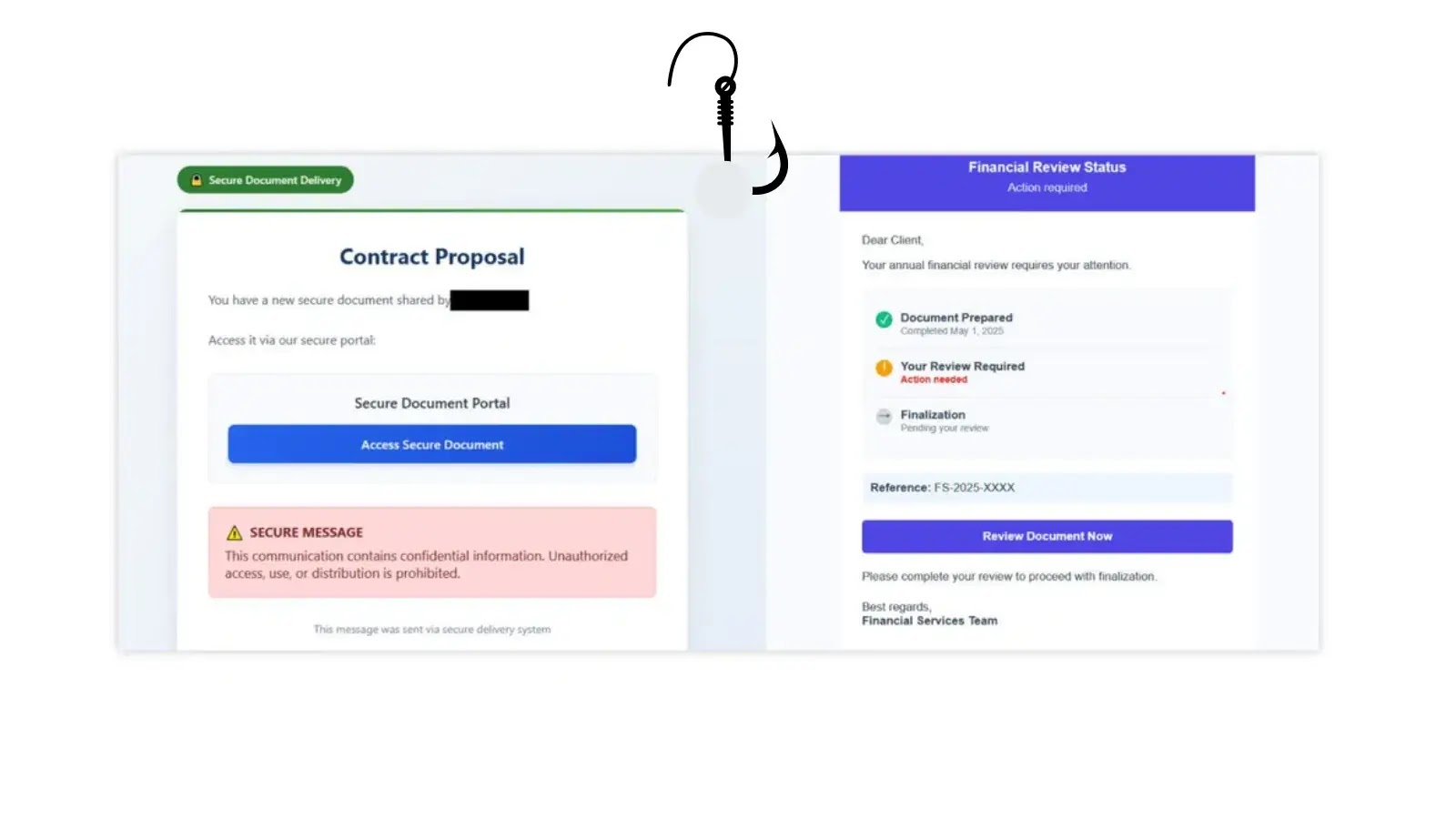
A classy new phishing equipment known as GhostFrame has already been used to launch over 1 million assaults.
First found in September 2025 by Safety researchers at Barracuda, this stealthy instrument represents a harmful evolution in phishing-as-a-service know-how.
What makes GhostFrame significantly regarding is its simplicity mixed with effectiveness.
Not like conventional phishing kits, GhostFrame makes use of an innocent-looking HTML file that conceals all malicious exercise inside an invisible iframe. This small window masses content material from one other supply.
The phishing electronic mail
This method makes the assault extraordinarily tough for safety instruments to detect.
How the Assault Works
The equipment operates in two levels. First, victims obtain phishing emails with misleading topic traces like “Safe Contract & Proposal Notification” or “Password Reset Request.”
When customers click on the hyperlink, they land on what seems to be a innocent webpage.
Hidden beneath the floor, an iframe masses the precise phishing content material from a continually altering subdomain.
To additional evade detection, attackers create a singular subdomain for every goal.
The equipment additionally contains anti-analysis options that block right-clicking, stop keyboard shortcuts, and switch off developer instruments, making it practically inconceivable for safety analysts or curious customers to examine the web page.
mouse clicks and principal context menu entry
GhostFrame contains a number of refined options. The phishing type is hid inside an image-streaming operate designed for big recordsdata, bypassing customary safety scanners that search for conventional login types.
The equipment can rotate subdomains throughout an energetic session and contains backup iframes in case JavaScript is blocked.
Particular options of the GhostFrame phishing equipment
Attackers can simply swap phishing content material with out altering the principle webpage, enabling them to focus on a number of areas or organizations concurrently.
The equipment even mimics legit providers by altering web page titles and favicons to look genuine. Barracuda specialists suggest a multi-layered protection technique.
Organizations ought to implement common browser updates, deploy electronic mail safety gateways that detect suspicious iFrames, and implement controls to limit iframe utilization on web sites.
Worker coaching stays vital; employees should confirm URLs earlier than coming into credentials and report suspicious embedded content material.
As GhostFrame continues to unfold globally, staying vigilant and implementing complete electronic mail safety options are important to defending customers from this evolving risk.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.