phishing operations concentrating on Ukraine supporters. Organizations concerned in humanitarian work, press freedom advocacy, and strategic analysis stay main targets aligned with Russian intelligence priorities.
Observe us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most popular Supply in Google.